A Chinese threat group linked to the malicious actor UNC5221 has launched an extensive espionage campaign leveraging newly developed variants of the BRICKSTORM malware. Since late 2022, European enterprises operating in strategic sectors have become regular targets. Initially confined to targeting Linux-based vCenter servers, BRICKSTORM has now evolved with Windows variants that exhibit enhanced capabilities for stealth and evasion.
According to analysts at NVISO, the Windows version of BRICKSTORM is written in Go 1.13.5 and notably lacks a direct command execution function. Instead, the attackers employ a traffic tunneling module, enabling the use of RDP and SMB protocols through compromised credentials. This method helps circumvent detection tools that monitor parent-child process relationships.
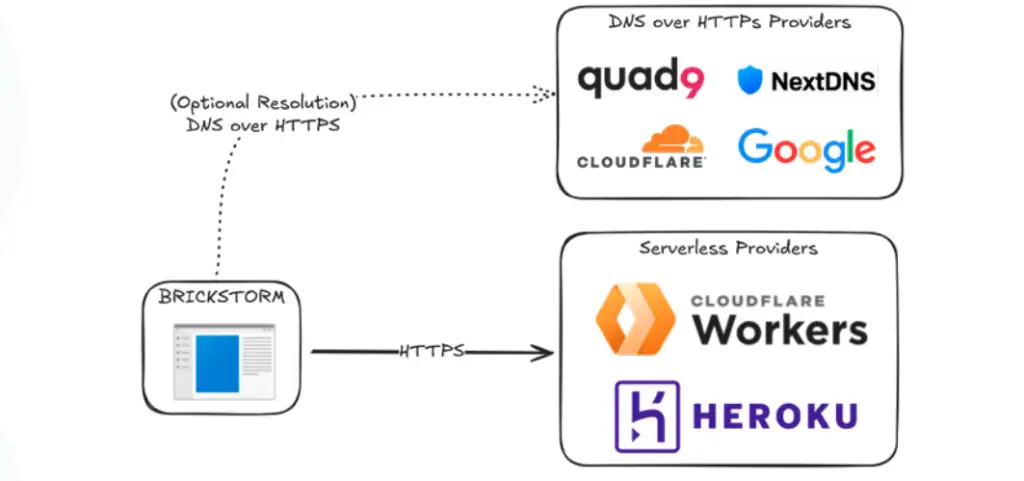
BRICKSTORM’s file management system operates via an HTTP API using JSON formatting, allowing attackers to upload, download, and modify files. The tunneling module supports TCP, UDP, and ICMP protocols, facilitating lateral movement deep into the victim’s infrastructure. Recent versions include a hardcoded IPAddrs parameter—an explicit list of IP addresses that ensures connectivity even when DNS-over-HTTPS (DoH) is restricted.
Earlier versions relied exclusively on DoH queries via Quad9 and Cloudflare, embedding DNS requests into HTTPS POST traffic to evade conventional DNS traffic monitoring. The latest samples exhibit adaptive switching between DoH and direct IP resolution, enhancing their resilience in diverse network environments.
BRICKSTORM employs a three-tiered traffic obfuscation architecture involving nested TLS connections. The outer layer consists of legitimate HTTPS sessions to stateless platforms such as Cloudflare Workers and Heroku, secured with valid certificates. The middle layer upgrades the connection to WebSocket and initiates a secondary TLS handshake authenticated with a static key. The innermost layer utilizes HashiCorp’s Yamux library for multiplexing command-and-control (C2) traffic, encompassing tunneling and file exfiltration.
Even when external HTTPS traffic is intercepted, the core command stream remains encrypted and concealed. Analysts have also identified IP address leaks from BRICKSTORM’s intermediary infrastructure during maintenance periods, including VPS nodes hosted on Vultr.
Command servers make use of dynamic DNS services such as “nip[.]io” and exploit weaknesses in certificate transparency mechanisms. For example, the domain “ms-azure[.]azdatastore[.]workers[.]dev” was registered with a wildcard certificate issued by Cloudflare. Domains of this nature have been observed since at least 2022. Operators routinely rotate IP addresses and certificates to preserve operational resilience and anonymity.
NVISO experts recommend organizations adopt a multi-layered security posture. Specific measures include blocking known DoH providers, inspecting TLS sessions for evidence of nested protocols, enforcing multi-factor authentication, and monitoring for anomalous activity over SMB and RDP protocols. Indicators of compromise include the execution of processes by “CreatedUACExplorer.exe” and connections to suspicious IP addresses.
Given that UNC5221’s operations align with the Chinese state’s broader agenda of industrial espionage and the acquisition of technological intelligence, sustained vigilance over server-based cloud platforms and DNS oversight systems remains imperative. Collective defense, information sharing, and continuous monitoring are essential countermeasures against threats of BRICKSTORM’s caliber.


