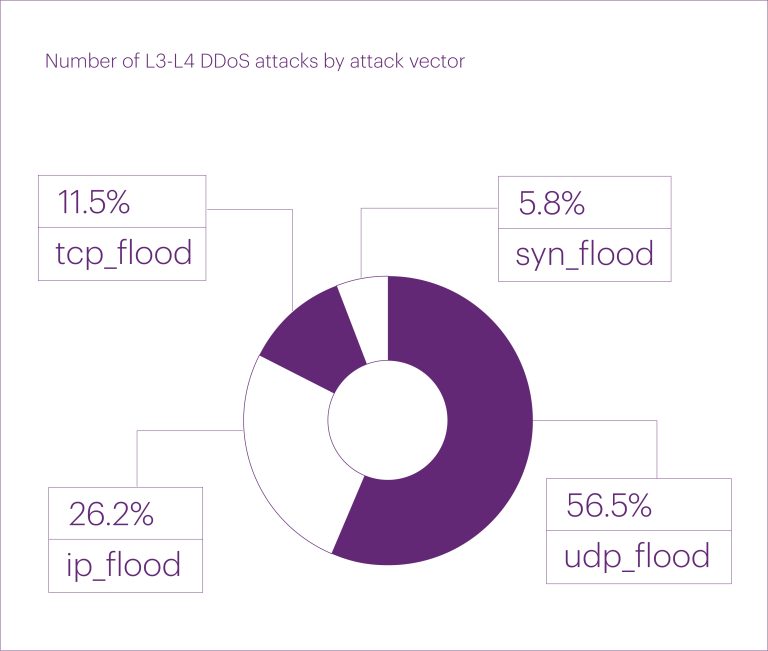
Credential theft has surpassed email phishing as the most prevalent initial access vector in 2024. For the...
cybersecurity
Outdated devices with high-speed internet have increasingly become liabilities to global cybersecurity—a trend starkly illustrated in 2025....
Microsoft has published the second report on the progress of its Secure Future Initiative (SFI) — the...
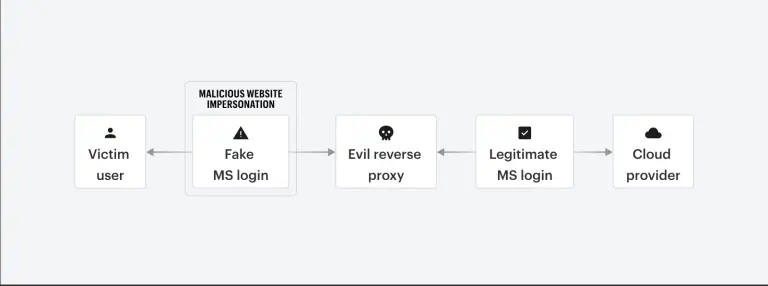
In a recent study conducted by specialists at Varonis, researchers revealed a subtle yet highly effective method...
Despite facing resistance, the Pakistan Telecommunication Authority (PTA) continues to advance efforts to regulate VPN applications, mandating...
The certificate authority SSL[.]com has found itself at the center of a controversy after a cybersecurity researcher...
Cybersecurity researchers have uncovered a zero-day vulnerability in the widely used utility WinZip, which allows adversaries to...
The group known as Lotus Panda, believed to be linked to China, has once again drawn the...
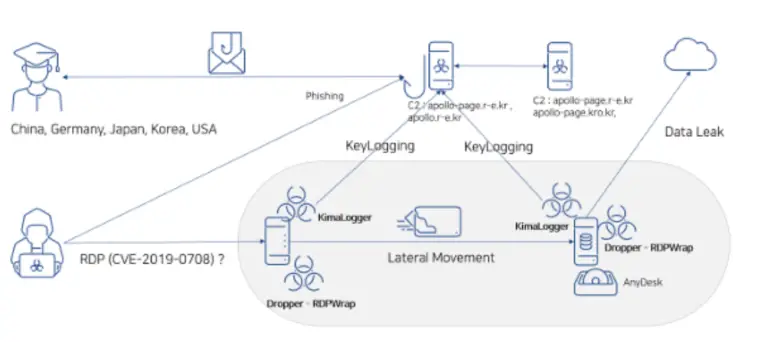
A cybercriminal campaign linked to the North Korean threat group Kimsuky has once again drawn the attention...
