Two information disclosure vulnerabilities have been identified in Linux systems, including Ubuntu, Red Hat Enterprise Linux, and...
vulnerabilities
Simplified application deployment in Kubernetes using Helm can lead to serious vulnerabilities if default configurations are left...
One of the key issues in AI security has once again come to the forefront following the...
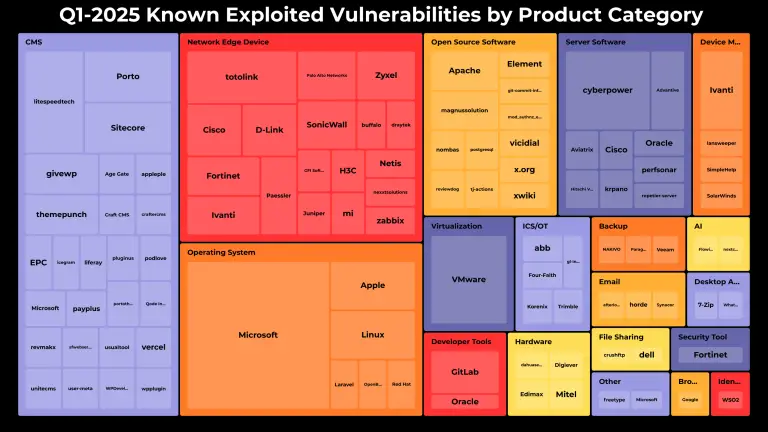
In the first quarter of 2025, cyberattacks leveraging 159 unique vulnerabilities with assigned CVE identifiers were recorded—a...
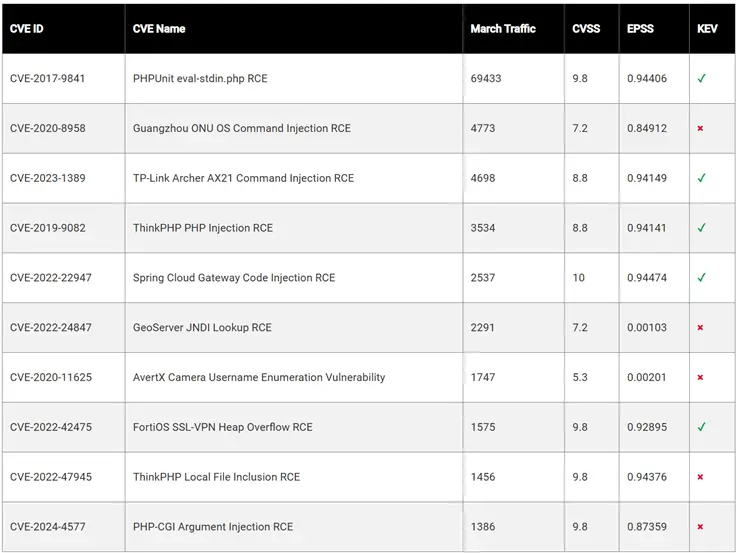
March 2025 witnessed a renewed surge in cybercriminal activity, concentrated along two principal vectors: mass scanning of...
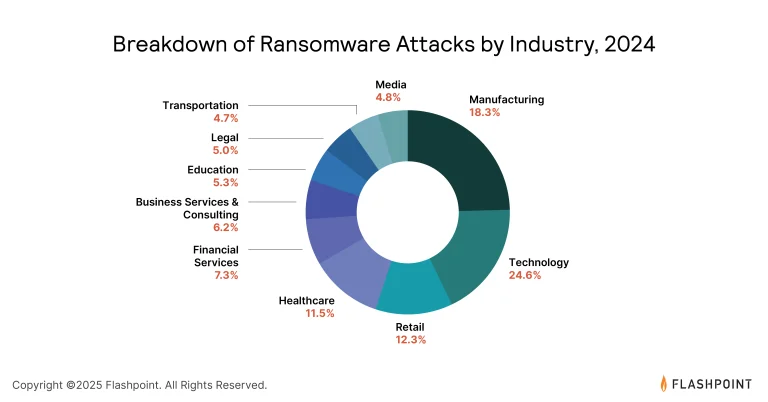
The world is confronting an unprecedented surge in cyber threats, with their scale and complexity continuing to...
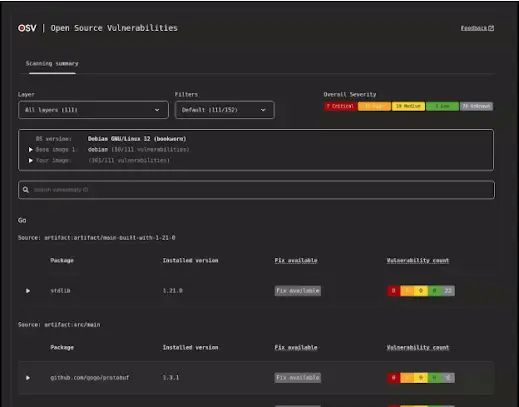
Google has announced the release of an enhanced version of OSV-Scanner, a free tool designed to detect...