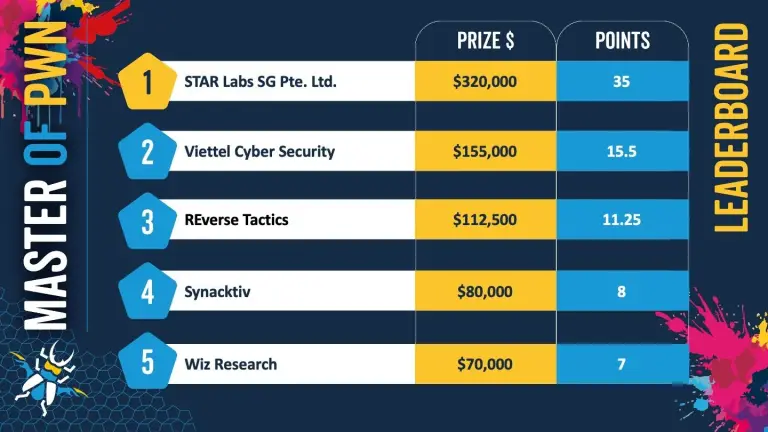
Pwn2Own 2025 has concluded in Berlin, marking one of the most significant showcases of zero-day vulnerabilities in...
cybersecurity
Hackers have compromised the official website of RVTools—a widely used utility for managing VMware virtual infrastructures—and replaced...
The developers have released updates for several versions of the Linux kernel, including 6.14.7 and other actively...
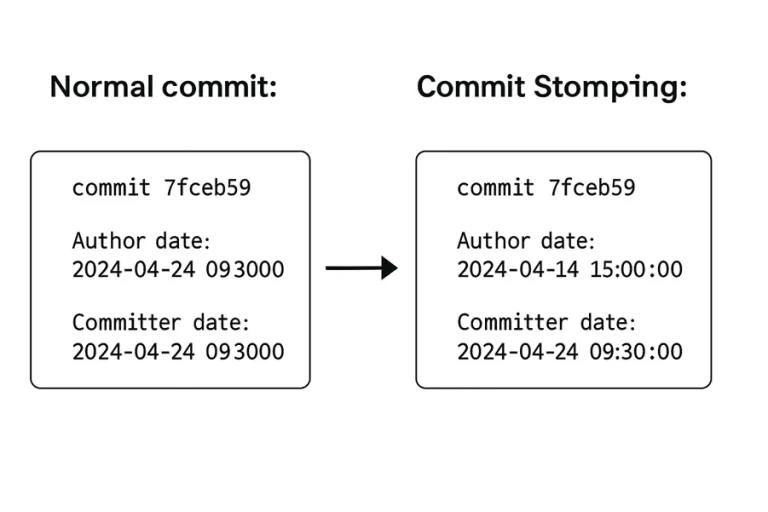
A method for concealing change history has been uncovered in Git, capable of misleading even seasoned digital...
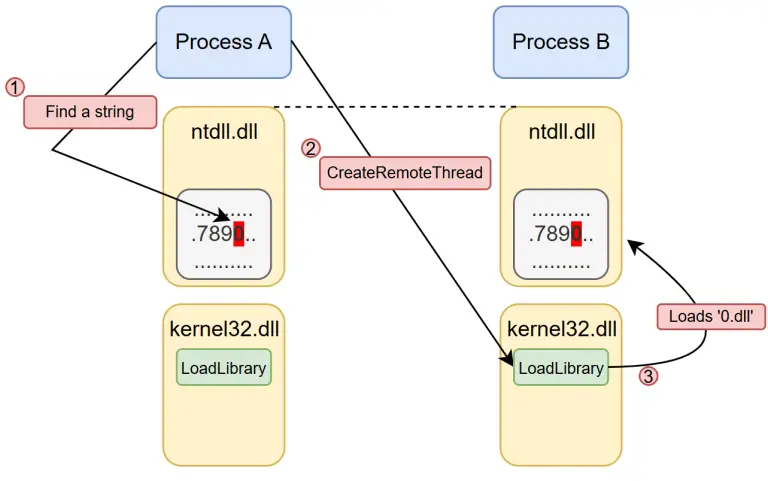
Recent research has demonstrated novel techniques for injecting malicious code into Windows processes without relying on traditional...
