Five years ago, on May 23, 2020, the jailbreak community witnessed a historic precedent: the public release of the tachy0n exploit—an authentic 0-day vulnerability in iOS 13.5 that enabled kernel-level privilege escalation. It marked the last known instance in which a modern version of iOS was compromised prior to the release of an official patch. Just nine days later, Apple issued a security update, and a month and a half after that, a fork of the exploit named tardy0n emerged. Today, this episode is seen as the dividing line between Apple’s old and new approaches to system security.
Tachy0n targeted a vulnerability in the lio_listio system call, which handles asynchronous file operations. The flaw stemmed from a race condition between two threads that could attempt to free the same lio_context structure. If the operation completed too quickly, this structure could be freed twice, allowing the attacker to reclaim that memory space for malicious purposes and manipulate its contents.
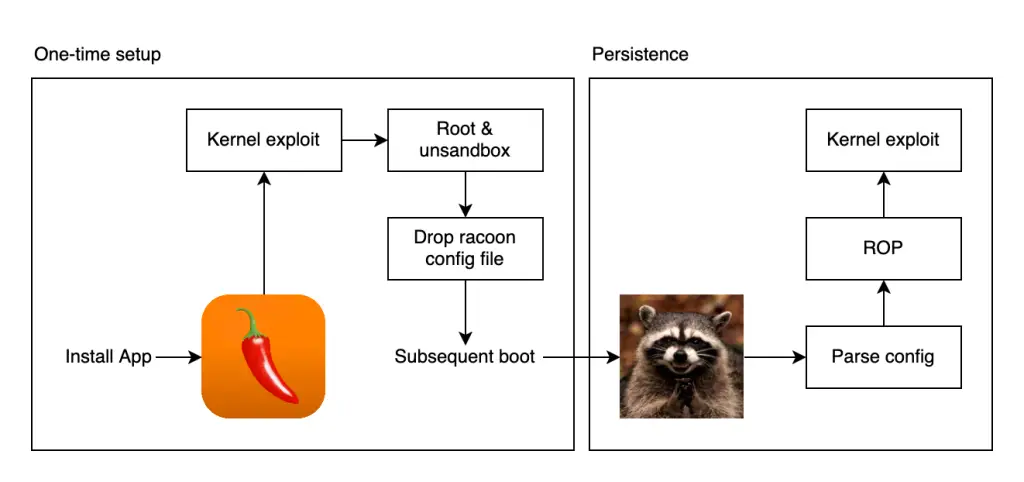
Notably, the bug was not an entirely new discovery. Before being published as a 0-day, it had already been used by the same team for a 1-day exploit in the Spice jailbreak, which targeted iOS 11. It was deployed in two variants—within an application and a system process called racoon. The latter was particularly noteworthy due to its elevated privileges and access to system-level functions such as sysctl, which greatly facilitated the retrieval of kernel object addresses.
The exploit was crafted in the classic pre-iOS 14 fashion: through race conditions, hijacking mach_port structures, descriptor manipulation, and controlled object spraying using IOSurface::setValue. The kernel could be tricked into allowing two different OSData objects to point to the same buffer, which was then gradually overwritten—first with pointers, and then with fabricated kernel structures.
A particularly inventive step involved leveraging an IOBufferMemoryDescriptor obtained via the AGX interface (IOAcceleratorFamily2) to allocate a predictable memory region with a known address. This allowed the placement of forged task and mach port structures within the kernel, granting full system control. To ensure that the memory became resident within the kernel, the author invoked the processSidebandBuffer method with a valid stub in the structure—an approach that triggered a fault and forced physical page initialization.
The exploit’s release elicited an immediate reaction from the security community. Within four hours, Brandon Azad of Project Zero identified and documented the vulnerability, and nine days later, Apple issued a targeted patch. Interestingly, the bug’s resurgence was tied to Apple’s earlier attempt to fix a separate memory leak—an issue previously identified and resolved in iOS 12. All signs suggest the reappearance of the vulnerability was the result of careless code merges within XNU, executed without proper regression testing.
The tachy0n story laid bare systemic shortcomings in Apple’s security model at the time. While some engineers attempted to hunt down and fix vulnerabilities manually, others—like the creator of unc0ver—achieved breakthroughs through simpler yet labor-intensive techniques such as regression testing of known flaws. That’s how this bug was ultimately rediscovered.
However, with the release of iOS 14, everything changed. Apple moved away from piecemeal fixes and began securing entire exploitation paradigms. The kalloc and zalloc allocators were rearchitected, kheaps were introduced to segregate user data from kernel objects, and the concept of “sequestering” was deployed to isolate object types. Additional measures such as random guard pages and deeper memory randomization rendered traditional object overlap techniques obsolete and made exploitation significantly more complex and unreliable.
Furthermore, Apple began fortifying individual structures frequently targeted by exploits. Kernel message structures were cryptographically signed, pipe buffers were protected by PAC (Pointer Authentication Code), and attempts to misuse foreign object types often led to immediate kernel panics. As a result, exploit development became so arduous that no complete public exploits for iOS 17 or 18 have surfaced, despite reports of successful attacks in the wild.
The tachy0n exploit is now viewed as the swan song of an era when jailbreaking was a mainstream pursuit and kernel LPEs could be achieved through diligent review of bug trackers. Today, on the threshold of iOS 19, even veteran researchers are confronted with a near-impenetrable wall of isolation layers, code signatures, PAC enforcement, and restartable runtime checks.
And yet, this is precisely why detailed accounts of such exploits—regardless of their age—remain invaluable: as monuments to a bygone era and as encyclopedias of techniques that, though antiquated, may still illuminate the present.


