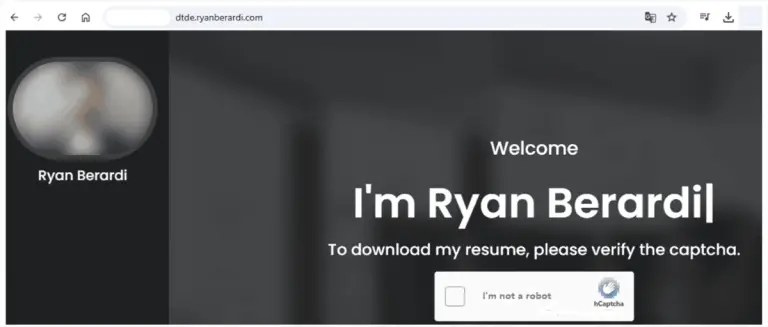
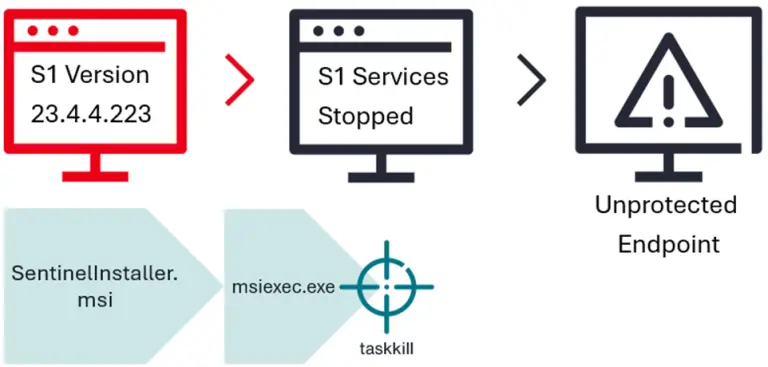
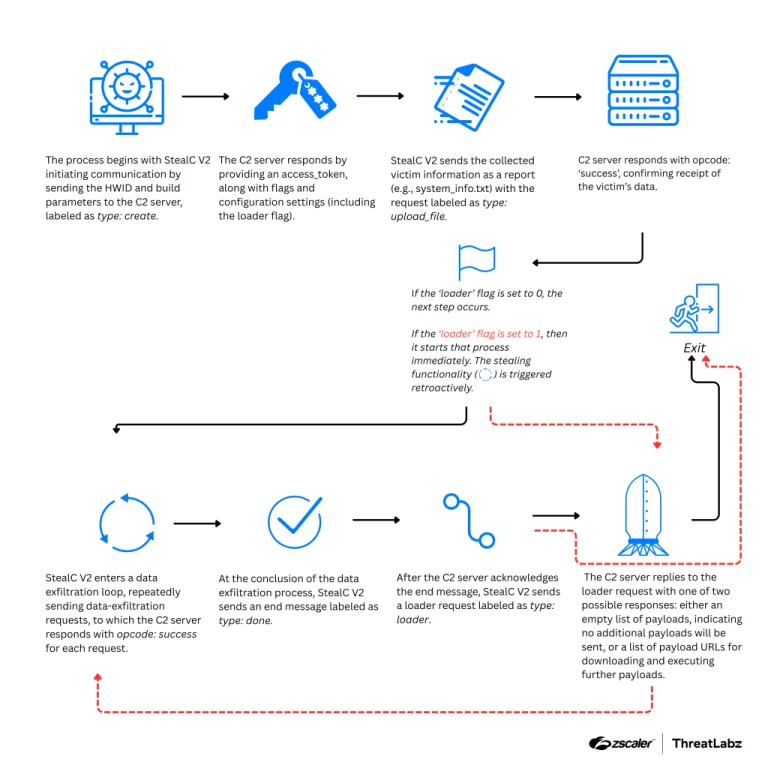
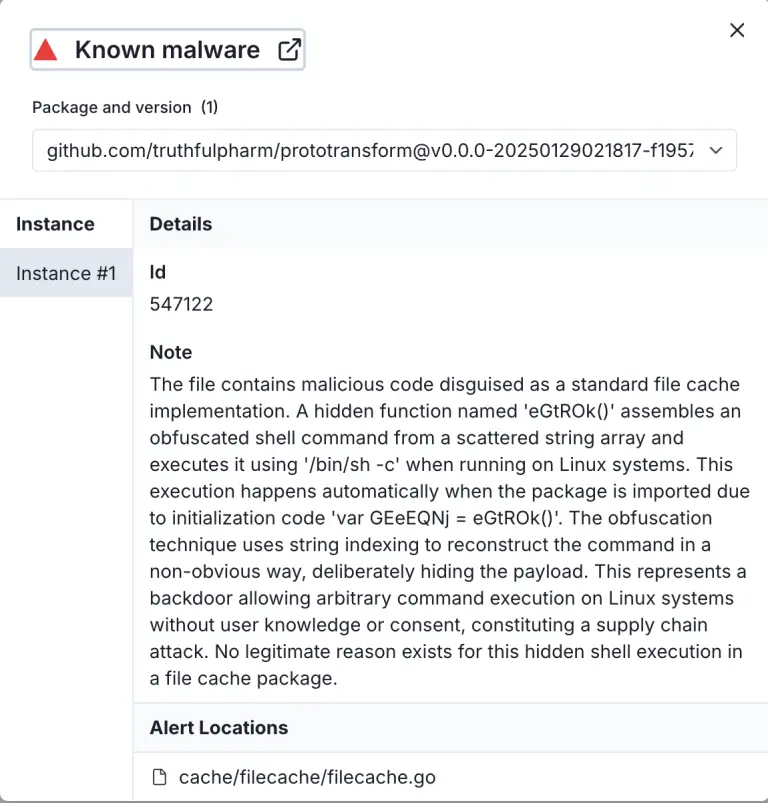
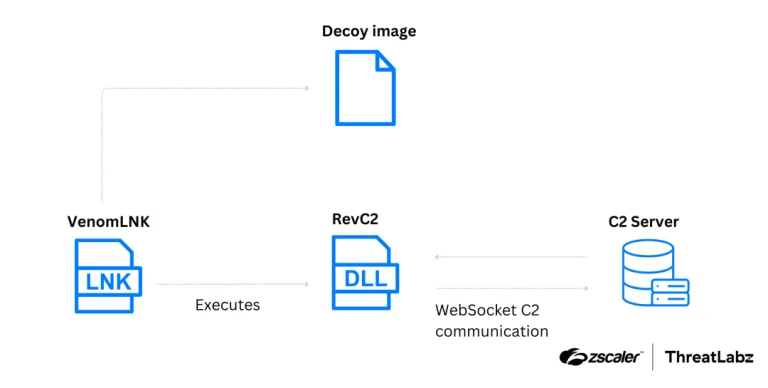
The cybercriminal group Venom Spider, also known as TA4557, has shifted its attack vector and is now...
Malware
In early 2025, incident response specialists from Aon’s Stroz Friedberg team uncovered a novel technique for bypassing...
