The legal battle between Meta and the Israeli firm NSO Group has culminated in a devastating verdict...
security
A critical vulnerability in Langflow—a platform designed for visual construction of LLM chains—is actively being exploited by...
Simplified application deployment in Kubernetes using Helm can lead to serious vulnerabilities if default configurations are left...
The notion that spam is easily identifiable by clumsy spelling and awkward syntax no longer holds true....
An AMD engineer continues to advance processor security within Linux by proposing a novel protection management system...
Despite the widespread adoption of multi-factor authentication (MFA), cybercriminals have developed increasingly sophisticated techniques to circumvent it....
AirPlay, developed by Apple, is a proprietary protocol that allows users to wirelessly stream content from iOS...
One of the most prevalent attack vectors targeting WordPress involves disguising malicious code as a harmless plugin....
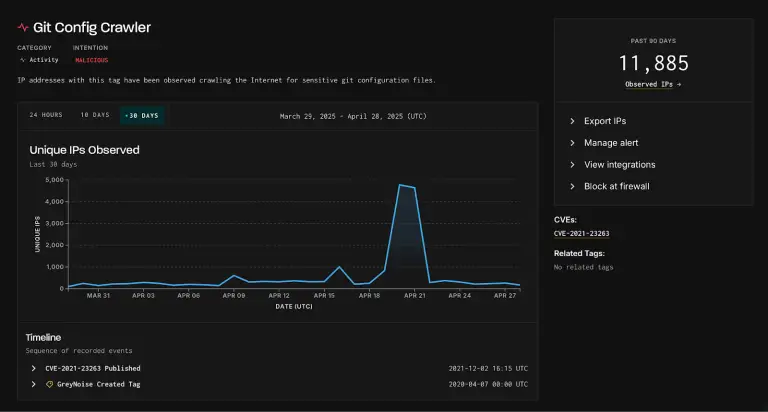
In recent days, cybersecurity experts have observed a disturbing surge in activity aimed at accessing configuration files...
Microsoft once again finds itself under scrutiny over Windows security updates. The controversy began when a recent...
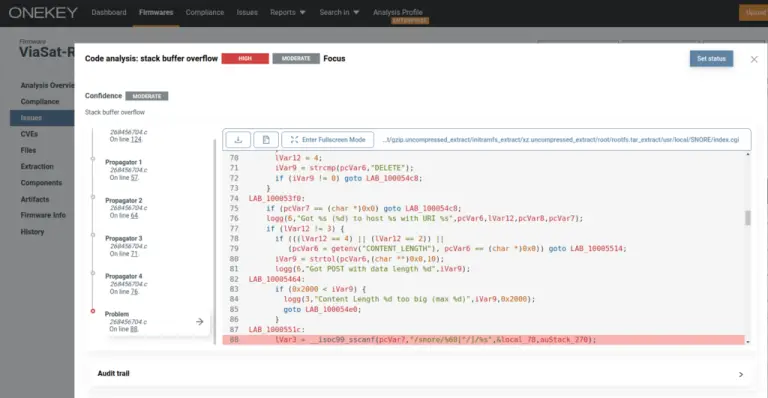
The discovery of a serious zero-day vulnerability in Viasat satellite modems has once again underscored the fragility...
On April 14, one of 4chan’s servers fell victim to an attack exploiting a vulnerability in outdated...
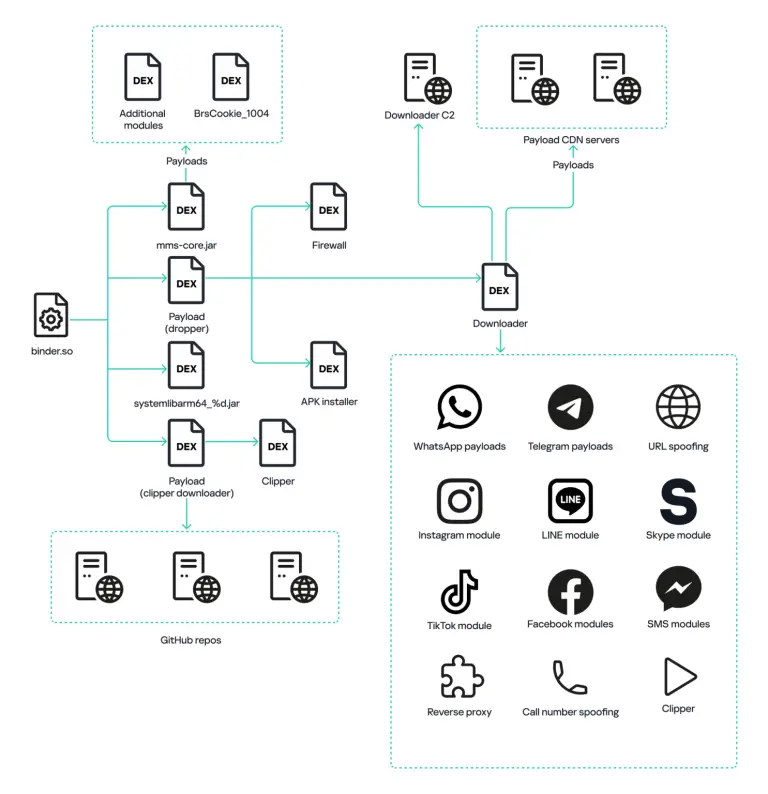
Newer versions of Android have significantly strengthened system security by prohibiting the modification of system partitions, even...
The Offensive Security team has issued a warning to Kali Linux users regarding potential system update failures—preventable...
A cybersecurity enthusiast from Russia reported a critical vulnerability in the Telegram messenger, which, in his opinion,...