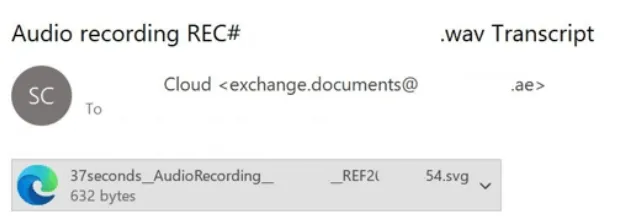
Experts at Kaspersky Lab have uncovered widespread phishing campaigns employing malicious attachments in SVG format. According to the company, these attacks target both individual users and organizations, with the primary objective of gaining unauthorized access to accounts on Google and Microsoft services. In March 2025 alone, the volume of such attacks surged nearly sixfold compared to the previous month, with over 4,000 phishing emails recorded since the beginning of the year.
The SVG format (Scalable Vector Graphics), designed to describe two-dimensional vector images using XML, also supports JavaScript and HTML integration—a feature that attackers have begun to exploit by embedding malicious scripts within these files to redirect victims to phishing websites.
The attack typically unfolds as follows: the victim receives an email with an SVG file attachment, which in reality is an HTML page disguised as a vector image. When opened in a browser, the user is presented with a seemingly legitimate interface featuring a button labeled “Listen to Audio File.” Clicking this button triggers a redirection to a counterfeit Google Voice page, where, instead of hearing audio, the user is prompted to enter their login credentials. These credentials are then captured and exfiltrated by the attackers.
In an alternative variant of the campaign, the attachment is disguised as a document requiring a signature. Here, the SVG file contains JavaScript that automatically redirects the user to a spoofed Microsoft login page. Upon entering their credentials, the victim unknowingly hands over access to the attackers.
According to Kaspersky Lab, phishers are actively experimenting with various attachment formats, and in its current form, the SVG-based phishing technique remains relatively simple: the malicious code is either embedded directly within the file or used as a redirector to external phishing portals. However, researchers caution that this method could evolve into more advanced, targeted attacks in the future.


