In the first quarter of 2025, cyberattacks leveraging 159 unique vulnerabilities with assigned CVE identifiers were recorded—a slight increase compared to the end of the previous year, which saw 151 such vulnerabilities. Strikingly, nearly one-third of these flaws—28.3%—were actively exploited within just 24 hours of public disclosure, underscoring the rapid transformation of technical information into attack tools.
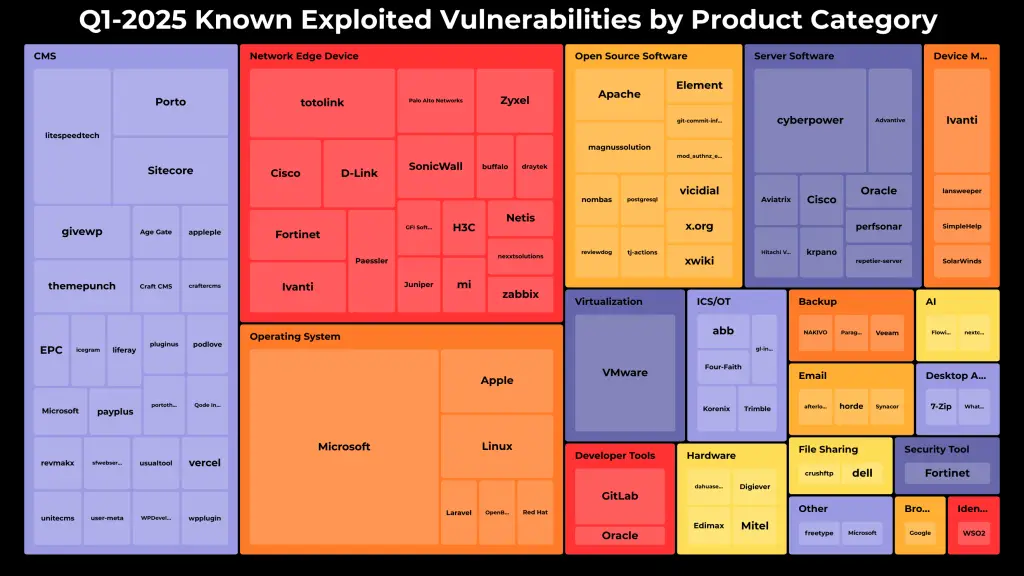
Forty-five vulnerabilities were weaponized on the very first day following disclosure. An additional fourteen were exploited within a month, and another forty-five within the span of a year. Content Management Systems (CMS) emerged as the most frequent targets, hosting the largest share of exploited vulnerabilities, followed by perimeter network devices, operating systems, open-source components, and server software.
Among vendors whose products were subjected to attacks, Microsoft topped the list, with its Windows operating system implicated in fifteen incidents. Other notable mentions include Broadcom VMware (six vulnerabilities), Cyber PowerPanel (five), LiteSpeed Technologies (four), and TOTOLINK routers (four).
According to VulnCheck, more than eleven critical vulnerabilities with known exploitation are discovered weekly, amounting to fifty-three per month. Meanwhile, the CISA Known Exploited Vulnerabilities catalog expanded by eighty entries over the quarter, though only twelve lacked previously confirmed exploitation—highlighting how swiftly vulnerability information reaches malicious actors.
Approximately 26% of all identified vulnerabilities remain under review in the National Institute of Standards and Technology’s (NIST) National Vulnerability Database, while 3% have been designated as “Deferred”—a new classification introduced in 2025.
Verizon’s latest Data Breach Investigations Report indicates that the use of vulnerabilities as initial attack vectors has surged by 34%, now accounting for one-fifth of all recorded incidents. This trend is mirrored in Mandiant’s findings: for the fifth consecutive year, exploits remain the most common method of initial system infiltration, surpassing phishing, which has now ceded second place to the use of stolen credentials.
Mandiant further reports that one-third of all attacks in 2025 began with vulnerability exploitation—a slight decline from 38% in 2023, yet close to the 32% figure observed in 2022. Despite heightened attacker activity, defensive measures show incremental improvement: the median dwell time—how long intruders remain undetected—has increased by only a single day, now averaging eleven days.
This evolving landscape underscores the critical need for not only timely patching but also continuous vulnerability monitoring, especially for publicly exposed services and network devices. With each passing quarter, the window between vulnerability disclosure and exploitation narrows, turning even brief delays in updating into significant security risks.