Japan has officially abandoned its longstanding restraint in cyberspace. On May 16, a landmark law was enacted,...
At the ongoing Pwn2Own hacking tournament in Berlin, a historic milestone was achieved: elite cybersecurity experts successfully...
On the opening day of the Pwn2Own 2025 hacking competition in Berlin, researchers succeeded in compromising Windows...
The FBI has issued a warning about a new wave of attacks involving voice-based deepfakes targeting U.S....
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has expanded its Known Exploited Vulnerabilities (KEV) catalog, adding...
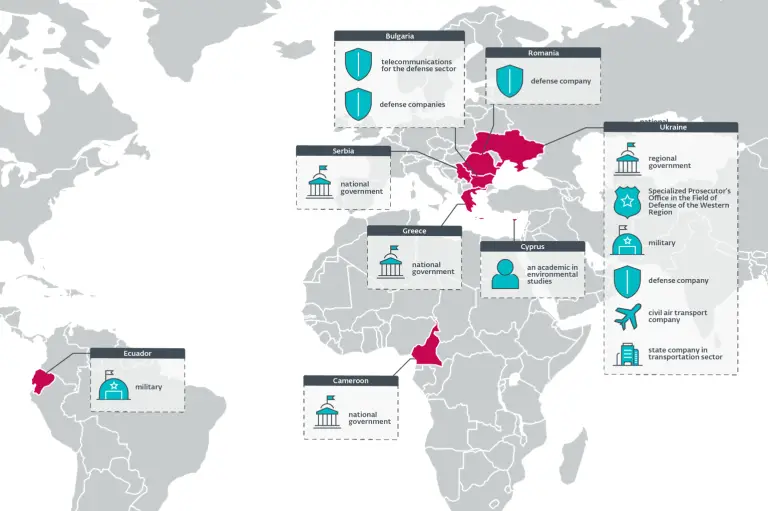
Since 2023, the hacker collective APT28 has been conducting a sweeping cyber-espionage operation known as RoundPress, aimed...
Malicious actors have once again targeted the npm ecosystem, this time through a package named “os-info-checker-es6”, which...
The House of Dior has suffered a data breach involving the personal information of customers from its...
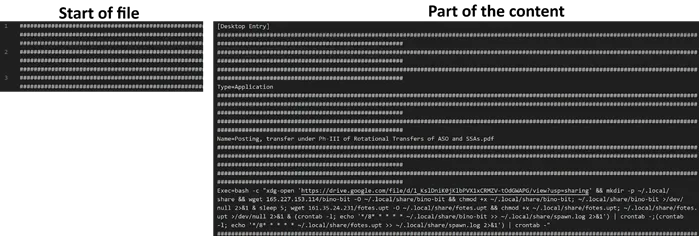
Google Threat Intelligence has published a new set of advanced threat-hunting techniques aimed at uncovering malicious .desktop...
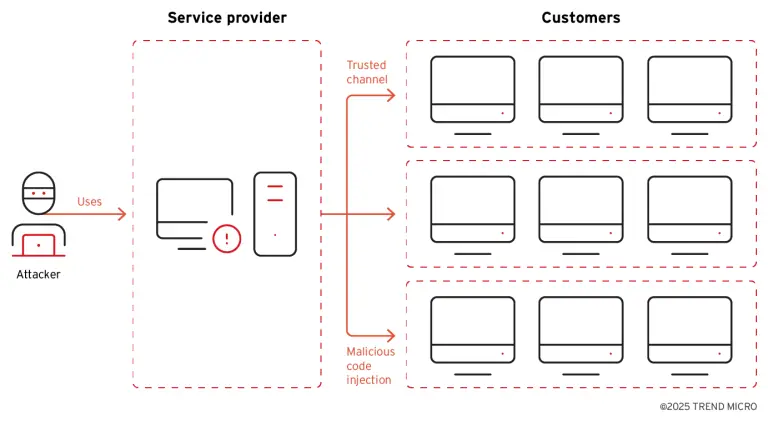
The group known as Earth Ammit, affiliated with Chinese-speaking APT entities, conducted two waves of targeted attacks...