Attacks leveraging infostealers delivered through phishing emails are surging at an alarming pace. According to a recent report by IBM X-Force, the volume of such malware-laden campaigns has increased by 84% in just the past week. This is not merely a spike in activity — it signals a fundamental shift in cybercriminal tactics, as adversaries increasingly turn to more sophisticated and covert infiltration methods.
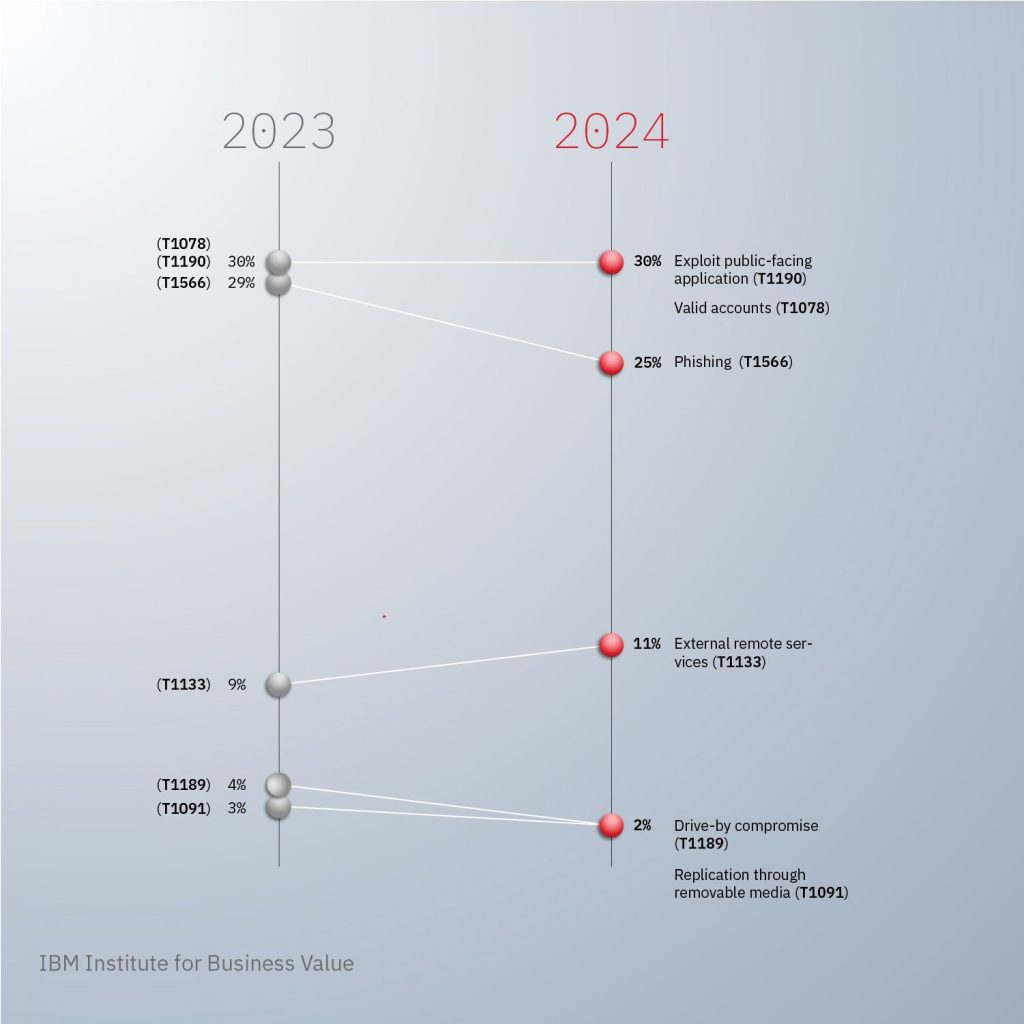
Phishing emails have long been a favored vector for breaching corporate defenses. However, whereas they once primarily served to deploy ransomware, the spotlight has now shifted to infostealers — stealthy programs designed to silently harvest credentials, financial information, and other sensitive data. Victims often remain unaware of the compromise. Common payloads now include AgentTesla, FormBook, and Strela Stealer, embedded in seemingly innocuous attachments and delivered via ever more refined schemes.
One of the driving forces behind this surge is the aggressive exploitation of cloud services. Threat actors increasingly conceal phishing pages and malicious files within platforms like Microsoft Azure Blob Storage. The legitimate appearance of these services deceives users and enables the malware to slip past automated security mechanisms. This trend is particularly pronounced in Latin America, where such attack vectors have reached endemic proportions.
Phishing is also being bolstered by more nuanced techniques. Malvertising and SEO poisoning allow adversaries to disguise malicious payloads as legitimate updates or utilities. These strategies are especially effective in regions with lower levels of cybersecurity maturity, where users and organizations are often ill-equipped to recognize or counter such subterfuge.
To confront this evolving wave of threats, traditional filters and antivirus solutions alone are no longer sufficient. Organizations must invest in comprehensive security awareness training, teaching employees to detect phishing lures, enforcing multi-factor authentication, and closely monitoring for anomalous behavior within systems. Increasingly, enterprises are also turning to AI-powered solutions capable of detecting threats in real time and responding swiftly to potential breaches.
The accelerating proliferation of phishing and infostealer campaigns starkly illustrates how rapidly the cybercriminal arsenal is advancing. The situation demands not merely a defensive posture, but a proactive and adaptive approach — for it is the speed of response and organizational agility that may ultimately determine resilience in an era of digital volatility.


