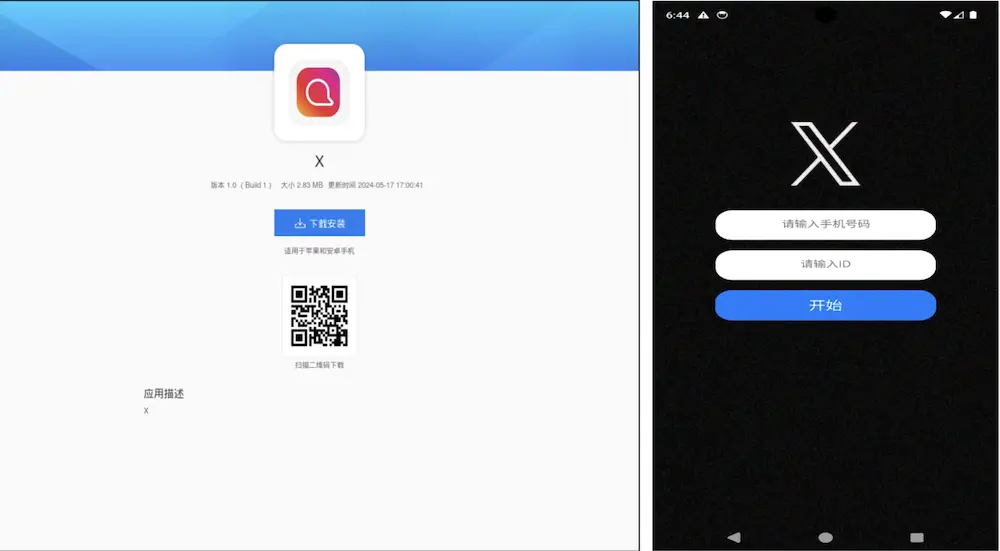
Distribution site and fake X app targeting Chinese-speaking users
Cybercriminals have devised a novel technique to conceal malicious code within Android applications, rendering it nearly impervious to detection by traditional antivirus tools. The McAfee Mobile Research team has identified campaigns that exploit .NET MAUI—a cross-platform framework developed by Microsoft—to craft malicious apps capable of evading detection on target devices. These applications disguise themselves as legitimate services while surreptitiously harvesting users’ personal data.
With the advent of .NET MAUI, developers can now create applications not only for Android and iOS but also for Windows and macOS. The transition from Xamarin to MAUI, completed in May 2024, has inadvertently opened new doors for cybercriminals. Rather than employing conventional DEX files or native libraries, .NET MAUI compiles code into compact binary “blobs” in C format. Since most antivirus engines are designed to scan traditional Android components, this novel structure allows malicious code to slip past standard defenses.
McAfee documented two campaigns employing this strategy. In the first, a malicious application poses as a legitimate service from the prominent Indian bank IndusInd. Upon launch, it prompts users to enter sensitive details such as their name, phone number, email, date of birth, and bank account information—all of which are promptly transmitted to the attacker’s server.
The malicious payload is embedded within blob files stored in the app’s “assemblies” directory, making it invisible during Java code analysis. The C-based source code is responsible for collecting and exfiltrating data, all while maintaining the facade of a standard banking app.
The second case involves a counterfeit social networking app targeting Chinese-speaking users. This variant is notably more sophisticated, employing a multi-stage dynamic code-loading mechanism. First, it decrypts an XOR-encrypted file, which subsequently loads a second payload encrypted with AES. Only in the third stage is the primary malware component—buried within MAUI’s C-layer—activated.
Rather than standard HTTP requests, data is exfiltrated via encrypted TCP sockets, thwarting typical traffic inspection techniques. Additionally, the application floods the AndroidManifest.xml file with dozens of meaningless and randomly generated permissions, thereby confusing static analysis tools and complicating reverse engineering efforts.
These malicious applications are primarily distributed through unofficial app stores and links shared via messaging platforms. In regions such as China, where access to Google Play is restricted, this tactic is especially prevalent. Analysts have identified numerous other apps—such as counterfeit dating platforms—employing identical techniques, suggesting a large-scale industrialization of this malware approach.
Researchers warn that this surge in threats signals a significant evolution in the development of mobile malware. The use of .NET MAUI as a wrapper, combined with multi-layered payload delivery, encrypted communication channels, and deliberately misleading permissions, renders these threats nearly invisible to conventional security solutions.
To mitigate risk, users are strongly advised to refrain from downloading applications from unverified sources and to avoid clicking on suspicious links. Caution is particularly vital in regions lacking official app distribution channels. Installing a reputable mobile antivirus solution with up-to-date signatures and real-time protection remains a critical pillar of mobile cybersecurity.


