Threat actors continue to exploit popular open-source repositories as launchpads for the distribution of malicious code. This time, researchers at Socket uncovered several suspicious packages on the Python Package Index (PyPI), masquerading as legitimate utilities while covertly harvesting user data from Instagram*, TikTok, and Telegram.
Three malicious libraries—“checker-SaGaF,” “steinlurks,” and “sinnercore”—were uploaded to PyPI over the past few months and collectively downloaded more than 6,000 times. Though they have since been removed, the consequences of their use could prove serious.
“Checker-SaGaF” was designed to verify whether a given email address was linked to TikTok or Instagram accounts by sending HTTP POST requests to the password recovery endpoints of those platforms. This enabled attackers to efficiently validate stolen email lists for use in further attacks—ranging from phishing and spam to account takeover attempts via credential stuffing or password spraying.
The “steinlurks” package employed a similar method, but exclusively for Instagram. It mimicked the behavior of an Android application, issuing spoofed requests to several Instagram API endpoints—including lookup, send_recovery_flow_email, and check_email—in an attempt to bypass the platform’s safeguards and validate accounts without detection.
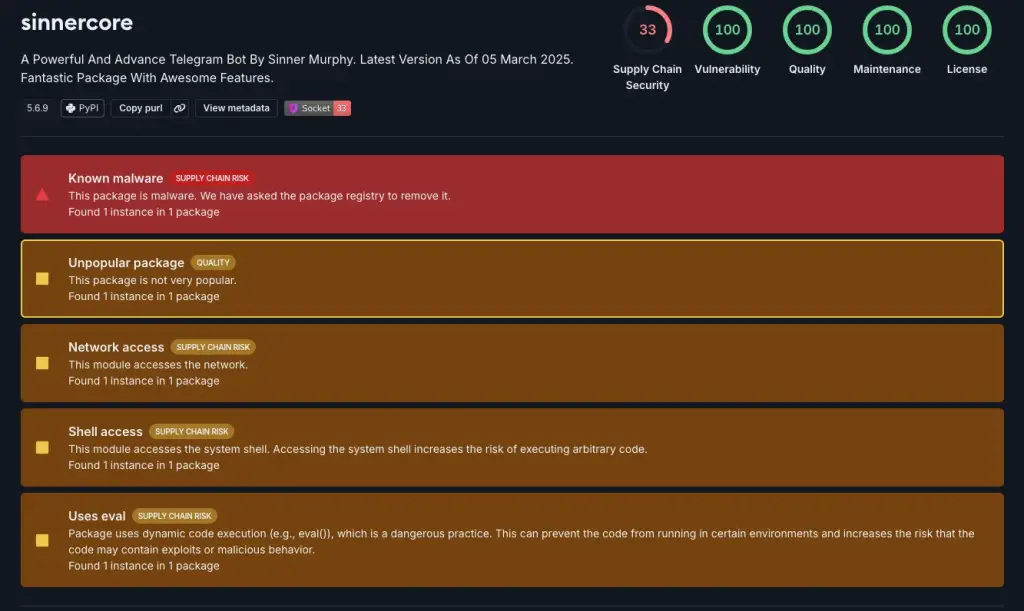
“Sinnercore” took the malicious capabilities a step further. It initiated fake password recovery requests using only a username and communicated with the Instagram API, while also collecting Telegram profile data such as name, ID, status, and bio. The package additionally contained cryptocurrency utilities for retrieving Binance exchange rates and performing currency conversions, alongside tools for extracting metadata from other PyPI packages—likely to lend the appearance of legitimacy by mimicking authentic developer behavior.
All of these functionalities contributed to the aggregation of verified email addresses and account credentials, which could later be weaponized in targeted attacks or sold on the dark web. As Socket’s researchers emphasize, such seemingly benign utilities often represent components of a broader attack chain and are engineered to evade detection with alarming efficiency.
In early May, another malicious PyPI package—“dbgpkg”—was identified. Disguised as a debugging tool, it secretly implanted a backdoor within the developer’s system, allowing remote code execution and data exfiltration. It was downloaded approximately 350 times. Further analysis revealed that it shared a common payload with previously flagged packages “discordpydebug” and “requestsdev,” the latter of which had been downloaded 76 times. According to ReversingLabs, all three are likely part of a coordinated campaign.
Notably, the embedded backdoor leverages GSocket—a network toolkit previously linked to the Phoenix Hyena threat group (also known as DumpForums or Silent Crow), which in 2022 targeted Russian entities, including the cybersecurity firm Doctor Web. While definitive attribution remains elusive, the recurring payloads and use of advanced obfuscation and injection techniques suggest a high level of technical sophistication.
These findings reaffirm a troubling trend: malicious packages increasingly masquerade as developer tools, operating quietly and surgically. The threat is exacerbated by the difficulty of detecting such libraries with the naked eye. Software supply chains remain a vulnerable link—one that cybercriminals continue to exploit with growing precision.


