Beginning in July 2025, Microsoft will automatically block email attachments with the extensions .library-ms and .search-ms in...
Malware
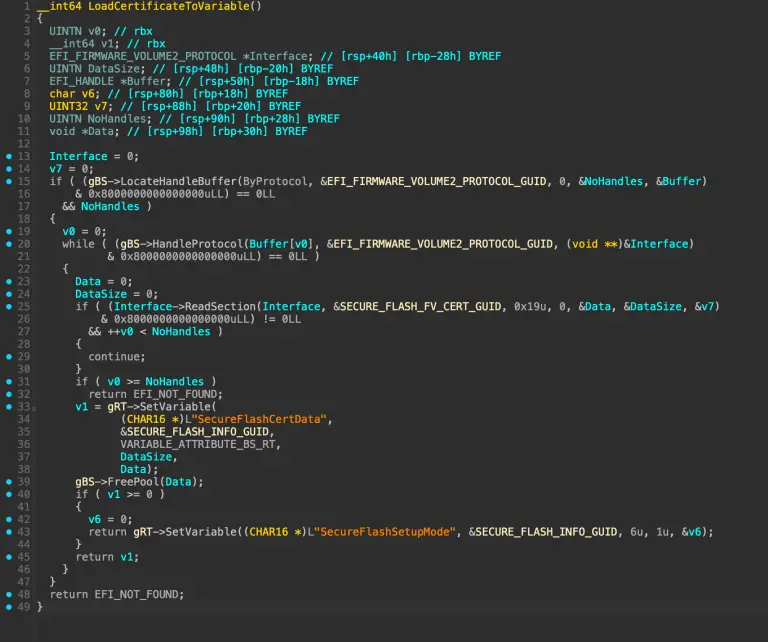
Nearly all modern computers with Secure Boot enabled have been exposed to critical risk due to a...
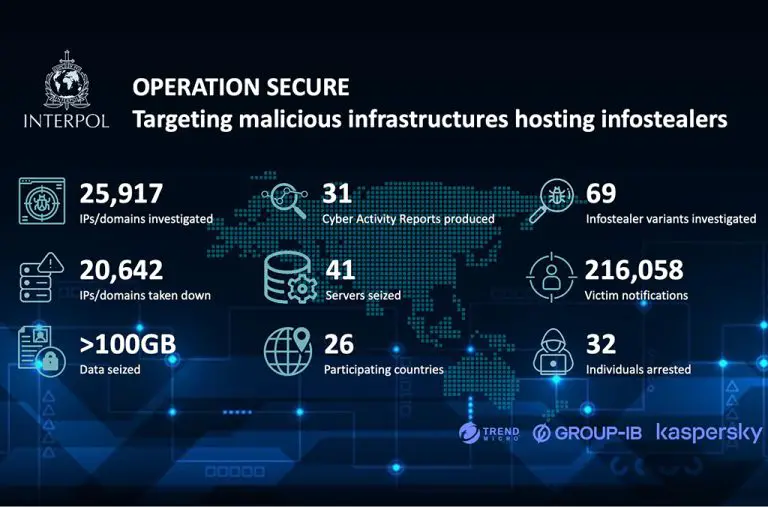
An international law enforcement operation, codenamed Operation Secure, has culminated in the large-scale dismantling of cybercriminal infrastructure...
In the spring of 2024, an obscure tool known as Skitnet—also appearing under the alias “Bossnet”—surfaced on...
Two malicious packages were recently discovered within the widely used JavaScript package registry, npm. Beneath their seemingly...
