In late 2024, hacker groups operating on behalf of the governments of Iran and North Korea began actively employing a novel social engineering technique known as ClickFix. According to research by cybersecurity firm Proofpoint, at least three cyber-espionage groups—TA427 (Kimsuky), TA450 (MuddyWater), and UNK_RemoteRogue—had adopted this method within a span of three months.
Initially used predominantly by cybercriminals, ClickFix’s efficacy in bypassing security mechanisms quickly drew the attention of more sophisticated threat actors. The technique revolves around deceiving the victim into manually copying, pasting, and executing a malicious command in PowerShell or another command-line interface, often under the guise of resolving a technical issue or confirming a device registration.
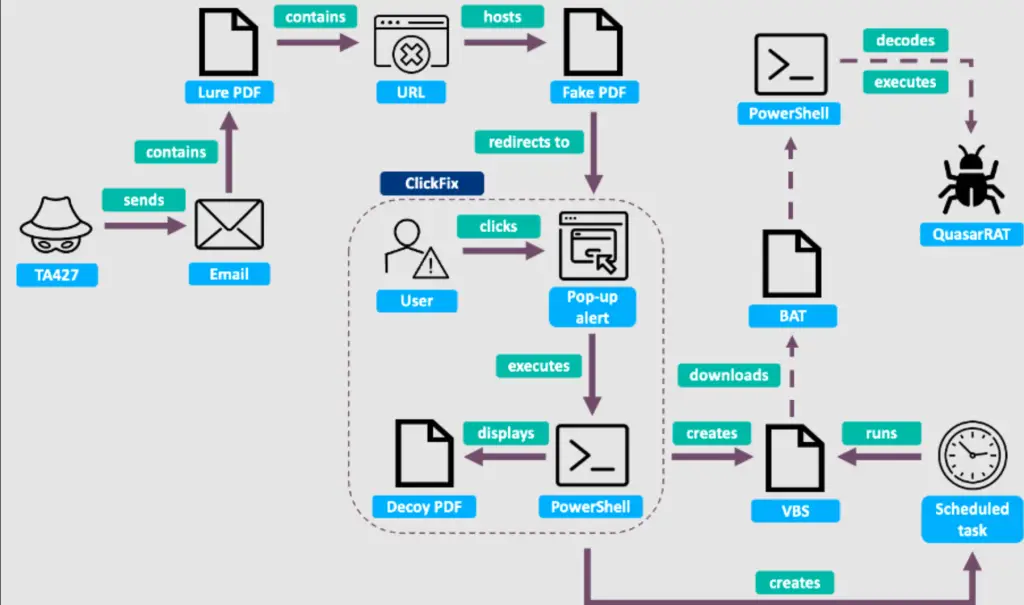
In January and February 2025, TA427 targeted analysts specializing in North Korean affairs. The attackers initiated contact with forged meeting invitations, allegedly from Japanese diplomats. Once rapport was established, the targets received a PDF file containing discussion topics and a link to what appeared to be the Japanese Embassy’s website. The site instructed users to register their device by running a PowerShell command. The command launched a script that both displayed a decoy PDF and stealthily installed Quasar RAT, an open-source remote access trojan used for surveillance.
Meanwhile, Iran-linked TA450 also adopted the ClickFix tactic. In November 2024, coinciding with Microsoft’s Patch Tuesday, the group disseminated spoofed emails impersonating Microsoft, warning of a fabricated vulnerability that required manual remediation. Victims were persuaded to launch PowerShell with administrative privileges and execute a provided command, which led to the installation of Level, a legitimate remote administration tool later repurposed for surveillance and data exfiltration. The campaign targeted governmental, financial, medical, and transportation institutions across the Middle East, as well as in Canada, Germany, Switzerland, and the United States.
By the end of 2024, the UNK_RemoteRogue group had also adopted the tactic. Using compromised Zimbra mail servers, they distributed emails containing links to Microsoft Office documents. Clicking the link directed victims to a webpage offering step-by-step instructions, and even a YouTube video tutorial, guiding users through launching PowerShell and pasting in the malicious command.
The embedded script was designed to execute PowerShell-based JavaScript, which established communication with Empire—a post-exploitation framework used for command and control of compromised systems. This campaign targeted two organizations associated with a major defense contractor and appeared to share infrastructure with other attacks aimed at the aerospace and defense sectors.
Experts note that while ClickFix does not fundamentally alter attack architectures, it streamlines the malware deployment phase. Instead of downloading executable payloads, victims voluntarily initiate the infection, believing they are performing legitimate verification or device registration steps. This significantly reduces the likelihood of detection by security solutions and allows attackers to operate with greater stealth.
Though not yet widely adopted, the method’s rapid uptake among state-sponsored groups signals its high efficiency. Analysts suggest that other APTs linked to Iran and North Korea have likely already begun experimenting with ClickFix—or will do so in the near future.


