Execution Flow
New samples of PowerShell-based malware, representing an advanced evolution of the notorious data-stealer ViperSoftX, have begun circulating across clandestine forums. The 2025 variant marks a significant technical leap over its 2024 predecessors, boasting enhanced modularity, stealth, and resistance to removal—making it particularly dangerous for both cryptocurrency users and corporate environments.
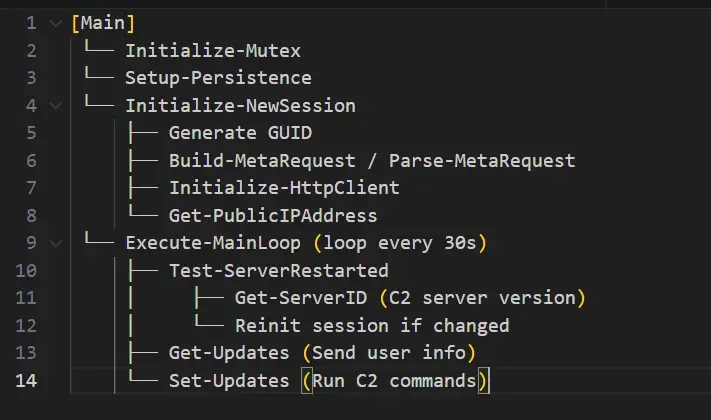
Code analysis confirms numerous refinements aimed at increasing the malware’s resilience and evading detection. Its architecture has grown more agile and adaptive, with a meticulously engineered lifecycle—from initialization to command-and-control communication.
The execution process has been substantially reworked. Unlike the 2024 version, which relied on a simple 10-second delay and a static mutex, the updated build employs a GUID-based identifier to prevent duplicate launches and extends the delay to 300 seconds. This approach not only prevents concurrent execution but also reduces the likelihood of detection within sandbox environments and behavioral analysis systems.
For network evasion, the legacy System.Net.WebClient component has been replaced with the more modern HttpClient, enabling manipulation of HTTP headers and support for encrypted HTTPS connections—mimicking legitimate software behavior. Furthermore, communication between infected hosts and command servers is now obfuscated using a simple XOR cipher with key 65, rather than transmitting data in plaintext or base64 as before. This obfuscation hampers traffic analysis and bypasses standard detection mechanisms.
Persistence techniques have been notably fortified. While ViperSoftX previously depended on external loaders, the latest version employs three redundant methods to survive system reboots. A scheduled task disguised as a system process—“WindowsUpdateTask”—is created; a registry key is added under HKCU for autorun; and a concealed BAT file is placed in the user’s startup folder. The PowerShell script itself is hidden in AppData\Microsoft\Windows\Config\winconfig.ps1, carefully masked during installation.
The malware’s functionality has also expanded considerably. Beyond rudimentary data harvesting, it now targets a wide array of cryptocurrency wallets, including Exodus, Atomic, Electrum, and Ledger. Browser extensions used for crypto transactions—such as MetaMask, Binance, and Coinbase—have also been targeted, along with KeePass configuration files.
Additionally, the malware queries the victim’s IP address via multiple fallback services to determine geolocation and associate the device with a specific campaign. This geotagging mechanism was absent in earlier versions.
Its modular design has grown even more sophisticated: functions like Get-ServerID and Test-ServerRestarted allow the malware to track changes in command-and-control infrastructure and automatically re-establish communication if the server is relocated or rebooted. Such capabilities elevate it to the realm of tools employed in high-level targeted attacks.
The report’s authors emphasize that the new ViperSoftX build is not merely an iteration, but a qualitative transformation. Unique victim identification, encrypted communications, and seamless command-server synchronization render it a formidable challenge for detection and forensic analysis. Its broadened target scope and elevated durability raise the bar for malware of its kind within the threat landscape.
To mitigate threats of this caliber, experts recommend deploying comprehensive security solutions capable of identifying malicious behavior across multiple stages of the infection chain.


