Amid a surge in increasingly sophisticated software supply chain attacks, cybersecurity experts have identified a new wave...
Cloud Security
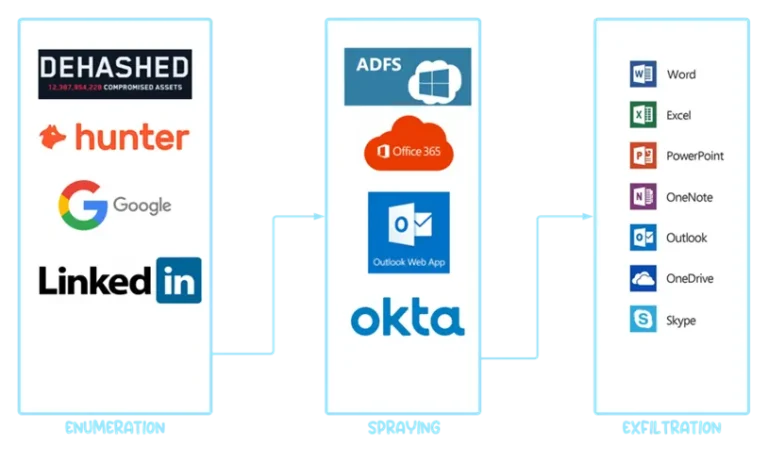
Hackers have compromised tens of thousands of corporate Microsoft Entra ID accounts by exploiting a tool originally...
Traditional models for securing corporate networks are no longer adequate in the face of modern realities. In...
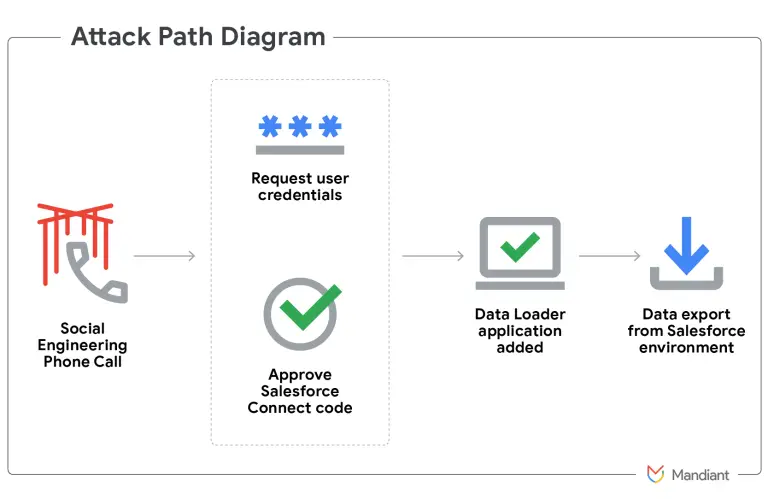
Hackers affiliated with the group UNC6040, tracked by Google’s Threat Intelligence Group, have been implicated in a...
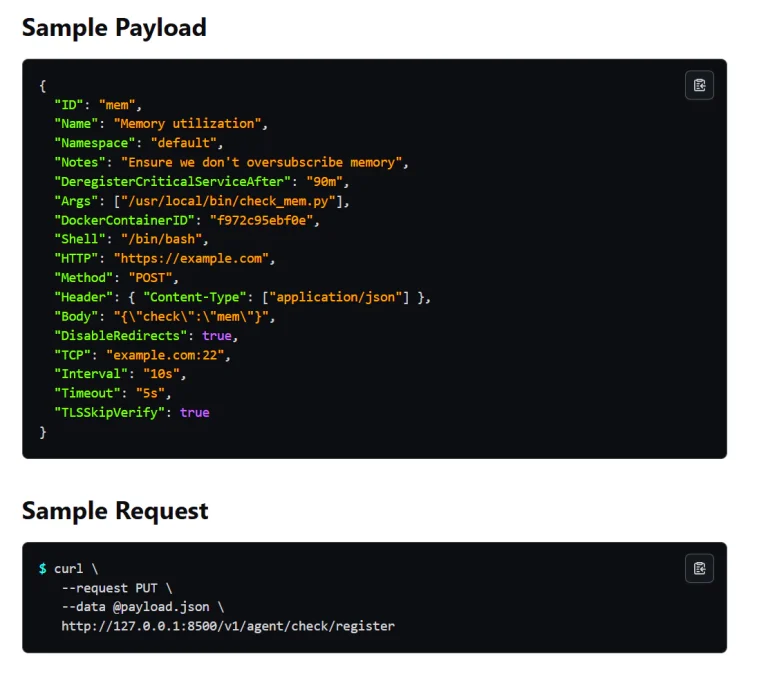
Cybersecurity experts have uncovered a new wave of covert cryptocurrency mining attacks targeting publicly accessible DevOps servers....