The widely used StealC malware, actively deployed in cyberattacks for data theft and the delivery of secondary...
Three malicious components have been discovered within the Go programming module ecosystem, capable of triggering complete data...
Researchers at Insikt Group have uncovered two new digital tools circulating online, both designed to steal passwords...
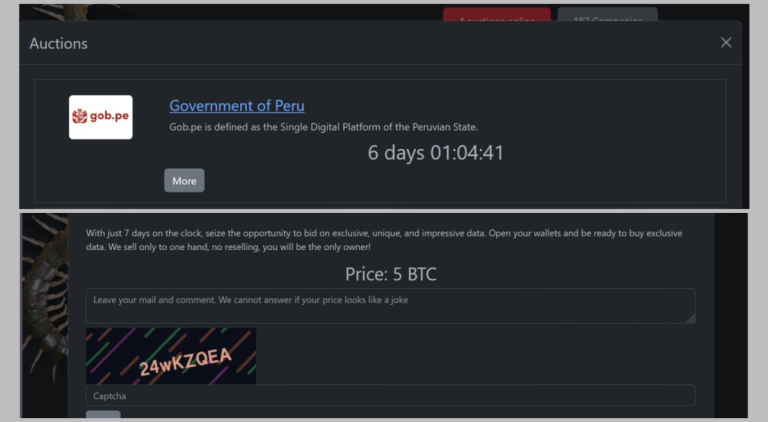
Government systems in Peru have been paralyzed following a large-scale cyberattack claimed by the hacker collective Rhysida,...
