Hospitals in the states of Maine and New Hampshire have experienced severe operational disruptions following a cyberattack...
cybersecurity
In the cybersecurity industry, each major player has long relied on its own nomenclature for threat groups...
Beginning August 1, 2025, the Google Chrome browser will cease to automatically trust digital certificates issued by...
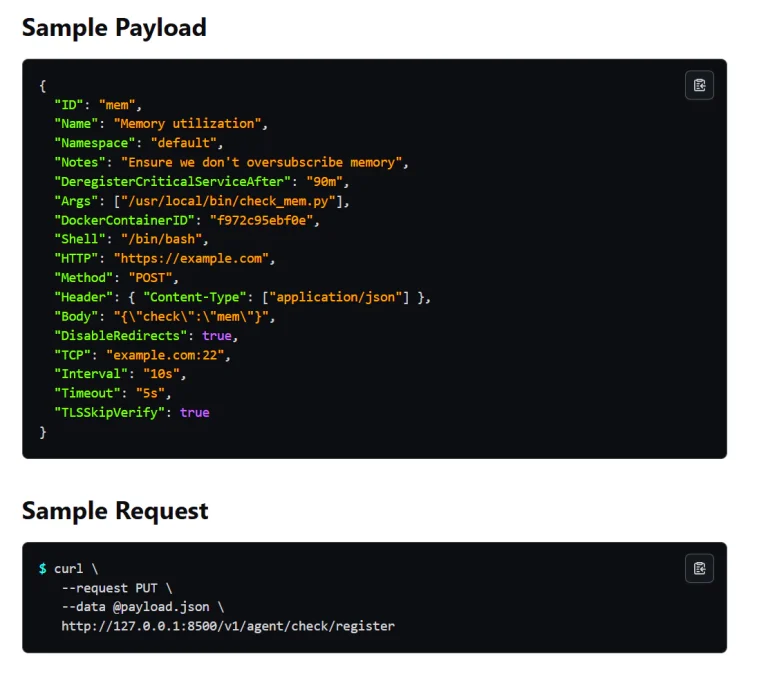
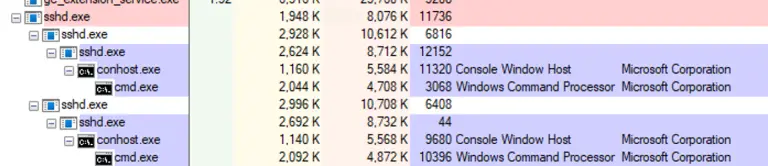
Cybersecurity experts have uncovered a new wave of covert cryptocurrency mining attacks targeting publicly accessible DevOps servers....
Each year—especially in the lead-up to major holidays—the topic of “juice jacking,” the surreptitious theft of data...
Smartphones manufactured by Ulefone and Krüger&Matz have been found to harbor critical vulnerabilities within their pre-installed applications—flaws...
Google has released an unscheduled update for the Chrome browser, addressing three security vulnerabilities—one of which is...
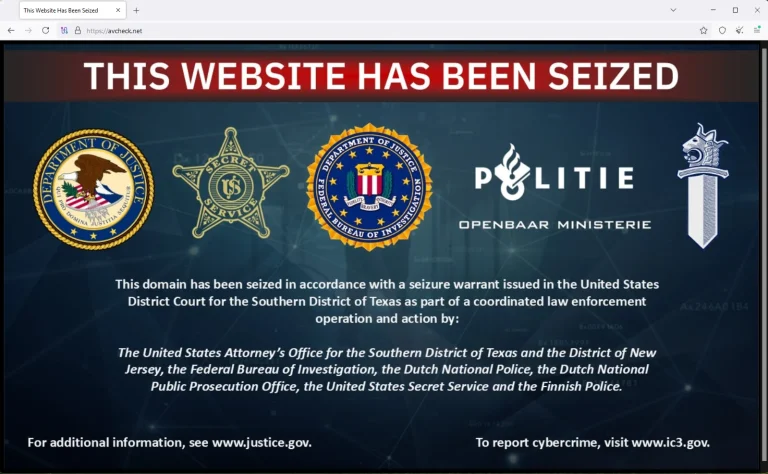
One of the most infamous underground services catering to cybercriminals—AVCheck—has come to an end. Its primary domain,...
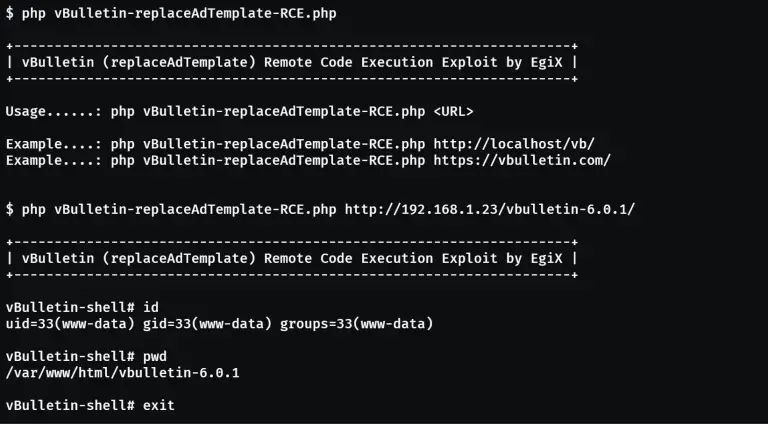
Critical security flaws have once again been discovered in popular vBulletin forums—vulnerabilities that allow for arbitrary code...
The technical details of one of the most perilous vulnerabilities of 2025—CVE-2025-20188—have now been made publicly available....
Automotive giant Volkswagen Group has unexpectedly appeared on a darknet leak site operated by the ransomware collective...
Linux 6.16 Revitalizes Confidential Computing with Major Trusted Security Manager (TSM) Enhancements


Linux 6.16 Revitalizes Confidential Computing with Major Trusted Security Manager (TSM) Enhancements
At the end of 2023, the long-anticipated feature for unified handling of attestation reports in confidential computing...
Two information disclosure vulnerabilities have been identified in Linux systems, including Ubuntu, Red Hat Enterprise Linux, and...
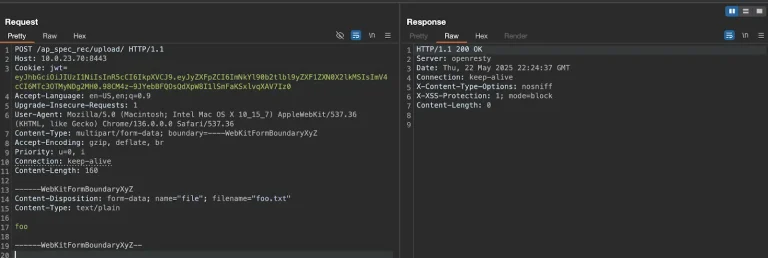
The remote management functionality of Azure Arc, designed to centralize administration across hybrid infrastructures, has proven unexpectedly...
Australia is ushering in a new chapter in its battle against cybercrime: under recently enacted legislation, major...