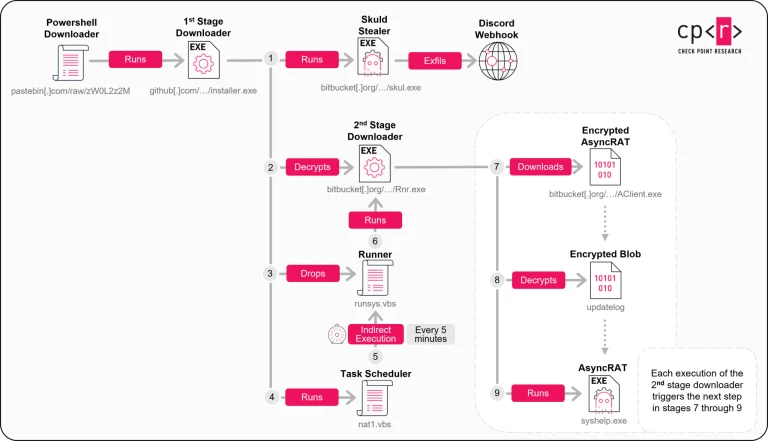
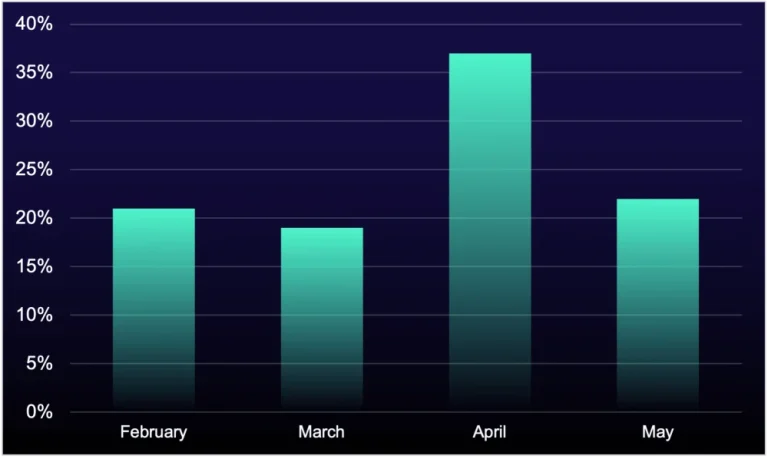
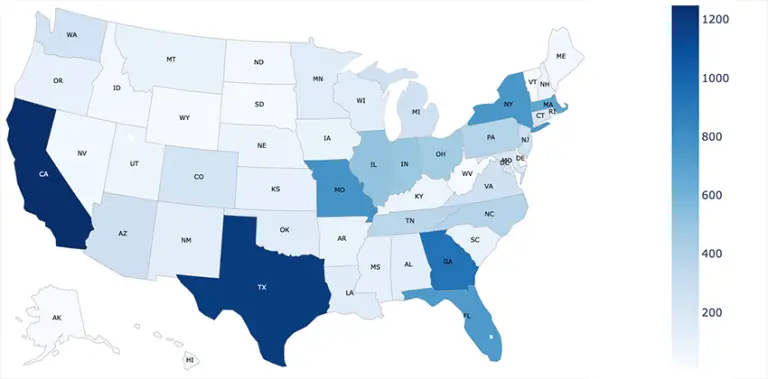
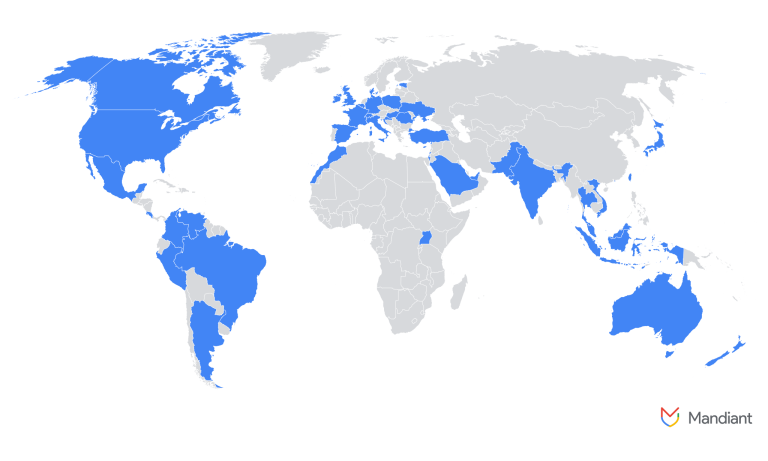
Cybercriminals have devised a cunning method to transform outdated Discord server links into digital traps: a newly...
cybersecurity
Jake Gallen was more than just a familiar face in the NFT scene—he had become a symbol...
The South Korean platform Yes24, the nation’s largest online ticketing service and a favored destination among K-pop...