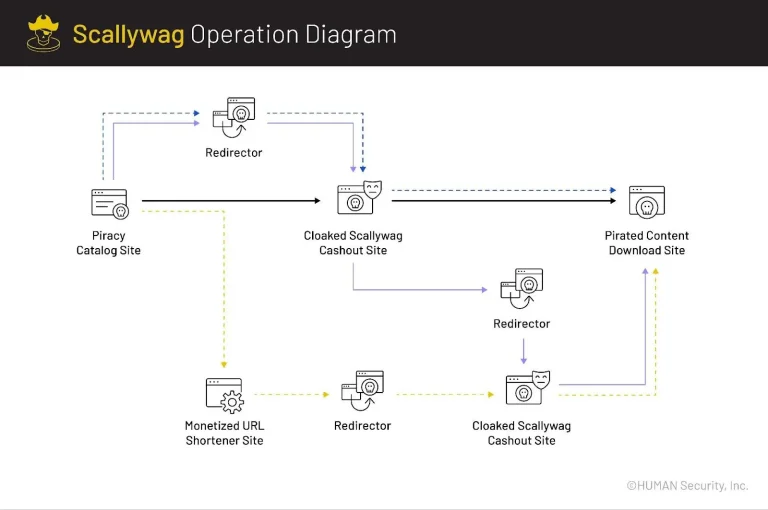
The fraudulent Scallywag scheme, built upon specially crafted WordPress plugins, had long been generating billions of ad...
The Cybersecurity and Infrastructure Security Agency (CISA) is discontinuing the use of two pivotal cyber threat analysis...
Zoom’s remote access functionality has become the foundation of a new, highly sophisticated attack campaign targeting professionals...
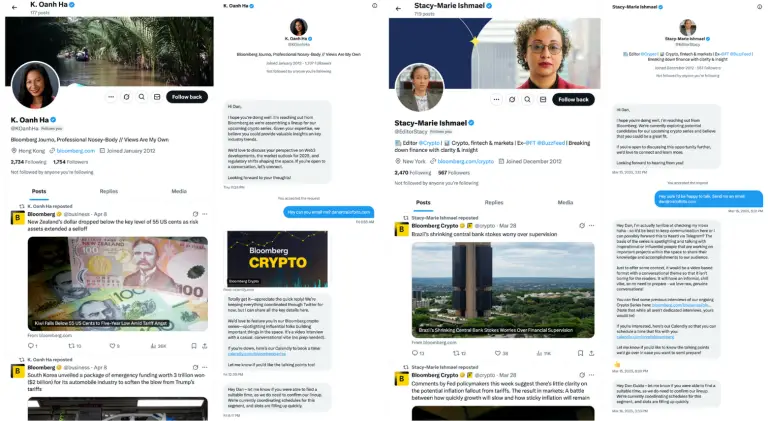
Hackers have discovered a method to deceive users by sending emails that appear to originate directly from...
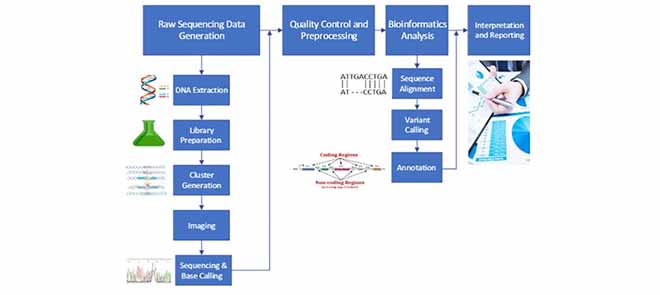
Scientists are sounding the alarm: DNA sequencing technologies may become the next prime target for cyberattacks. The...
ASUS has issued a warning regarding a critical vulnerability in its routers, specifically linked to the AiCloud...