
Amid the growing proliferation of consumer-grade surveillance apps for smartphones, it has become increasingly evident that such software is evolving to be more covert and significantly harder to remove. A newly discovered Android application, identified by TechCrunch journalists, exemplifies this troubling trend—capable not only of hiding in plain sight but also of effectively preventing its own uninstallation without a specific password.
This spyware, whose name remains undisclosed to avoid publicity, exploits Android’s native capability to overlay content atop other apps. Leveraging this feature, it displays a password prompt whenever a user attempts to uninstall it via the device’s settings. The password is set by the individual who initially installed the spyware.
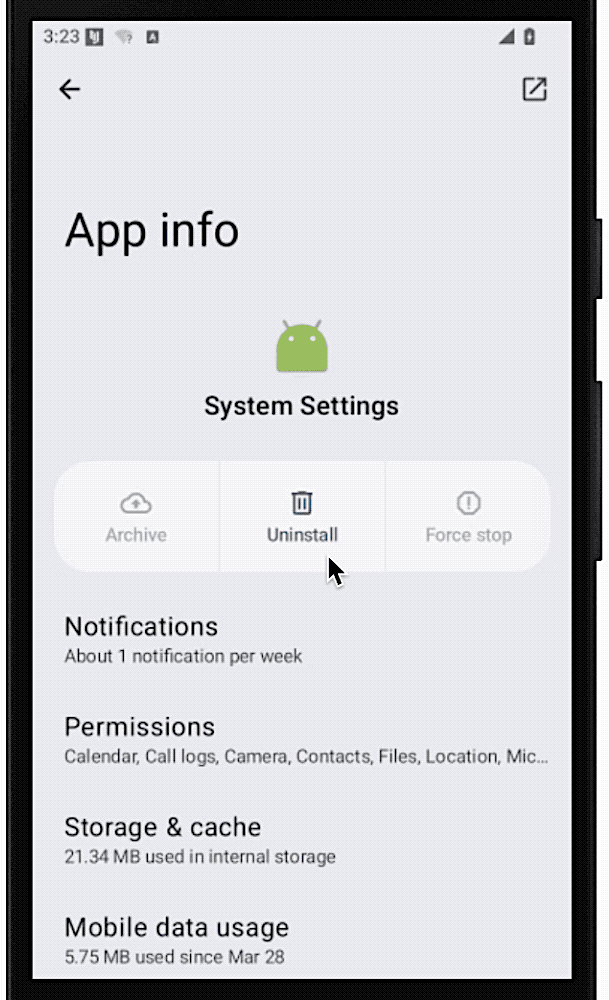
Exacerbating the issue, the application does not appear on the home screen—it masquerades as a standard system settings item with an innocuous icon, rendering it even less conspicuous and more difficult to detect.
Such applications are often marketed under the guise of parental control tools or employee monitoring solutions. In reality, however, they are frequently deployed to secretly spy on partners or spouses, a practice that violates privacy laws and is categorized as the use of “stalkerware” or “spouseware.”
Typically, these apps are sideloaded outside of the official Google Play Store, requiring physical access to the device and knowledge of its unlock credentials. Once installed, the spyware conceals itself and begins exfiltrating user data to a remote server—ranging from text messages and photos to real-time location data. The operator can manage this surveillance through a web-based control panel.
Detection of such covert software generally requires delving into Android’s system settings, particularly within the Device Admin section. The presence of an unfamiliar or suspicious app in this list can be a red flag. However, attempting to remove it through conventional means triggers the aforementioned password prompt.
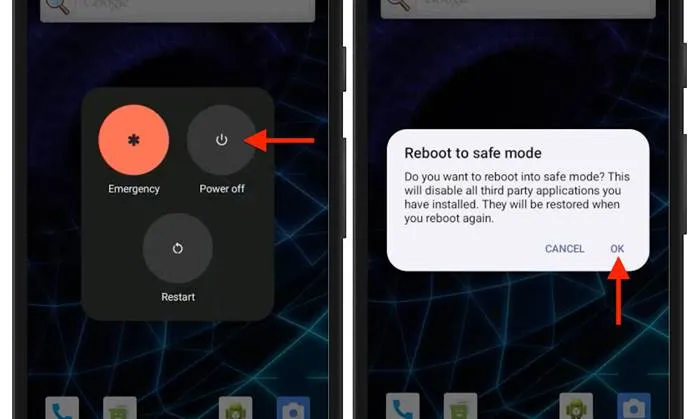
According to TechCrunch, a viable countermeasure involves rebooting the device in Safe Mode. This mode temporarily disables all third-party applications, including the spyware, thereby allowing it to be removed without invoking the protective overlay.
