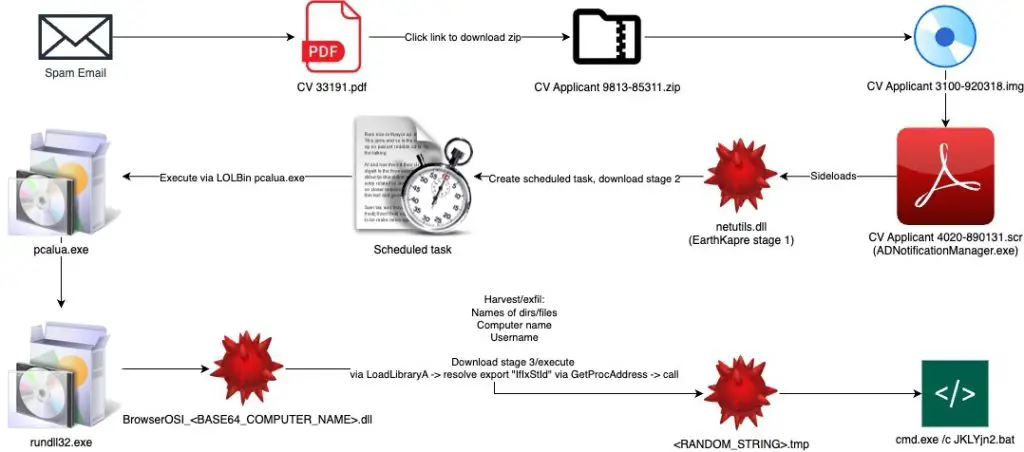
EarthKapre/RedCurl Attack Chain
The hacker collective known as RedCurl—previously distinguished by its corporate espionage operations—has now been observed for the first time deploying ransomware in a targeted attack. This strategic pivot significantly amplifies the threat the group poses. The shift came to light during an investigation by Romanian cybersecurity firm Bitdefender, which uncovered the use of a previously unknown malware strain dubbed QWCrypt.
RedCurl, also referred to as Earth Kapre and Red Wolf, had historically focused on extracting sensitive corporate data from organizations in Canada, Germany, the United Kingdom, the United States, Slovenia, Ukraine, and beyond. Active since 2018, the group was known for its phishing campaigns crafted around HR-themed lures, which enabled the execution of malicious code on compromised systems.
In January 2025, Huntress reported renewed RedCurl activity in Canada, highlighting the deployment of RedLoader—a downloader with remote access capabilities. By February, eSentire observed the use of fraudulent résumé-themed PDF attachments in phishing emails. These triggered malicious payloads via a legitimate Adobe process, “ADNotificationManager.exe.”
According to Bitdefender, the latest campaign involved ISO disk images disguised as résumé files. Embedded within was a faux Windows screensaver which, in truth, was the same “ADNotificationManager.exe” binary designed to execute a malicious DLL, “netutils.dll,” via a DLL sideloading technique.
Once launched, the malware redirected the victim’s browser to Indeed’s legitimate login page, crafting the illusion of a benign document opening while the system was being quietly compromised in the background.
The downloader performed several functions: it fetched a secondary malicious DLL, scheduled a task to ensure persistence, and triggered a component through “pcalua.exe”—a method previously detailed by researchers at Trend Micro. At this stage, the attackers could freely navigate the network, harvest data, and escalate their foothold.
Notably, RedCurl took its activities a step further by deploying ransomware—an unprecedented move for the group. Bitdefender found that the malware encrypted virtual machines on host servers, effectively halting all services running on them. This tactic inflicted maximum damage with minimal effort, paralyzing the targeted infrastructure.
Before initiating encryption, the ransomware employed a BYOVD (Bring Your Own Vulnerable Driver) strategy to disable endpoint security mechanisms. It also collected detailed technical information about the infected systems. Interestingly, the ransom note contained phrasing reminiscent of known ransomware gangs such as LockBit, HardBit, and Mimic. However, the absence of a dedicated data leak site casts doubt on whether the objective was truly extortion or mere obfuscation.
RedCurl’s transition from espionage to ransomware deployment suggests a strategic intent to diversify its arsenal of coercion. This evolution renders the group’s operations more erratic and unpredictable, prompting a reassessment of defensive strategies against such hybrid threats.