The remote management functionality of Azure Arc, designed to centralize administration across hybrid infrastructures, has proven unexpectedly...
ConnectWise, a company specializing in software for managing IT infrastructure, has disclosed a security breach within its...
A cyberattack targeting the cloud infrastructure of Commvault has resulted in unauthorized access to customer data, specifically...
Experts have uncovered significant risks linked to default access policies within Amazon Web Services’ cloud infrastructure. These...
Simplified application deployment in Kubernetes using Helm can lead to serious vulnerabilities if default configurations are left...
Microsoft has pledged to safeguard the data of its European clients — even in court — in...
A comprehensive study conducted by Rubrik Zero Labs has confirmed that in 2024, nearly 90% of IT...
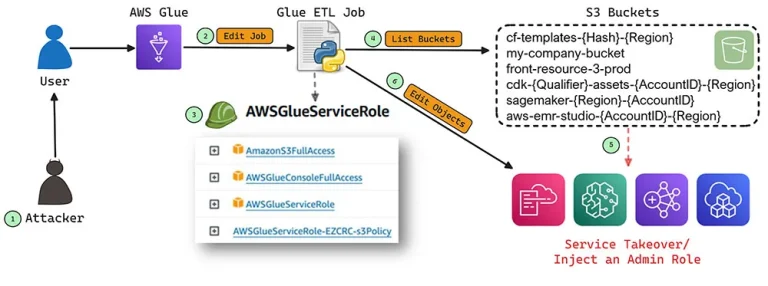
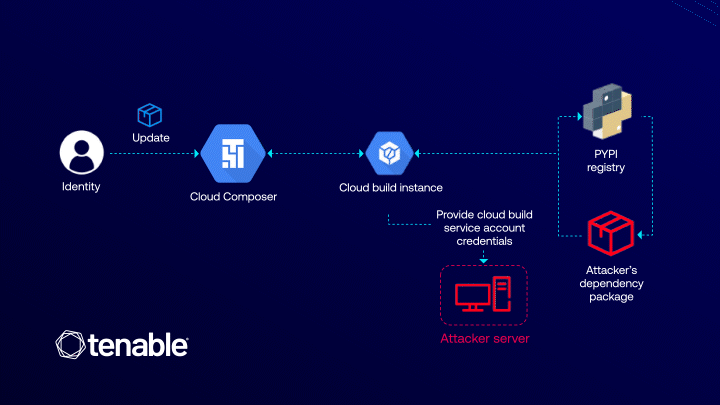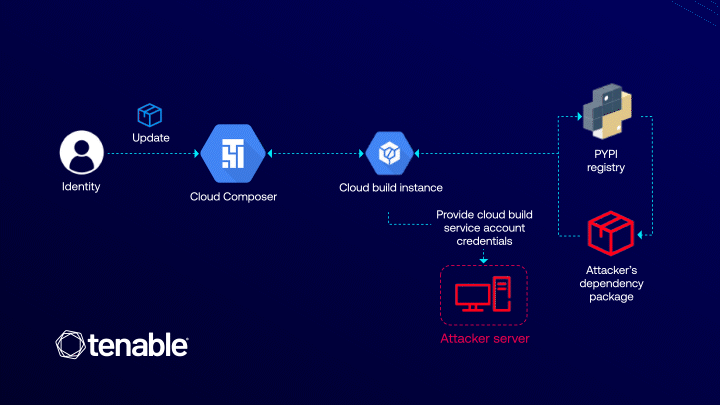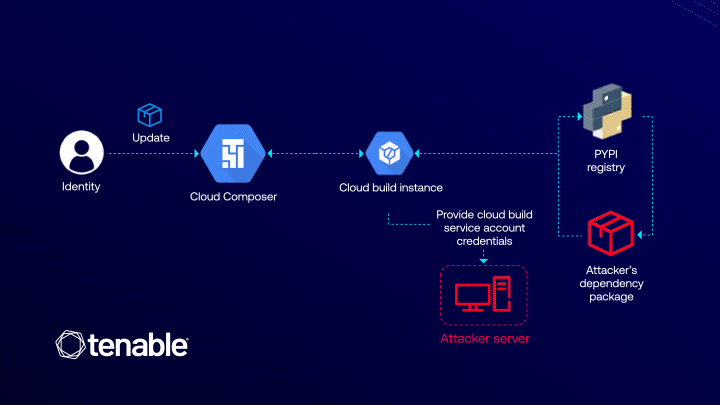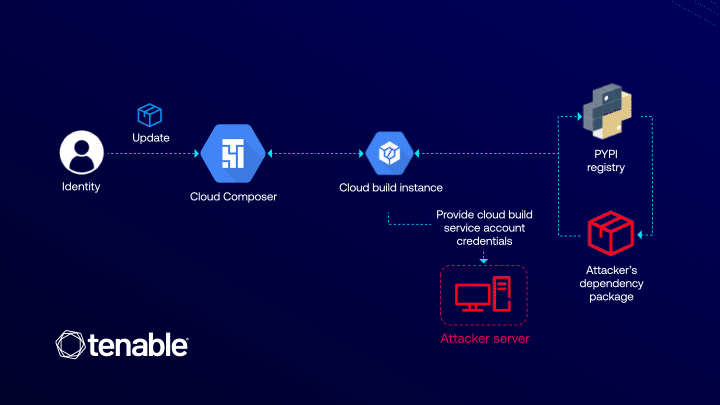
The ConfusedComposer vulnerability, uncovered by researchers at Tenable, stands as yet another illustration of how the internal...
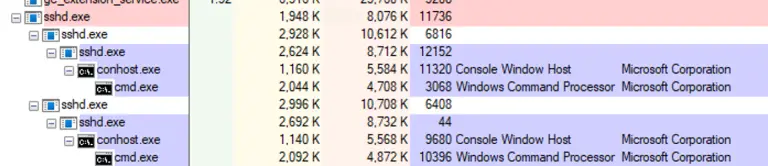
In recent times, cryptominers have begun to employ increasingly unconventional tactics, and a newly uncovered malicious campaign—identified...
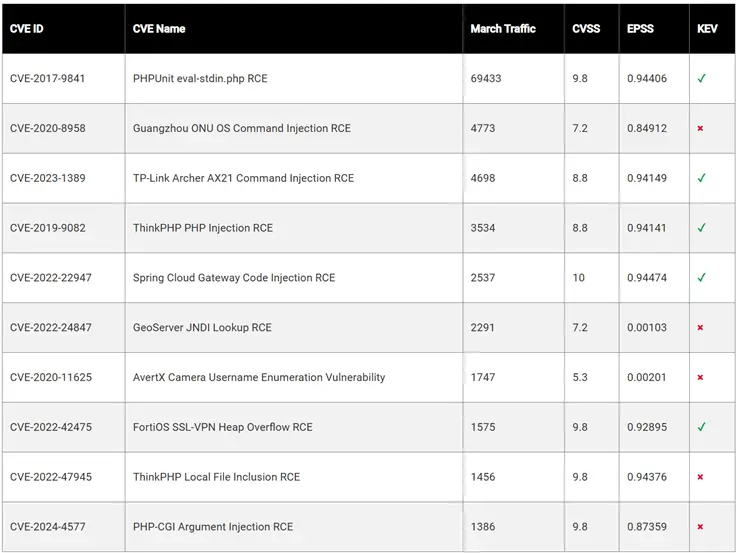
March 2025 witnessed a renewed surge in cybercriminal activity, concentrated along two principal vectors: mass scanning of...