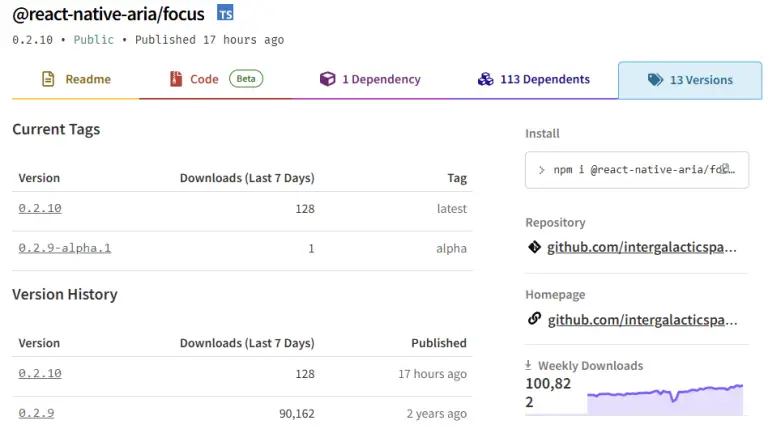
A large-scale supply chain attack has been identified on the NPM platform: threat actors compromised 17 widely...
A new wave of cyberattacks has been recorded in Ukraine, targeting the destruction of critical infrastructure. At...
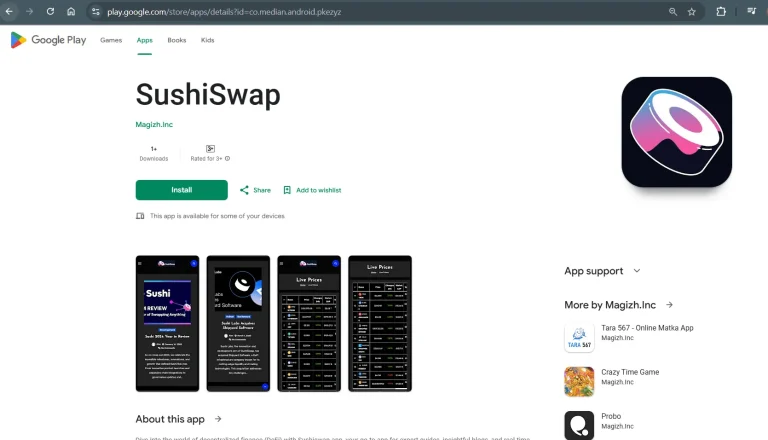
Even if you download applications exclusively from Google Play, this does not always guarantee safety—particularly when it...
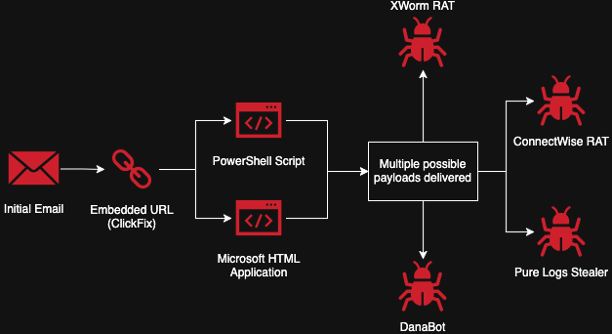
At first glance, it appears to be nothing more than a routine security check. In reality, it...
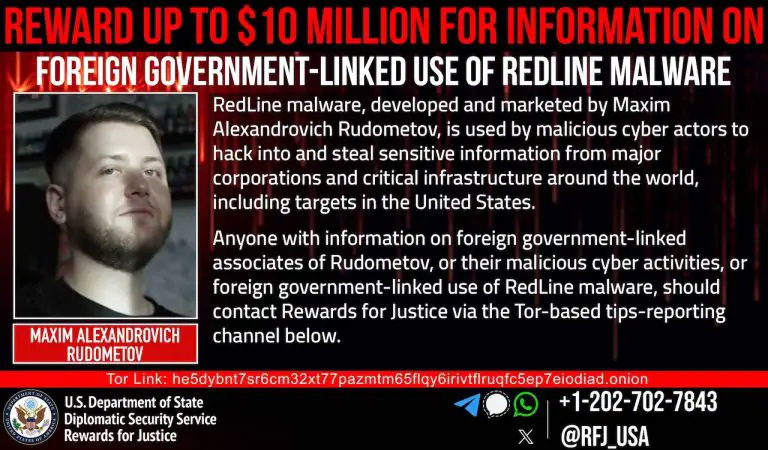
The U.S. Department of State has announced a reward of up to $10 million for information leading...
