The fraudulent Scallywag scheme, built upon specially crafted WordPress plugins, had long been generating billions of ad requests daily for its operators. However, a large-scale deception campaign targeting advertising platforms was finally dismantled—through technical analysis and domain blocking, its activity was curtailed by 95%.
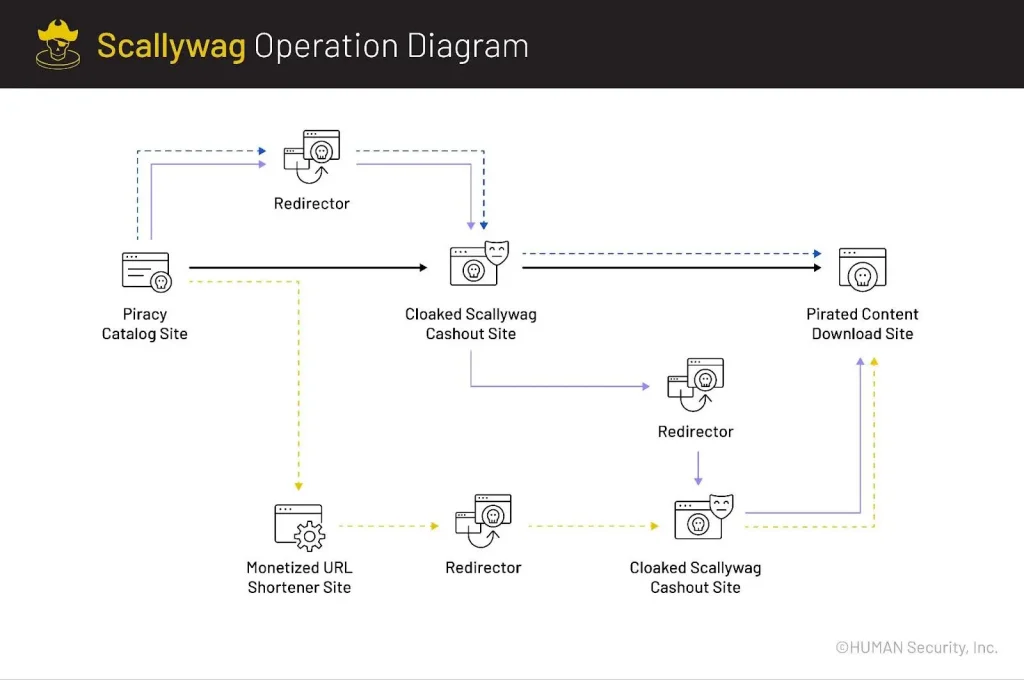
According to HUMAN, a company specializing in bot detection and ad fraud prevention, Scallywag comprised an intricate network of 407 domains. The core of the operation lay in transforming dubious websites—primarily pirate content hubs and URL shorteners—into lucrative sources of fake ad impressions. This was achieved via plugins embedded into WordPress sites, which handled everything from redirects to cloaking.
Scallywag’s ecosystem relied on four main plugins—Soralink (2016), Yu Idea (2017), WPSafeLink (2020), and Droplink (2022). The latest was distributed for free, provided users completed tasks that funneled revenue to its developers. The others were actively marketed and even featured in instructional YouTube videos. HUMAN emphasized that the Scallywag campaign was not the handiwork of a single group; rather, it represented a “fraud-as-a-service” model, accessible to a wide range of participants, including novice threat actors.
Pirates and shady site owners, unable to monetize their platforms through legitimate channels due to a lack of trust from ad networks, entered into tacit cooperation with the scheme’s architects. Visitors to such sites were rerouted via shortened URLs to intermediary pages cluttered with aggressive ads, CAPTCHA challenges, and countdown timers. These interstitials generated fake views and clicks, enriching the fraudsters before users accessed the promised content.
A defining feature of Scallywag was its cloaking mechanism. When inspected by ad networks or automated analytics tools, the site appeared as a harmless blog—devoid of anything suspicious. This layer of deception allowed the operation to run undetected for an extended period.
The anomaly was uncovered through behavioral traffic analysis. HUMAN noted sudden surges in ad impressions across otherwise nondescript WordPress blogs, the presence of waiting mechanisms, unexpected CAPTCHA prompts, and dynamic content replacement based on the source of traffic.
Following the identification of the scheme, HUMAN’s specialists began systematically blocking domains, liaising with ad platforms, and halting traffic acquisition—effectively collapsing the scheme’s economic foundation.
Attempts by the perpetrators to circumvent blocks through new domains and convoluted redirect chains were swiftly neutralized. As a result, the volume of fake ad requests plummeted from 1.4 billion per day to nearly zero, prompting most participants to abandon the operation.
Though Scallywag in its current form has been largely dismantled, HUMAN cautions that its orchestrators may reconfigure their infrastructure and re-emerge in a new guise. The digital fraud ecosystem remains highly adaptive and resilient—especially in corners of the internet where legality and reputation take a backseat.


