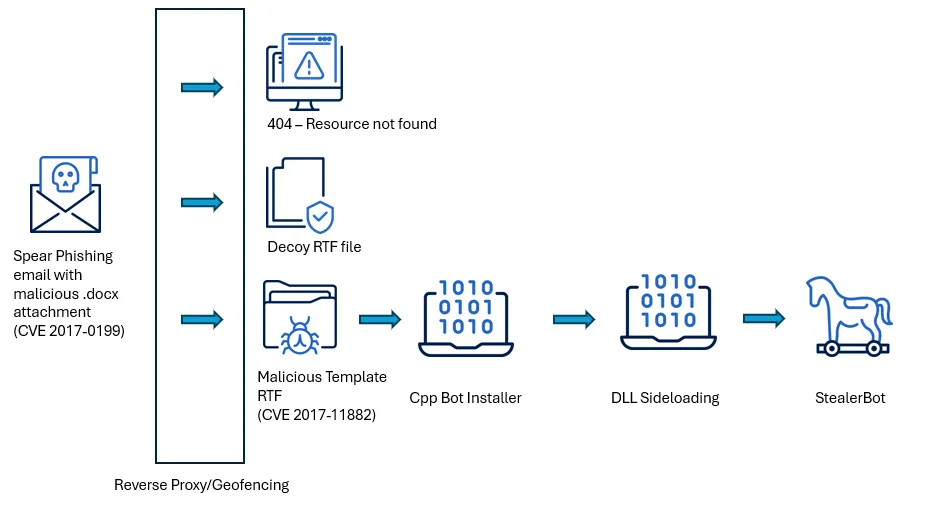
The SideWinder group has launched a new cyber-espionage campaign targeting government institutions across South Asia, striking agencies in Sri Lanka, Bangladesh, and Pakistan. According to a report by Acronis, the attacks began with phishing emails containing malicious documents, which only activated when opened by recipients in specific countries—displaying a blank file in all other cases.
The infection vector exploited long-known but still unpatched vulnerabilities in Microsoft Office—CVE-2017-0199 and CVE-2017-11882. Opening the document triggered the download of StealerBot, a .NET-based malware capable of capturing screenshots, keystrokes, passwords, and files, as well as granting remote shell access to the attacker. Its delivery relied on DLL hijacking, a technique that complicates detection.
Targets included ministries of defense and finance, central banks, and telecommunications regulators. The use of geo-filters and tightly constrained execution windows indicates a deliberate and highly targeted strategy. SideWinder continues to operate with remarkable consistency, avoiding prolonged dormancy—a testament to its resilient structure and sustained motivation.
Similar activity by this group has previously been documented by Kaspersky Lab, affirming the continuity of its methods and the reliability of its toolkit. Despite the age of the exploits, the attacks remain effective, capitalizing on unpatched systems and the inertia of organizations slow to adopt critical updates.