The criminal syndicate behind the Fog malware has adopted an unorthodox arsenal of tools for its campaigns,...
Researchers from HiddenLayer have unveiled a novel attack on language models that can bypass built-in moderation and...
Apple has quietly updated the security release notes for iOS 18.3.1, revealing that it has patched a...
Modern smartphones have transcended their original role as mere communication tools — they have become gateways for...
Despite the public collapse of the Black Basta syndicate following the leak of its internal chat logs...
Bitsight has uncovered over 40,000 internet-connected surveillance cameras left completely unprotected—many of which could be accessed in...
GPS trackers manufactured by the Chinese company SinoTrack have been found vulnerable to exploitation due to two...
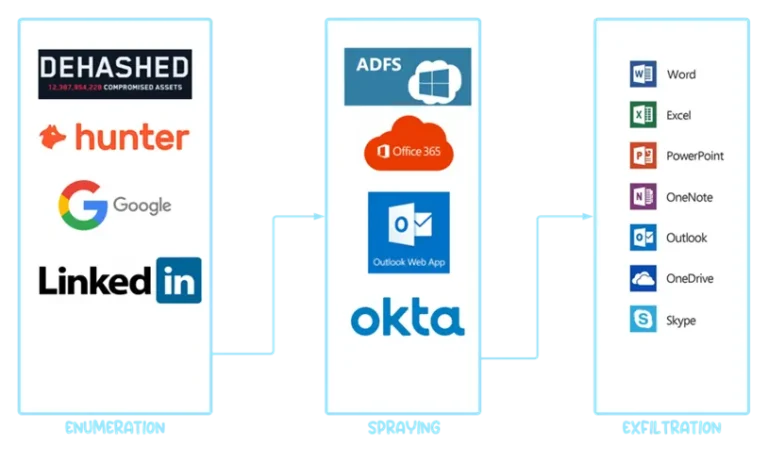
Hackers have compromised tens of thousands of corporate Microsoft Entra ID accounts by exploiting a tool originally...
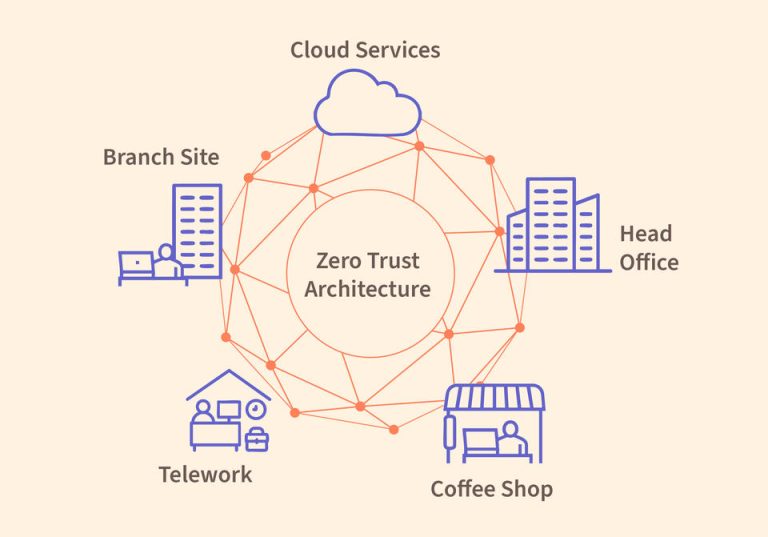
Traditional models for securing corporate networks are no longer adequate in the face of modern realities. In...
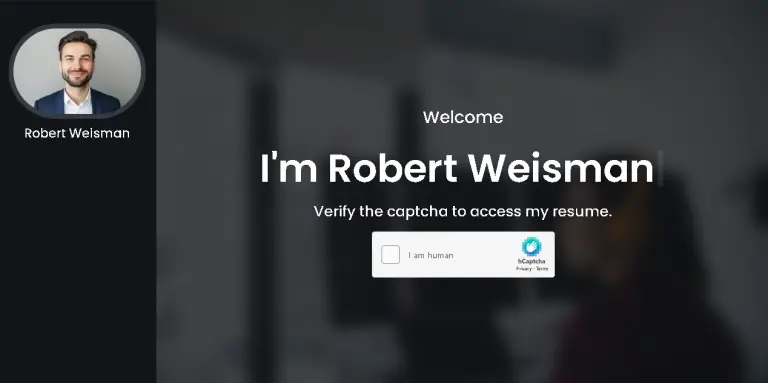
The financially motivated hacking collective FIN6 has resurfaced with a sophisticated phishing campaign that leverages counterfeit resumes...
Cybersecurity specialists at Trellix have uncovered a previously undocumented malware strain written in Rust, dubbed Myth Stealer,...
Beginning in July 2025, Microsoft will automatically block email attachments with the extensions .library-ms and .search-ms in...