Cybersecurity experts at Sekoia have uncovered a large-scale campaign in which an unidentified group, operating under the codename ViciousTrap, compromised nearly 5,300 network devices positioned at the edge of corporate and residential networks across 84 countries, transforming them into a unified surveillance infrastructure.
The attackers exploited a critical vulnerability—CVE-2023-20118—affecting Cisco Small Business router models RV016, RV042, RV042G, RV082, RV320, and RV325. The brunt of the assault was borne by Macau, where 850 devices were overtaken.
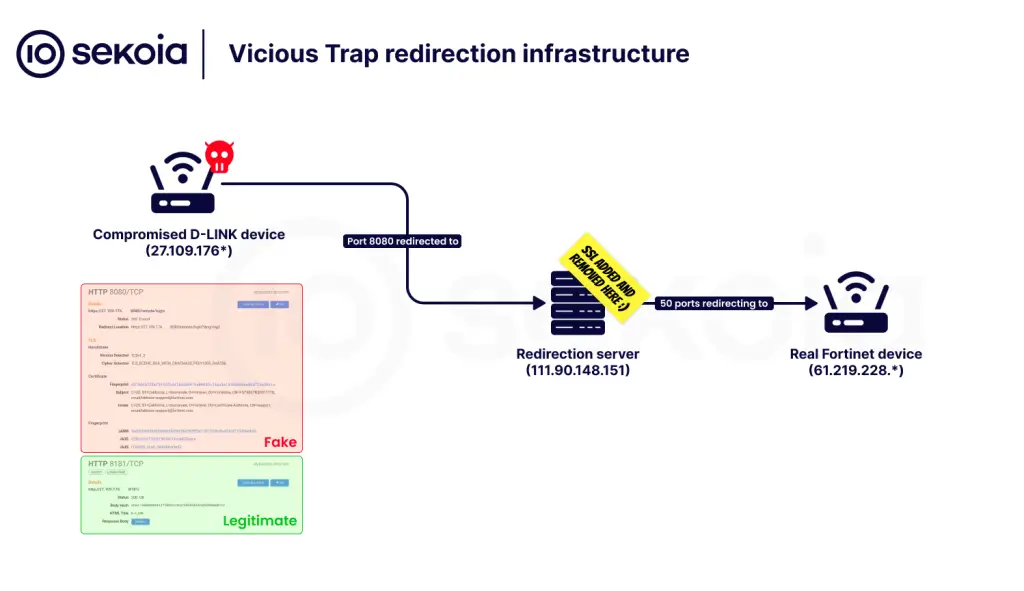
The infection vector involved the deployment of a specialized shell script dubbed NetGhost. This script configured port forwarding from the compromised router to the attackers’ infrastructure, enabling real-time interception and inspection of network traffic. As a result, thousands of hijacked devices were effectively weaponized as lures for other threat actors and as tools for harvesting exploitation attempts.
According to Sekoia analysts, the activities of ViciousTrap are not directly linked to the PolarEdge botnet, which also previously exploited CVE-2023-20118. However, there is reason to believe that the operators behind ViciousTrap are constructing a bespoke reconnaissance network comprising devices from diverse vendors, including not only SOHO routers but also SSL VPNs, digital video recorders, and BMC controllers. This expansion of infrastructure allows them to surveil emerging attack techniques, uncover covert exploits, and repurpose access obtained by other groups.
Technically, the attack followed a multi-stage sequence: the Cisco vulnerability was first exploited to deliver and execute a bash script via ftpget, which then retrieved a wget binary from an external server. The attackers subsequently leveraged the same vulnerability to deliver and run a second script—NetGhost—whose primary function was to reroute device traffic to the adversary’s infrastructure, facilitating adversary-in-the-middle (AitM) attacks. To evade detection, the script was designed to delete itself post-execution.
Analysis of the exploitation attempts revealed that all attacks originated from a single IP address (101.99.91[.]151), with the first incidents recorded in March 2025. By April, the adversaries began using a previously undocumented web shell that had appeared in prior PolarEdge operations, now repurposed for this new campaign. Researchers note that NetGhost’s redirection mechanism allows for the covert collection not only of exploit attempts but also of calls to backdoors planted by other attackers.
In May, the campaign expanded to target ASUS routers. These exploits came from a different IP address (101.99.91[.]239); however, no decoy infrastructure was deployed in those instances. All implicated IPs are associated with Malaysian hosting provider Shinjiru (AS45839). Indicators such as overlapping infrastructure with GobRAT and traffic redirection to assets in Taiwan and the U.S. suggest a likely Chinese-speaking origin of the group.
This unfolding scenario starkly illustrates that even widely deployed network devices can swiftly be weaponized for reconnaissance if vulnerabilities remain unpatched. The security of today’s infrastructure increasingly hinges not solely on vendor selection but on the capacity for rapid incident response and the proactive mitigation of security flaws.


