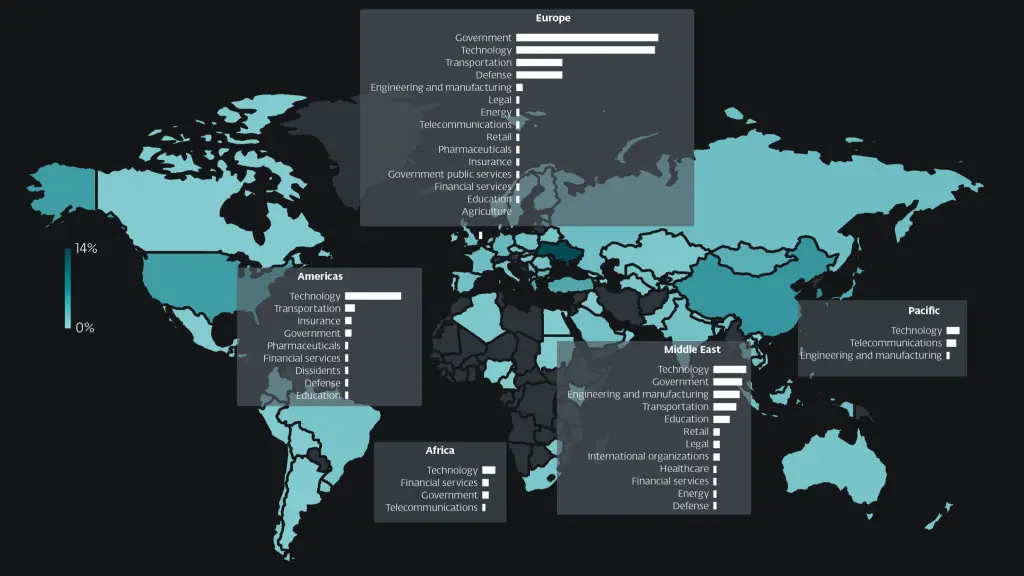
Targeted countries and sectors | Image: ESET
Researchers at ESET have uncovered the operations of a little-known yet active cyber-espionage group linked to China, designated UnsolicitedBooker. According to the report, the group targeted an international organization based in Saudi Arabia, deploying a previously undocumented malware strain named MarsSnake. The first recorded intrusion occurred in March 2023, followed by at least two additional attempts in 2024 and 2025.
During the campaign, the attackers distributed phishing emails containing a lure in the form of a flight ticket, purportedly sent by the airline Saudia. Attached to the message was a Microsoft Word document embedded with a VBA macro. When opened, the document executed malicious code that saved an executable named “smssdrvhost.exe” to the system. This file functioned as a loader, triggering the deployment of MarsSnake—a backdoor that established communication with a remote server at contact.decenttoy[.]top.
The phishing email incorporated a legitimate ticket sourced from Academia, a platform known for hosting academic publications. This added a layer of credibility to the decoy, reinforcing the attack with sophisticated social engineering tactics.
UnsolicitedBooker has previously employed well-known Chinese malware such as Chinoxy, DeedRAT, Poison Ivy, and BeRAT. Its attack patterns bear striking similarities to those associated with the Space Pirates and Zardoor clusters—the latter recently implicated in intrusions against an Islamic nonprofit organization in Saudi Arabia.
ESET’s report notes that UnsolicitedBooker maintains persistent operations across Asia, Africa, and the Middle East. The repeated targeting of a single organization over a span of three years suggests sustained interest and likely strategic value attributed to the victim.
Simultaneously, researchers observed renewed activity from another Chinese APT group—PerplexedGoblin, also known as APT31. In December 2024, the group infiltrated a governmental body in Central Europe, deploying the surveillance-focused backdoor NanoSlate.
Also under continued scrutiny is the DigitalRecyclers group, active since at least 2018. This actor targets governmental institutions within the European Union and leverages the ORB proxy network (Operational Relay via KMA VPN) to obscure its network traffic. Notable malware deployed by the group includes RClient, HydroRShell, and GiftBox. Of particular interest is HydroRShell’s use of Google Protobuf protocols and the Mbed TLS library to facilitate communication with its command-and-control infrastructure.
ESET attributes DigitalRecyclers to a broader constellation of Chinese threat actors, linking it to the Ke3chang and BackdoorDiplomacy groups—both regarded as components of the loosely defined APT15 ecosystem. Given the breadth of tools employed and the scale of these campaigns, all of the aforementioned groups represent a significant and escalating threat on the global cyber-espionage stage.