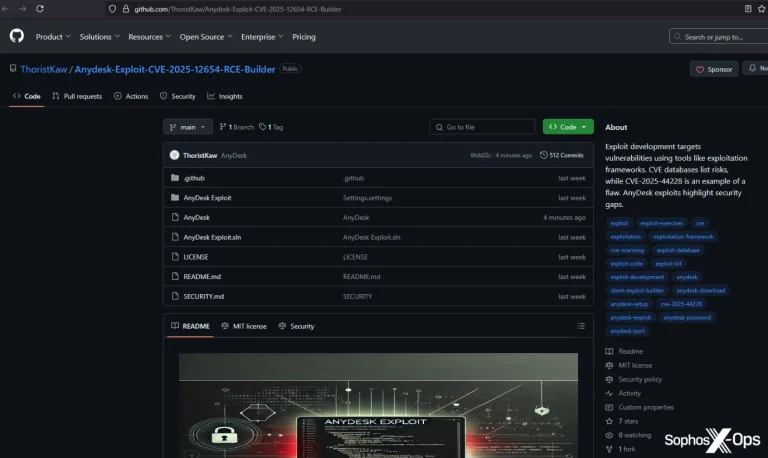
A recently uncovered malicious campaign is leveraging GitHub as a trap for security professionals, gamers, and even...
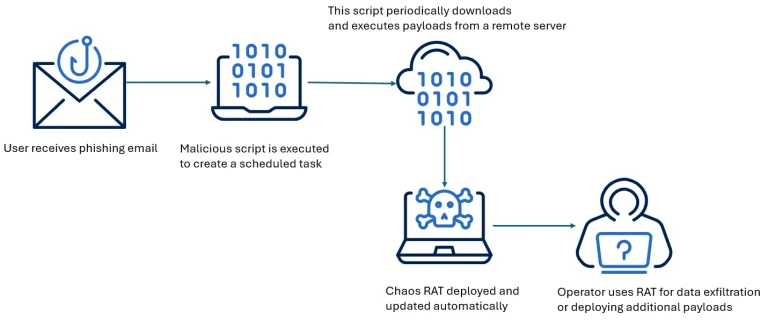
Amid a surge in cybercriminal activity, security experts have turned their attention to a new iteration of...
Researchers from the DomainTools team have reported a new malicious campaign that leverages counterfeit websites masquerading as...
Each year—especially in the lead-up to major holidays—the topic of “juice jacking,” the surreptitious theft of data...
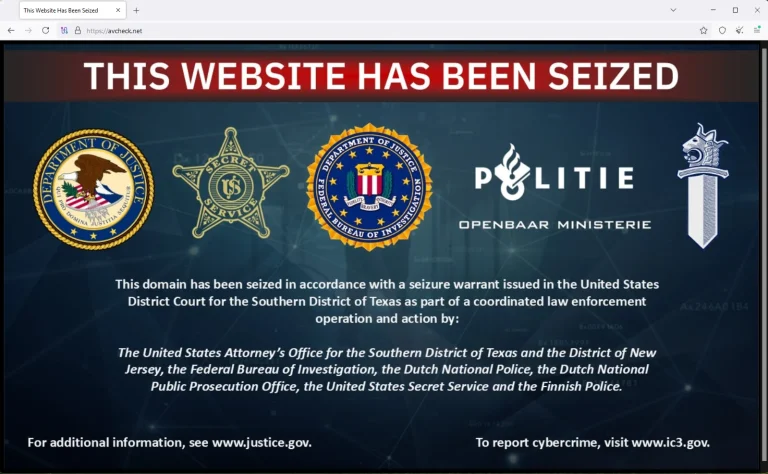
One of the most infamous underground services catering to cybercriminals—AVCheck—has come to an end. Its primary domain,...