To enter Safe Mode, one must press and hold the power button, then tap and hold the “Power off” option until a prompt appears offering to restart in Safe Mode. Upon reboot, a message confirming Safe Mode will appear in the corner of the screen.
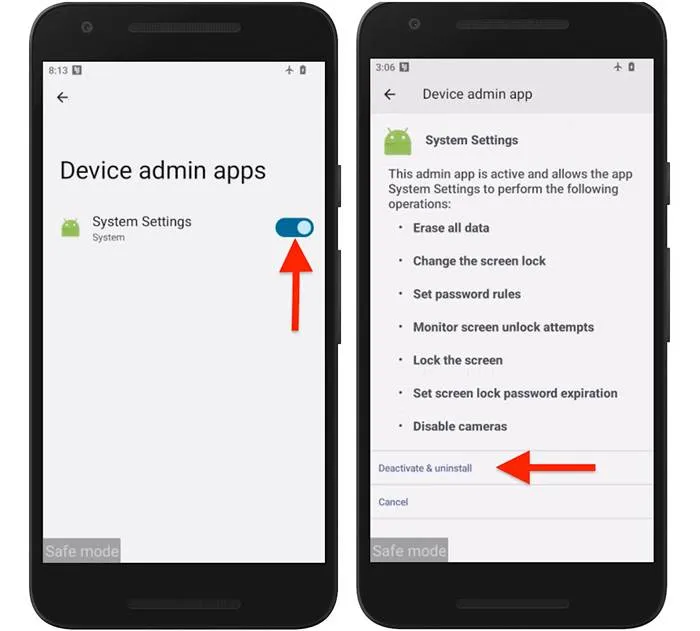
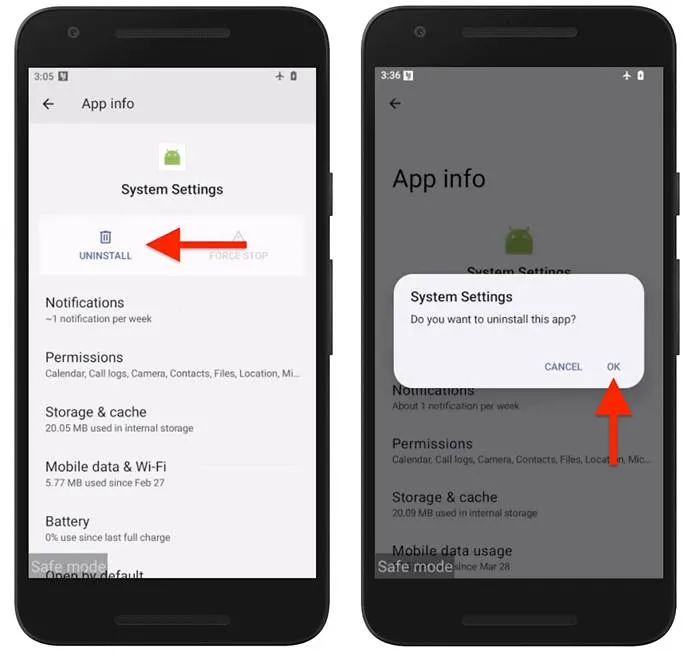
Next, navigate to the settings menu, locate the “Device Administrators” section, and revoke administrative privileges from the suspicious application. Once deactivated, the app can be fully uninstalled via the “Apps” or “Applications” menu.
It is important to note that removing such software may alert the individual who installed it. Therefore, it is advisable to devise a comprehensive safety plan prior to taking action. After uninstallation, immediate steps should be taken to reinforce the phone’s security—this includes setting a strong lock screen password and updating credentials for linked accounts, especially the Google account.
In conclusion, even if a surveillance app operates silently in the background and actively resists removal, users still have the tools to reclaim control. Success hinges on awareness, vigilance, and the precise execution of countermeasures.


