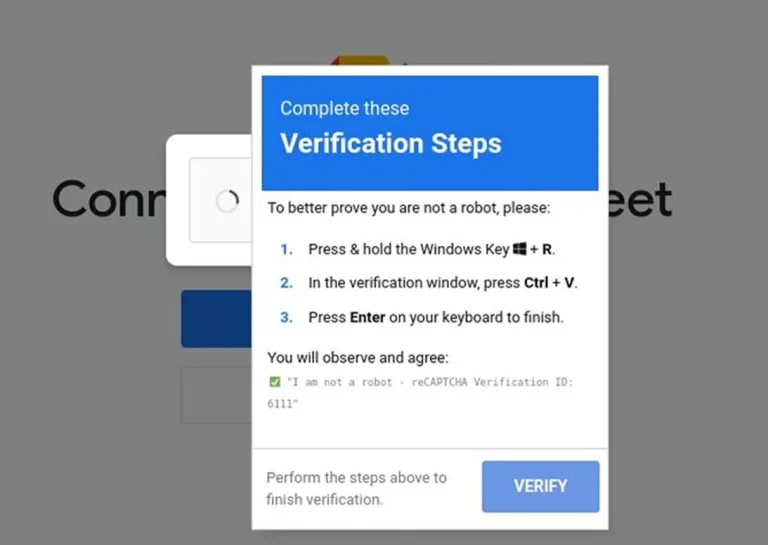
At first glance, it appears to be nothing more than a routine security check. In reality, it...
Data Theft
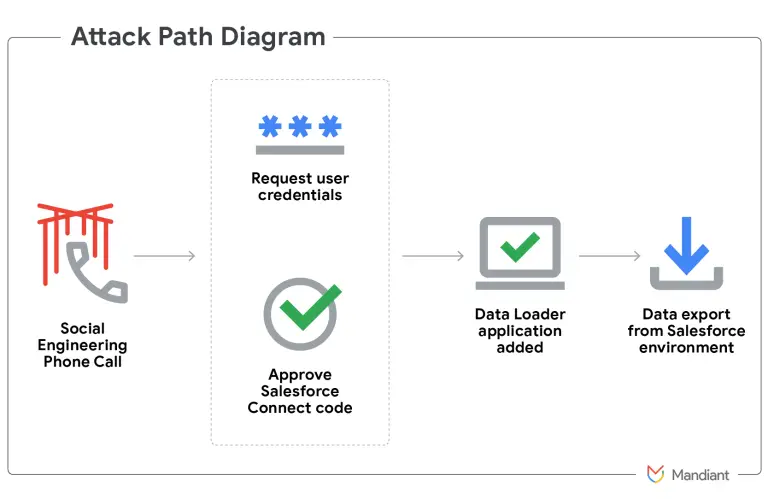
Hackers affiliated with the group UNC6040, tracked by Google’s Threat Intelligence Group, have been implicated in a...
Ukrainian cyber police have apprehended a 35-year-old man who, over several years, exploited compromised servers belonging to...
Each year—especially in the lead-up to major holidays—the topic of “juice jacking,” the surreptitious theft of data...
The Zanubis malware, purpose-built for Android-based devices, continues its relentless evolution, emerging as one of the most...
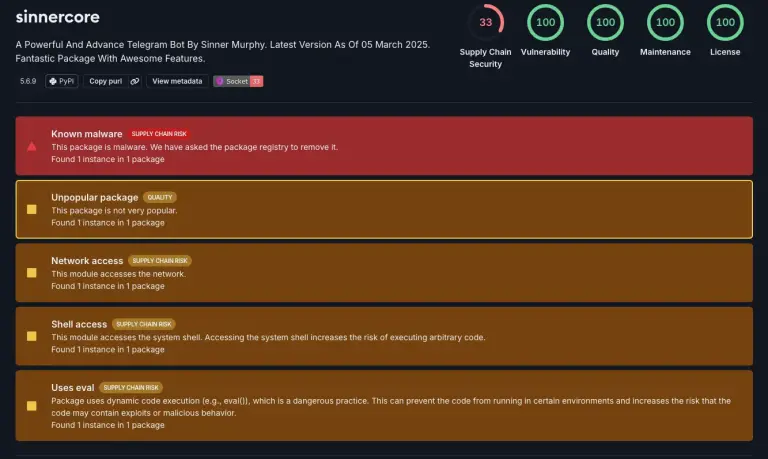
Threat actors continue to exploit popular open-source repositories as launchpads for the distribution of malicious code. This...
