
Federal cybersecurity agencies have issued a call to organizations and DNS providers to strengthen defenses against Fast Flux—an evasion technique increasingly employed by both state-sponsored hackers and ransomware operators.
Though long known, Fast Flux remains remarkably effective: it continues to serve as a resilient means of obscuring malicious infrastructure used for command-and-control operations, malware dissemination, and phishing campaigns. The core concept involves the rapid and frequent rotation of IP addresses associated with a domain, rendering traditional blocking methods virtually futile and making tracking efforts significantly more difficult.
Fast Flux is typically executed through botnets, where numerous infected devices across various countries function as proxy servers. These devices sequentially serve as the “face” of a domain, creating the illusion of hundreds—or even thousands—of legitimate sources, all while masking a single, centralized malicious backend.
There are two primary variants of the technique:
- Single Flux — where only the IP addresses returned in DNS responses are frequently rotated;
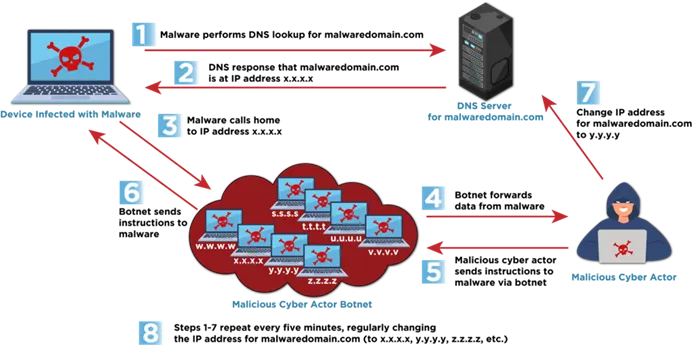
Single Flux diagram – CISA - Double Flux — which not only rotates IP addresses but also dynamically changes the DNS servers that handle the domain, adding an additional layer of obfuscation and greatly complicating mitigation efforts.
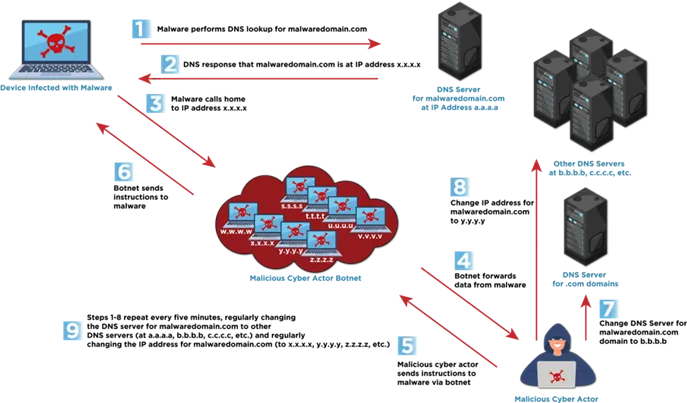
Double Flux diagram – CISA
Fast Flux has been observed in use by a range of threat actors, from phishing operators to nation-state-sponsored groups. Notable examples cited by CISA include the Gamaredon group, ransomware families like Hive and Nefilim, and providers of so-called bulletproof hosting—services that shield cybercriminals by offering anonymous and resilient infrastructure.
To counter Fast Flux operations, several measures are advised. Chief among them is the analysis of DNS logs for signs such as frequent IP rotations, unusually low TTL values, high IP entropy, and geographically implausible routing patterns—indicators that can expose malicious activity in its early stages.
Organizations are also encouraged to integrate external threat intelligence feeds and reputation databases into their security infrastructure—particularly SIEM systems and DNS resolvers—to automatically flag domains engaged in Fast Flux. Network traffic monitoring can further aid in identifying telltale signs, such as surges in DNS queries or bursts of connections within short timeframes.
Additionally, the development of custom behavioral detection algorithms tailored to an organization’s historical traffic and infrastructure is recommended. Such algorithms can increase the accuracy of anomaly detection while reducing false positives.
At the defensive perimeter, best practices include deploying IP and domain blocklists, configuring firewalls to limit access to suspicious destinations, and redirecting suspect traffic to internal analysis systems. Centralized logging, swift incident response to DNS anomalies, and participation in inter-organizational information-sharing networks are also considered essential components of a robust defense strategy.


