
Automotive giant Volkswagen Group has unexpectedly appeared on a darknet leak site operated by the ransomware collective Stormous, where the group typically publishes data stolen from its victims. The claim surfaced in late May, though as of the time of publication, there is no concrete evidence of a breach or confirmed data leak.
According to the hackers, they allegedly gained access to user accounts, authentication tokens, access control data, and other internal information. However, no samples or files have been provided to substantiate these claims—only non-functional links were posted. Nonetheless, Stormous is a known entity within the cybercriminal underworld, and its declarations are not always without merit.
Experts speculate that this behavior may be a tactic of psychological pressure. The absence of immediate proof may indicate an attempt at extortion, with the attackers awaiting a reaction from the targeted organization—perhaps to initiate negotiations behind closed doors.
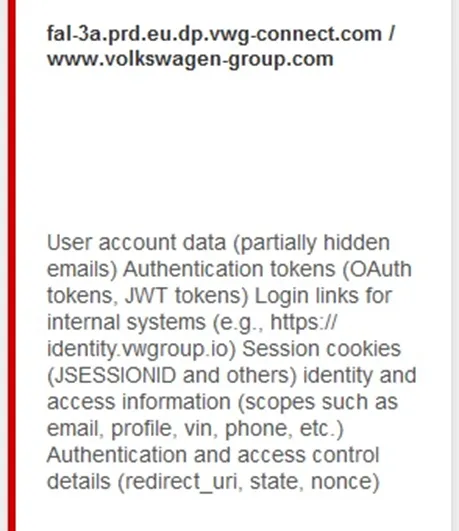
Should the threat prove credible, the implications for Volkswagen could be severe. The exposure of authentication tokens and other credentials could facilitate account takeovers and unauthorized access to internal systems. Additionally, if personal user data—such as names and email addresses—has been compromised, the company could face significant privacy breaches and regulatory repercussions.
Active since 2022, Stormous has established itself as one of the more persistent players in the ransomware ecosystem. The group previously claimed responsibility for an attack on Belgian brewery Duvel Moortgat and purportedly leaked passwords and email addresses belonging to French organizations. According to Ransomlooker, a platform monitoring darknet activity, Stormous targeted at least 34 organizations in the past year alone.
As of now, Volkswagen Group has not issued a public statement regarding the incident. It remains possible that the attack is a fabrication—an all-too-common occurrence on the darknet, where threats often serve as tools of coercion even in the absence of actual data breaches.