Since February 2024, the Chrome Web Store has been hosting malicious browser extensions disguised as useful utilities,...
Every smartphone owner knows the first essential step with a new device: enabling screen lock. Most users...
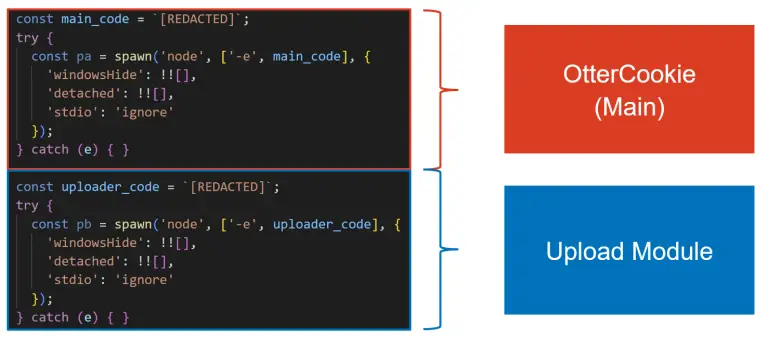
The North Korean cyber-espionage group behind the Contagious Interview campaign continues to evolve its multifunctional malware, OtterCookie—a...
An unusual social engineering attack was recently discovered on the website of iClicker, a widely used educational...
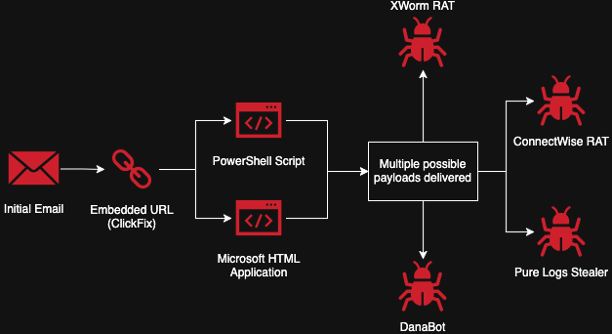
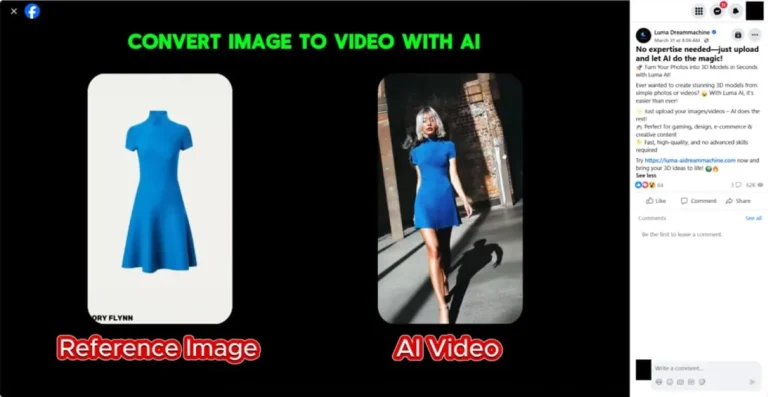
Fake AI-powered video generation platforms have emerged as a new front for disseminating a dangerous malware strain...
Law enforcement authorities have dismantled a botnet that, for over two decades, had infected thousands of routers...
