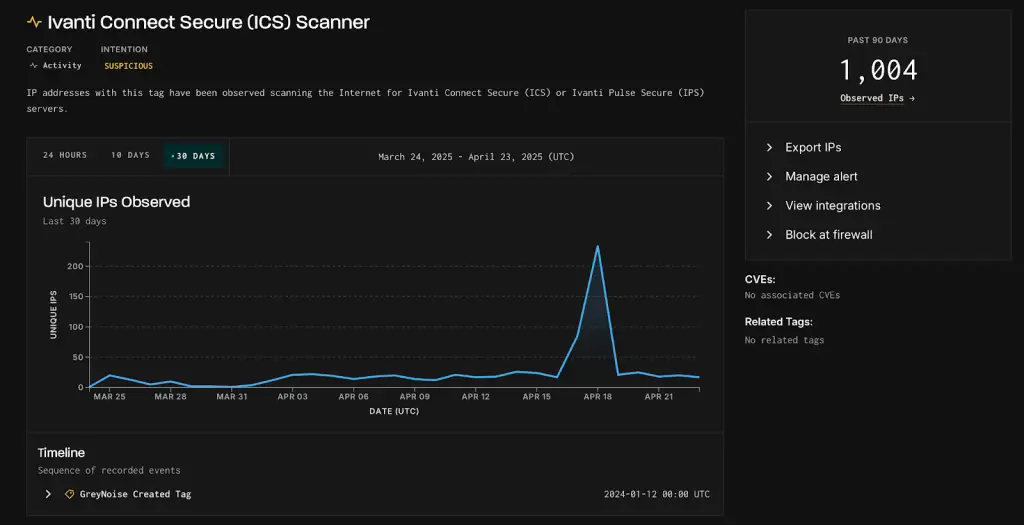
Users of Ivanti’s VPN services should remain vigilant: according to GreyNoise, a company that monitors internet activity, the number of IP addresses scanning Ivanti Connect Secure and Pulse Secure systems has surged by 800 percent over the past week. Experts explain that such spikes often precede either the active exploitation of vulnerabilities or their public disclosure.
Typically, the number of unique IP addresses scanning Ivanti’s VPN services does not exceed 30 per day and sometimes remains in the single digits. However, on April 18, GreyNoise recorded a dramatic increase: 234 IP addresses were simultaneously scanning Ivanti endpoints. For comparison, over the past 90 days, a total of 1,004 unique IP addresses had been observed, with nearly a quarter of all activity concentrated in a single day.
Of these 1,004 IP addresses, GreyNoise classified 634 as “suspicious,” 244 as “malicious,” and only 126 as “benign.” Analysts believe that such a sharp rise in scanning activity may indicate coordinated reconnaissance ahead of a potential attack.
The security posture of Connect Secure has recently drawn increasing scrutiny from cybersecurity experts. Although there is no confirmed evidence of new vulnerabilities at this time, GreyNoise notes that similar activity spikes have historically preceded the disclosure of new flaws. Ivanti Connect Secure remains an attractive target for threat actors due to its critical role in facilitating remote access to corporate networks.
In response to inquiries from The Register, Ivanti reminded users that support for Pulse Secure devices and older Connect Secure 9.1 Rx versions has ended. The company emphasized that products reaching end-of-support status are particularly vulnerable to attacks exploiting known vulnerabilities, as they no longer receive security updates. Ivanti strongly urges users to migrate to supported versions without delay and noted that it is actively taking measures to encourage customer upgrades.
Meanwhile, GreyNoise advises administrators to diligently review event logs for suspicious login attempts and to promptly apply all available security updates.
The atmosphere of concern is further intensified by Ivanti’s history of being targeted in serious attacks over recent years. In January 2025—marking the second consecutive year—Connect Secure services were attacked using zero-day vulnerabilities. Two new vulnerabilities were disclosed just days after the New Year, with subsequent investigations revealing that exploits had been in use since mid-December. One of these vulnerabilities (CVE-2025-0282) received a critical severity rating of 9 out of 10. This week, Japan’s incident response team JPCERT confirmed successful attacks leveraging this flaw.
Compounding matters, there were also reports during January of Ivanti devices being infected with a new strain of malware known as DslogdRAT. Although definitive attribution remains elusive, experts suspect a link to the Chinese hacking group UNC5221, which had orchestrated similar attacks in January 2024. That earlier incident was exacerbated by Ivanti’s delays in issuing patches, leaving many customers unprotected for weeks after the vulnerabilities had been disclosed.
Ivanti later acknowledged the 2024 incident as “a lesson learned” and, in April of that year, pledged to overhaul its security practices, making secure development principles a central tenet of its processes.


