The cybercriminal group Venom Spider, also known as TA4557, has shifted its attack vector and is now targeting corporate human resources departments. This new campaign employs meticulously crafted phishing emails disguised as job applicant responses. Through this ruse, the attackers aim to infect enterprise systems with More_eggs malware—a formidable threat to businesses across multiple sectors.
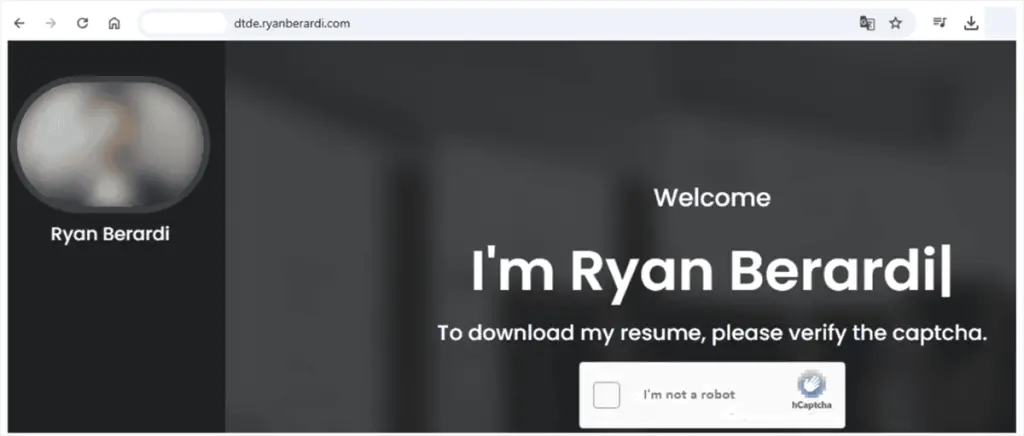
According to Arctic Wolf, the threat actors leverage popular job search platforms and messaging apps to disseminate counterfeit résumés embedded with malicious attachments. Once a recipient clicks the link, they are redirected to a fraudulent download page requiring CAPTCHA verification, designed to bypass automated security filters. The user is then served an archive containing a decoy image and a Windows shortcut file (LNK) masquerading as a résumé.
Embedded within this file is a script that triggers native Windows utilities such as “ie4uinit.exe,” enabling the execution of malicious code without raising antivirus alarms. To further obscure its actions, the script launches WordPad to simulate the opening of a legitimate document. In the next phase, JavaScript code hosted on remote servers is retrieved and executed. This script deploys a dropper, which registers itself using the regsvr32 utility.
During execution, additional files are written to the AppData directory, and delayed code execution is employed to evade sandbox environments and static analysis tools. The final stage involves the installation of a backdoor that utilizes encryption with uniquely generated keys derived from the host’s computer name and processor ID, ensuring the malware is tightly bound to the compromised device. Once deployed, the backdoor establishes persistent communication with command-and-control servers, allowing attackers to issue commands, download additional payloads, and exfiltrate data.
A distinguishing aspect of this campaign is its deliberate targeting of HR professionals—individuals who, by the nature of their role, routinely open attachments from unknown senders. By exploiting this universal point of entry, Venom Spider capitalizes on a vulnerability inherent to virtually every organization, regardless of industry. Previously, the group focused on U.S.-based e-commerce and pharmaceutical firms, but the scope of their operations has since expanded considerably.
The report’s authors emphasize that effective mitigation hinges on raising employee awareness about phishing tactics, deploying secure email gateways, and implementing behavioral analysis tools at the endpoint level. Additional recommendations include inspecting file properties before opening attachments and blocking known command-and-control domains involved in the infection chain.
Detection is further complicated by the adversaries’ use of cloud infrastructure—such as Amazon and GoDaddy—to host attack components, along with their application of multi-layered obfuscation and encryption techniques. Given the high degree of automation and precision targeting, these attacks may go unnoticed for extended periods, posing a significant threat to corporate data and reputation.


