The widely used StealC malware, actively deployed in cyberattacks for data theft and the delivery of secondary malicious payloads, has undergone a significant upgrade. The second iteration of this tool first surfaced on underground forums in March 2025, but only now have researchers at Zscaler released an in-depth analysis of its latest variant.
Since its initial release, the new version has received several minor updates, including bug fixes and the addition of new features. The most current iteration is version 2.2.4.
StealC is a lightweight and highly adaptable infostealer that emerged on darknet marketplaces in early 2023, where access to it was initially sold for \$200 per month. By 2024, it had been observed in large-scale malvertising campaigns and kiosk-mode attacks designed to lock down systems.
Development of StealC has remained steady. Late last year, its creators implemented a bypass for Chrome’s App-Bound Encryption—a security mechanism that had hindered access to stored data. This advancement allowed threat actors to retrieve deprecated cookies and hijack active Google account sessions, thereby significantly heightening the threat landscape.
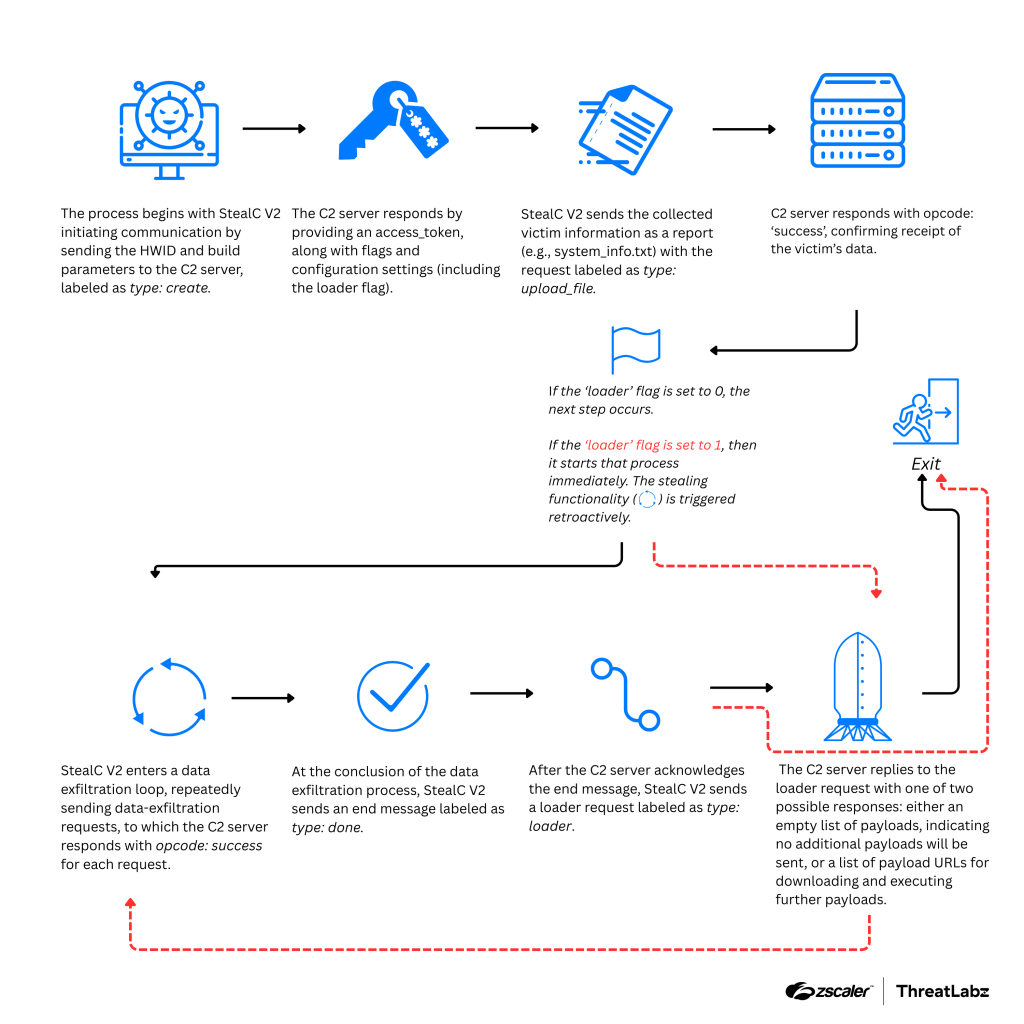
With the launch of version two, StealC’s capabilities have been considerably enhanced. Notably, the malware’s delivery mechanism now supports the execution of EXE files, MSI installers, and PowerShell scripts, each with customizable triggers. Communications with the command-and-control server are now encrypted using RC4, and randomized parameters have been introduced into responses to hinder detection.
The architecture has also been refined: the malware now supports 64-bit systems, resolves API functions at runtime, and includes a self-deletion mechanism. It also features a built-in template generator, enabling operators to compile custom builds with tailored data exfiltration rules. New capabilities include Telegram-based alert notifications and the ability to capture desktop screenshots—complete with multi-monitor support.
However, some legacy features were removed in the process. Code responsible for detecting virtual environments and loading DLL libraries has been stripped out—possibly to streamline the malware’s functionality or as a temporary omission during ongoing code refactoring.
In recent attacks documented by Zscaler, StealC was delivered via the Amadey loader, although this does not preclude the use of other delivery mechanisms or auxiliary tools in future campaigns.