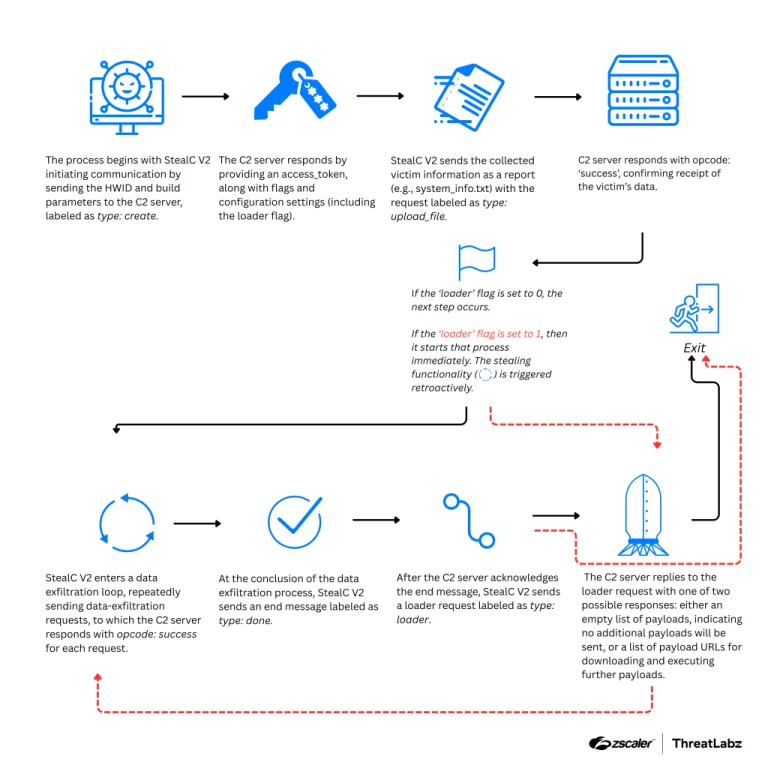
The widely used StealC malware, actively deployed in cyberattacks for data theft and the delivery of secondary...
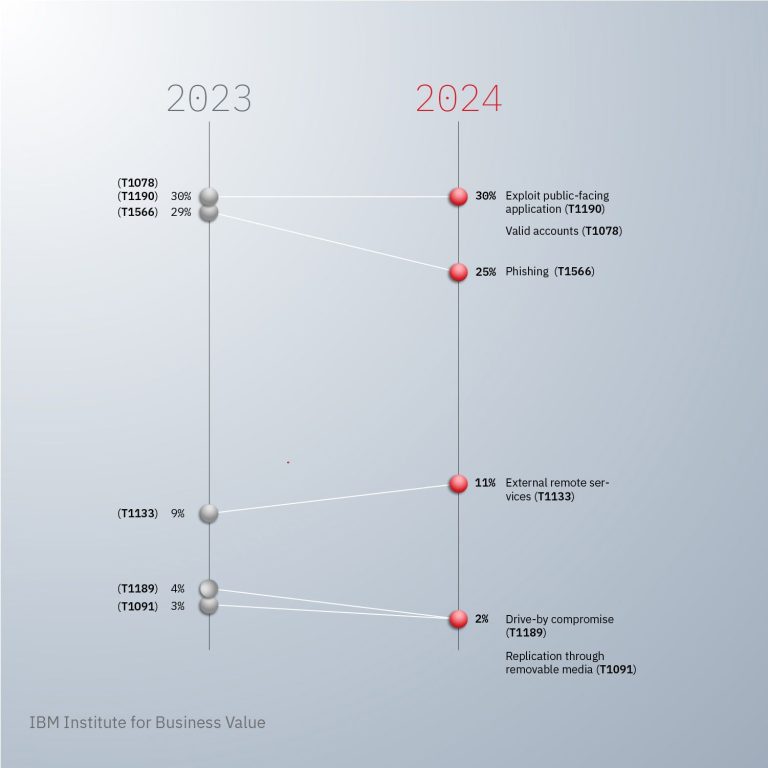
Attacks leveraging infostealers delivered through phishing emails are surging at an alarming pace. According to a recent...
One of the alleged operators behind the SmokeLoader malware has found himself at the center of a...