Four newly discovered vulnerabilities have been identified in one of Windows’ core components—the Task Scheduler—enabling local privilege escalation attacks. Research indicates that adversaries can not only gain administrative privileges but also erase traces of their activity by tampering with event logs.
The flaws center around the binary file “schtasks.exe”, which is used to manage tasks both locally and remotely. Experts found critical flaws in its operation that could allow attackers to bypass standard protection mechanisms, including User Account Control (UAC).
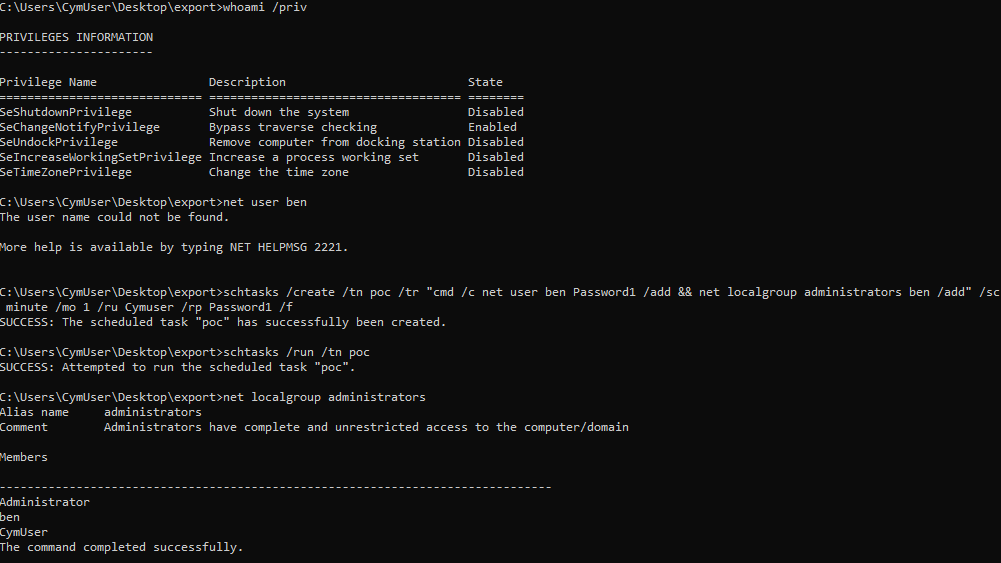
According to Cymulate, one of the vulnerabilities allows processes to be launched under the SYSTEM account without requiring user confirmation. This is achieved through the creation of a task using the Batch Logon method—where a password, rather than an interactive token, is used for authentication. Such tasks run with the highest possible privileges, making them ideal for executing malicious scripts.
However, the key prerequisite for exploitation is possession of a valid password for the target account. This can be obtained, for instance, through the interception and decryption of NTLMv2 hashes during SMB authentication, or by leveraging other vulnerabilities such as CVE-2023-21726.
With a valid password, even a low-privileged account can impersonate an administrator, backup operator, or performance log user. This is done using the standard Windows utility with the /ru and /rp flags to specify username and password credentials.
Particular attention was given to techniques for obfuscating traces. Researchers demonstrated how an XML task file can be used to craft an author name exceeding 3,500 characters, which results in a log description overflow, effectively erasing prior activity records. Another technique targets the Security Event Log database located at C:\Windows\System32\winevt\logs\Security.evtx, enabling its corruption and the destruction of critical audit records.
As such, the Task Scheduler becomes not merely a tool for task automation but a powerful attack vector capable of granting the highest levels of access. It is available to all users and controlled by a service that runs under SYSTEM privileges, offering extensive opportunities for manipulating privileges, process integrity, and impersonation mechanisms.
This research underscores how underestimated built-in system utilities can be in the broader security landscape. A seemingly benign command-line tool can become a backdoor, bypassing access controls, elevating privileges, and wiping digital footprints.
Despite the technical depth and significant risks outlined in the report, Microsoft has not acknowledged any of the findings submitted to the MSRC as official vulnerabilities. Consequently, no updates or mitigations for “schtasks.exe” are currently planned, leaving the described techniques viable for local exploitation.