At the beginning of 2024, a California-based programmer developed a malicious application disguised as an artificial intelligence...
Software developer Ibrahim Diallo maintains a personal blog hosted on his own modest server. According to his...
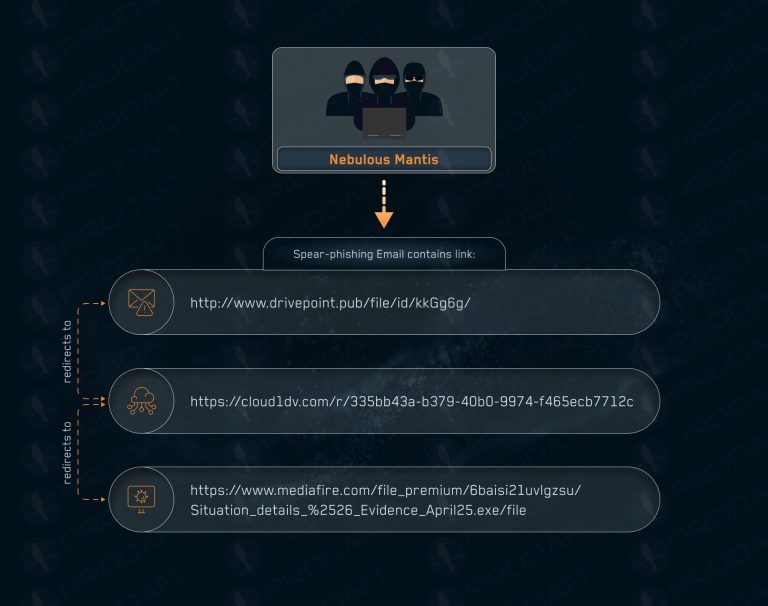
The cyber-espionage group known as Nebulous Mantis has once again drawn the attention of information security experts....
One of the most prevalent attack vectors targeting WordPress involves disguising malicious code as a harmless plugin....
Newer versions of Android have significantly strengthened system security by prohibiting the modification of system partitions, even...
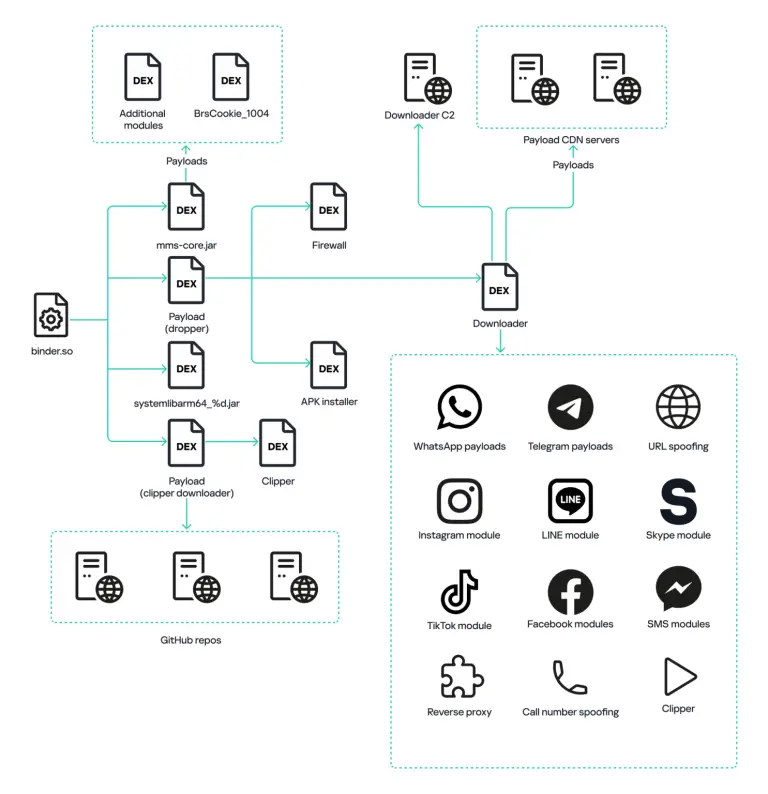
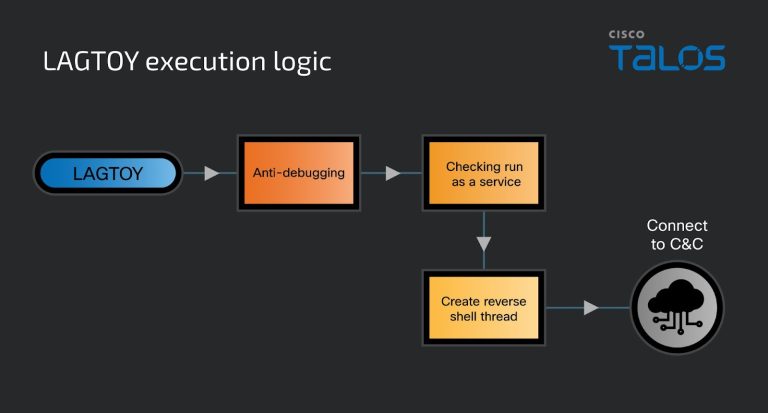
A new and formidable player has emerged on the cybercrime stage: Cisco Talos has uncovered the operations...
