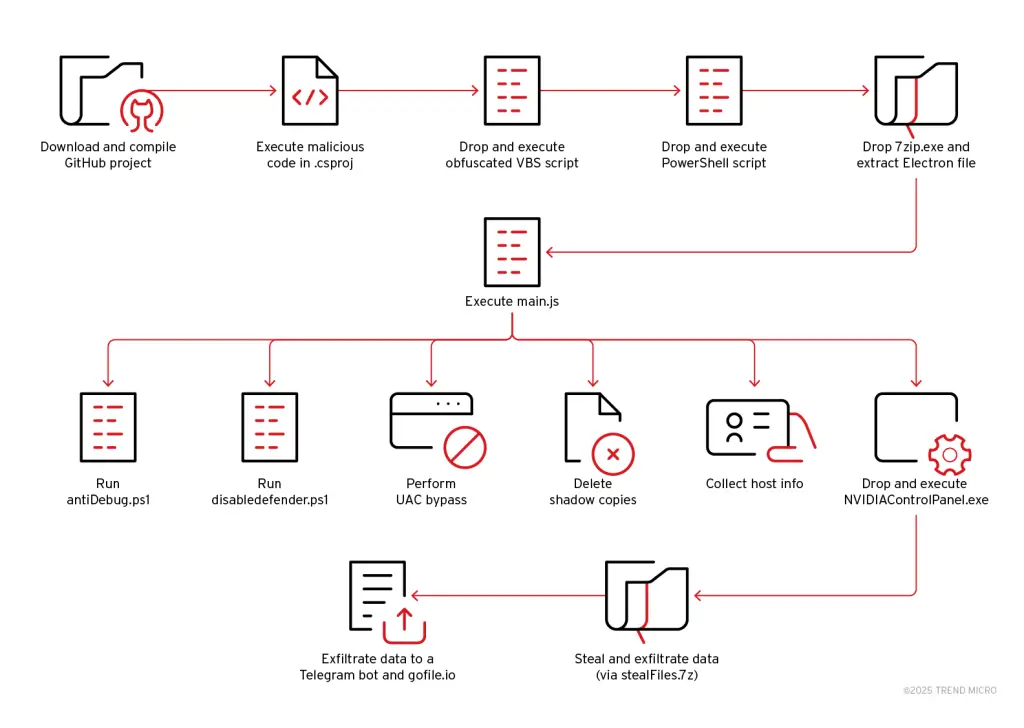
A new actor has emerged within cyberspace—Water Curse, a threat group that since March 2023 has been orchestrating a covert yet expansive campaign to disseminate sophisticated malware through counterfeit repositories on GitHub. According to experts at Trend Micro, the group’s operations are marked by a high degree of automation, a diverse arsenal of tools, and a focused strategy targeting supply chains, including software developers, system administrators, and cybersecurity professionals.
To lure victims, the attackers created repositories masquerading as legitimate pentesting utilities. In reality, these Visual Studio projects harbored concealed malicious components ranging from SMTP spammers to the fully functional Sakura RAT trojan. Upon execution, the malicious code triggered a complex infection chain utilizing VBS and PowerShell scripts, encrypted archives, and Electron-based applications. The attack was augmented with extensive reconnaissance of the victim’s system and the use of advanced evasion techniques—including anti-debugging, privilege escalation, and persistence mechanisms.
Water Curse does not confine itself to a single malware type. Its toolkit includes security bypass utilities, spam generators, tainted game cheats, cryptocurrency-related tools, open-source intelligence collectors, and a comprehensive suite of surveillance functions. Particular emphasis is placed on harvesting credentials, session tokens, and sensitive browser data. The exfiltrated information is actively transmitted via Telegram and public file-sharing platforms.
Analysis of the repositories revealed that no fewer than 76 GitHub accounts were employed in this campaign. Based on code patterns, documentation style, and linguistic cues, researchers concluded that the group is deeply embedded within the cybercriminal marketplace, profiting from the sale of access credentials and stolen data. Despite the campaign’s vast scale, the delivery mechanisms and tooling are meticulously crafted to appear credible to developers, thereby achieving a high success rate in compromising targets.
In addition to Water Curse, the report highlights other malware campaigns leveraging the ClickFix strategy for payload delivery. These include AsyncRAT, DeerStealer, Filch Stealer, LightPerlGirl, and SectopRAT. These tools infiltrate victims’ systems through ephemeral Cloudflare tunnels, which generate temporary subdomains visually indistinguishable from legitimate domains—bypassing perimeter defenses without the need for compromised servers or bulletproof hosting.
The use of such transient tunnels renders attacks nearly invisible to traditional security systems, as the infrastructure is spun up on demand, leaving no lasting forensic footprint. This presents a formidable challenge for security teams attempting to distinguish legitimate DevOps activity from malicious behavior.
Taken together, these operations reveal an increasingly sophisticated adversarial approach—scaling malicious campaigns, co-opting legitimate infrastructure, and embedding threat activity seamlessly into the digital routines of developers and IT professionals. Platforms such as GitHub, OneDrive, MediaFire, and Cloudflare are now frequently repurposed as delivery vectors in operations once confined to underground forums and anonymous hosting services.


