Following the dismantling of LabHost—one of the largest phishing-as-a-service (PhaaS) platforms—in 2024, the underground phishing market entered a state of flux. Former LabHost clients scrambled to find alternative infrastructures to continue their malicious campaigns. It was within this vacuum that a new contender rapidly emerged: SheByte.
For years, LabHost had been a dominant provider of phishing kits specifically targeting Canadian banks, with a particular focus on the Interac brand. According to Fortra, up to 75% of all phishing traffic impersonating Interac had been routed through LabHost. After its shutdown, the volume of such attacks nearly halved, though they did not vanish entirely. Cybercriminals began migrating en masse to other services. Among these, SheByte stood out for its aggressive and open marketing strategy.
First identified in May 2024 through a Telegram channel adorned with a cartoonish logo reminiscent of Bettie Page, SheByte officially launched in mid-June. Within weeks, it was already responsible for roughly 10% of all Interac-themed phishing attacks. Even during its testing phase, it accounted for 8% of attacks, with that share rising swiftly.
Mirroring LabHost’s functionality, SheByte offered a suite of universal phishing templates that spoofed the websites of major Canadian banks. At launch, its arsenal included templates for 17 Canadian and 4 U.S. banks, along with popular email providers, telecom companies, cryptocurrency exchanges, and even toll services. Notably, the platform supported dynamic customization, allowing threat actors to tailor each template to the specific needs of a given campaign.
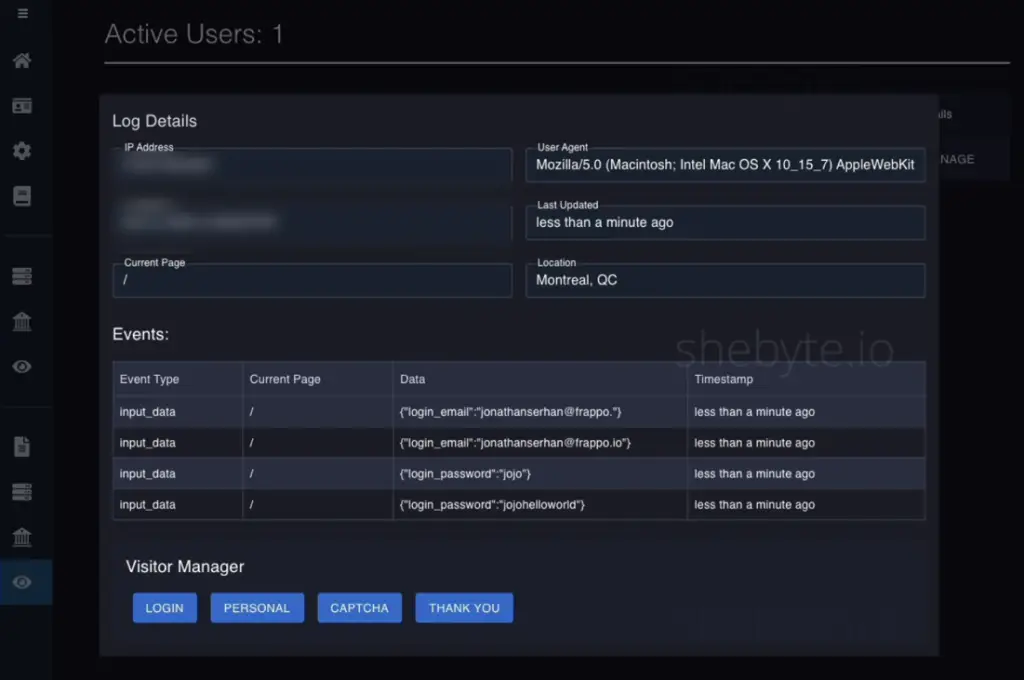
SheByte operates under a flat-rate subscription model of $199 per month, with discounts for long-term commitments. This fee grants full access to its phishing templates, anti-detection tools, and LiveRAT—a command-and-control panel for real-time attack orchestration. Functionally, LiveRAT replicates features from LabHost’s LabRAT, enabling adversaries to monitor victims in real time, intercept two-factor authentication codes, trigger secondary prompts, and send arbitrary messages within a spoofed “bank” interface.
The platform places particular emphasis on evasion and anti-analysis techniques. Clients can geo-fence access, block VPN and proxy traffic, and deny requests from virtual machines. To further thwart automated analysis, phishing campaigns begin with a CAPTCHA challenge. All of these features are integrated natively within SheByte’s management console.
Interestingly, SheByte’s developer claims the platform is a one-person operation, positioning this as a strength rather than a limitation. The rationale is that LabHost’s downfall was partly due to the number of developers involved, which increased the risk of internal leaks and law enforcement infiltration. Additionally, SheByte asserts that it retains no logs and uses end-to-end encryption for stolen data, though the veracity of these claims remains uncertain.
Technically, the new Interac-themed phishing kit—launched in February 2025—has been designed to be harder to detect. Filenames are randomized, directories are dynamically generated, and the page structure is frequently updated. Indicators of SheByte activity include legacy start.php paths in version 1 and 7–9 character alphanumeric patterns in URLs of newer versions.
After a brief lull in the fall of 2024—partly due to a cyberattack from rival platform Frappo—SheByte has resurged. A marked uptick in phishing activity began in December 2024, coinciding with the launch of its so-called “v2” pages. Although the Interac branding wasn’t fully integrated until early 2025, interest in the platform spiked, suggesting that the phishing ecosystem has adapted to LabHost’s demise and embraced a new frontrunner.
While SheByte has yet to match LabHost’s scale, it is widely regarded as its most promising successor. Thanks to its open distribution model, extensive brand support, and ongoing technical innovation, SheByte has quickly filled the void. If left unchecked by law enforcement, it may well become the next major threat to financial institutions across Canada and the United States.