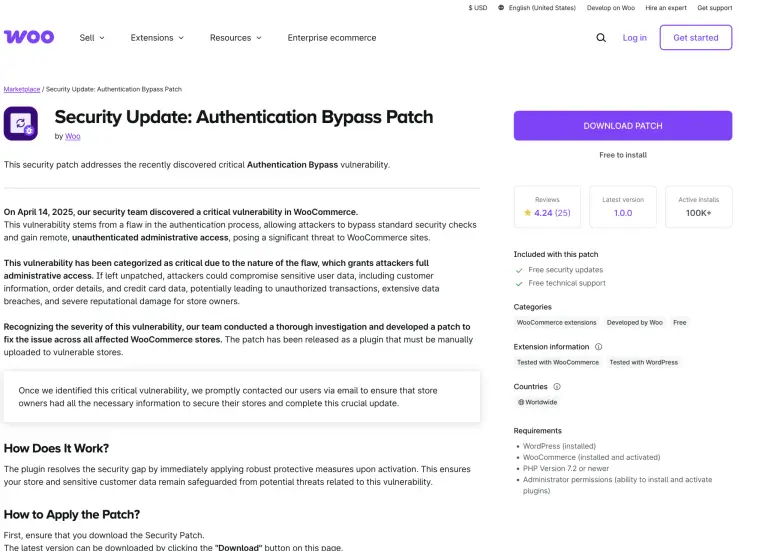
Specialists at Patchstack have uncovered a large-scale phishing campaign targeting users of the WooCommerce platform. Threat actors...
Numerous hacker groups linked to North Korea have once again drawn global attention following a series of...
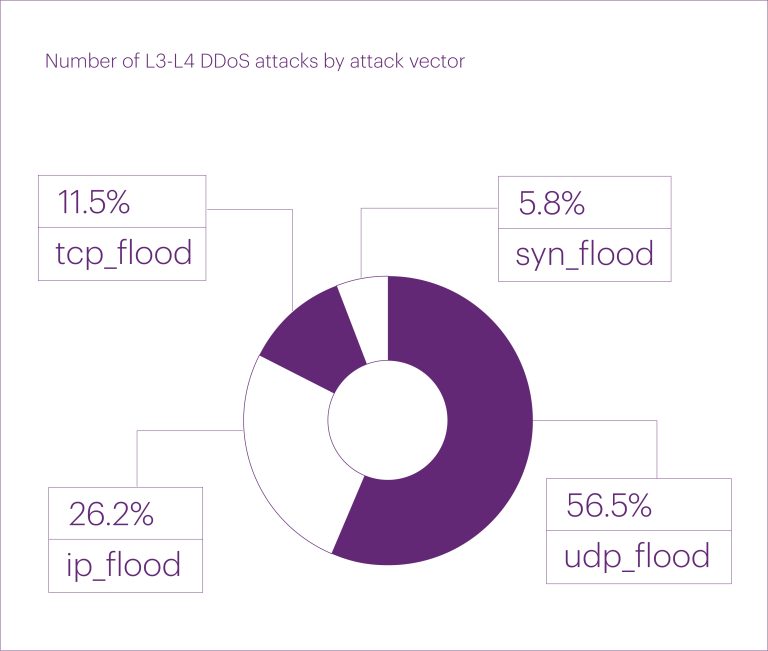
Outdated devices with high-speed internet have increasingly become liabilities to global cybersecurity—a trend starkly illustrated in 2025....