The cybersecurity firm SentinelOne has released a report detailing recent attempts by malicious actors to breach its systems. A successful compromise of such an organization could have paved the way for hackers to access thousands of protected infrastructures across the globe.
“We don’t just study attacks, we experience them firsthand, levied against us. Our teams face the same threats we help others prepare for, and that proximity to the front lines shapes how we think, and how we operate,” the document states.
While discussions of targeted attacks remain a taboo among cybersecurity solution providers, the constant pressure on defense mechanisms serves to refine and advance protective technologies.
In recent months, the company’s specialists have repelled a wide array of attacks — ranging from financially motivated criminal operations to sophisticated campaigns orchestrated by state-sponsored intelligence services.
The most extensive and intricate campaign was orchestrated by North Korean operatives. Researchers uncovered an elaborate network of IT professionals from the DPRK operating under false identities. The attackers created nearly 360 meticulously crafted virtual personas, each complete with compelling professional histories, portfolios, and references. Over a thousand applications were submitted for technical roles at the company on behalf of these fictitious candidates. In one particularly audacious instance, an agent even sought employment within SentinelOne’s cyber intelligence division — the very team investigating and analyzing their activities at the time.
Another serious threat stems from hackers operating on behalf of the Chinese government. The ShadowPad group compromised the supply chain by infiltrating a logistics partner responsible for managing hardware infrastructure. Between July 2024 and March 2025, cybercriminals deployed a stealthy malware strain dubbed ScatterBrain to penetrate the systems of more than 70 organizations worldwide. Victims included industrial enterprises, government agencies, financial institutions, telecommunications providers, and research centers.
A third persistent menace is ransomware. The Nitrogen gang employs a cunning tactic: they identify reseller companies with lax customer verification procedures and, through social engineering, acquire legitimate software licenses. Their ultimate goal is to infiltrate cybersecurity platforms — including SentinelOne’s own EDR system. Once inside, they methodically examine the defense mechanisms, seek out vulnerabilities, and develop techniques to evade intrusion detection systems.
Meanwhile, the Black Basta hacking group has also intensified its operations, opting for a different strategy. Its members systematically test the effectiveness of their malware against leading security solutions. Their focus includes systems from prominent vendors such as CrowdStrike, Carbon Black, Palo Alto Networks, and SentinelOne. Each trial is carefully documented to refine their methods of intrusion.
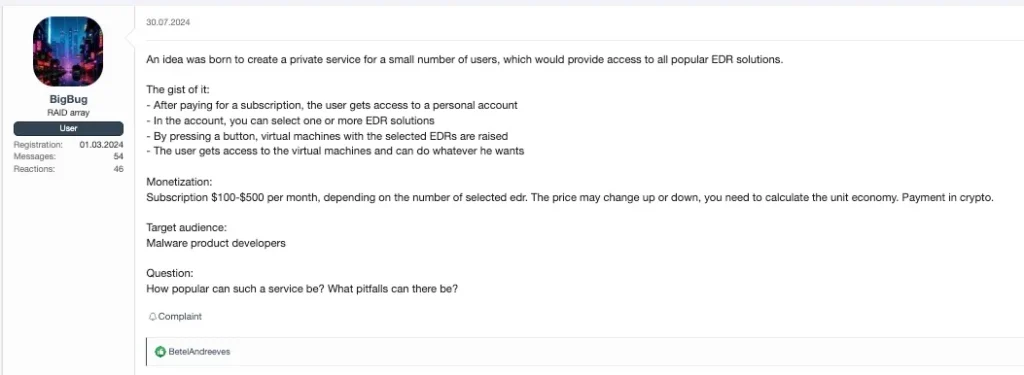
Hacker forums now regularly feature offers for temporary or permanent access to security system management consoles.
This wave of recent attacks has prompted the SentinelOne team to reassess its defensive posture. Engineers have implemented additional layers of security and developed more advanced monitoring tools for the entire infrastructure. There is now an intensified focus not only on fortifying internal systems but also on rigorously vetting all partner organizations with access to critical data.


