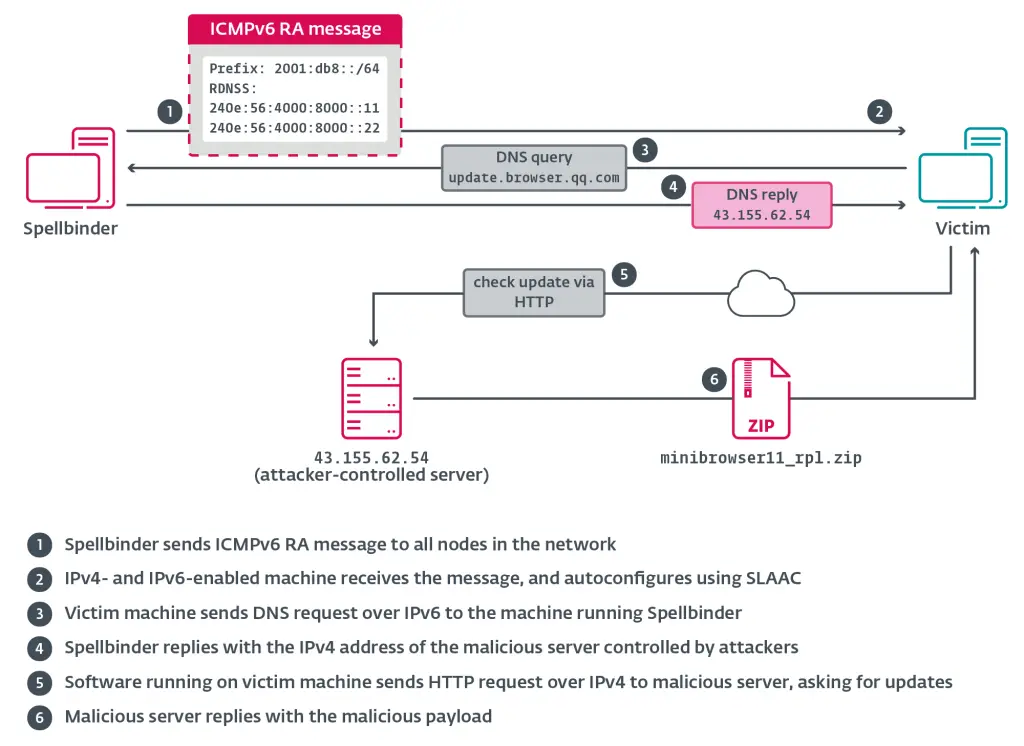
Illustration of the SLAAC attack carried out by Spellbinder | Image: ESET
The Chinese APT group known as TheWizards has adopted a novel lateral movement tactic within compromised networks, employing a tool dubbed Spellbinder. According to a recent report by ESET, this utility facilitates adversary-in-the-middle (AitM) attacks by manipulating IPv6 addressing via the SLAAC protocol, enabling traffic interception and the redirection of legitimate Chinese software updates to malicious servers.
At the heart of this operation lies the update mechanism of Sogou Pinyin — a widely used Chinese input method editor. This vector delivers a malicious loader, which in turn downloads and activates a modular malware framework known as WizardNet.
Similar manipulations involving Sogou Pinyin updates have been observed in the past: in early 2024, a separate group designated Blackwood distributed the malicious NSPX30 module through this method, followed shortly by another cluster, PlushDaemon, which used the same technique to deliver the LittleDaemon tool.
TheWizards’ campaign is geographically focused on Cambodia, Hong Kong, mainland China, the Philippines, and the United Arab Emirates. Deployment of Spellbinder has been traced back to at least 2022. Although the initial infection vector remains unidentified, the attack chain progresses with the delivery of a ZIP archive containing four files: AVGApplicationFrameHost.exe, wsc.dll, log.dat, and winpcap.exe.
Upon installation, winpcap.exe initiates the execution of another binary employing DLL sideloading, which reads shellcode from log.dat and activates Spellbinder directly in the system’s memory.
The tool operates by capturing network packets via the WinPcap library and leveraging ICMPv6 Router Advertisement — a mechanism through which devices receive routing information within a network. Spellbinder exploits this by spoofing router advertisement responses, inserting itself into the communication flow between legitimate services and end-users.
In one attack documented in 2024, this mechanism was used to intercept an update for the Tencent QQ messenger at the DNS level. The domain query for the update was redirected to an IP address controlled by the attackers, where a weaponized version of the software, embedded with WizardNet, was hosted.
In addition to Spellbinder, TheWizards also possess another tool — DarkNights, also referred to as DarkNimbus. While it was previously attributed to the Earth Minotaur group, current intelligence indicates a divergence between these clusters due to distinct infrastructure and targeting patterns. It was discovered that DarkNights is supplied by a contractor of China’s Ministry of Public Security — Sichuan Dianke Network Security Technology Co., Ltd., also known as UPSEC.
For Windows platforms, TheWizards deploy the WizardNet backdoor, whereas for Android, the compromised servers distribute DarkNights — reinforcing the assessment of Dianke as a central provider of offensive tooling for this APT group.
The subversion of widely trusted software updates into channels for delivering malicious payloads underscores the profound fragility of familiar digital infrastructure. When trust in legitimate software becomes the Trojan horse, traditional perimeter defenses lose their relevance — and network security becomes ever more dependent on who already resides within.


