Malicious Python libraries have once again surfaced on the PyPI platform, engineered to steal confidential data and automate the verification of stolen credit cards. Before their removal, these packages had accumulated over 39,000 downloads in total.
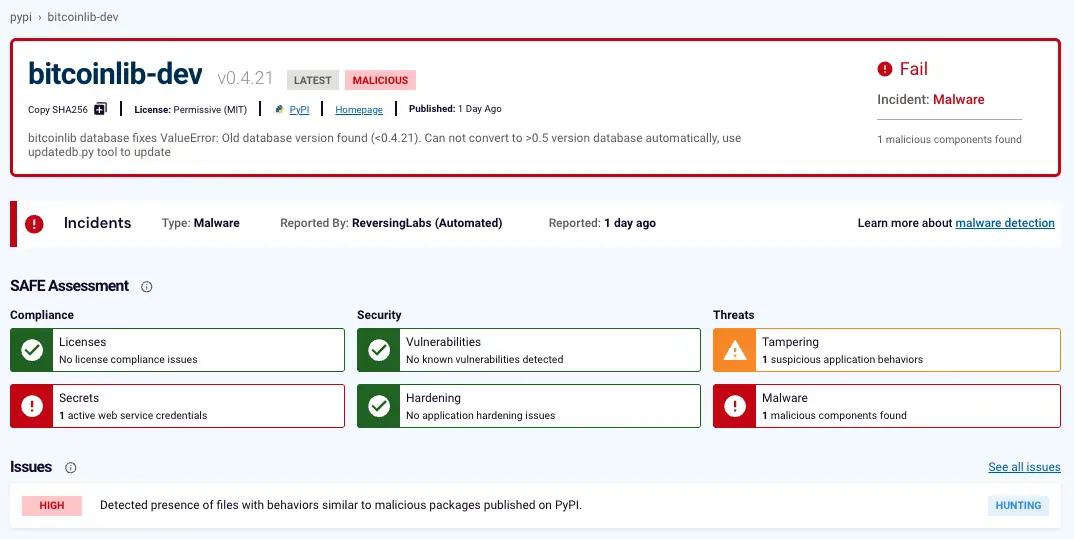
According to ReversingLabs, two of the identified malicious libraries—bitcoinlibdbfix and bitcoinlib-dev—were cleverly disguised as legitimate patches for the widely used bitcoinlib module. A third, known as disgrasya, was flagged by researchers at Socket as a fully operational carding tool, specifically targeting e-commerce platforms powered by WooCommerce.
Statistics from pepy.tech reveal the alarming reach of these threats: disgrasya alone was downloaded more than 37,000 times, while bitcoinlibdbfix and bitcoinlib-dev recorded over 1,000 and 700 downloads, respectively. Though appearing deceptively similar to authentic software, these packages hijacked the “clw cli” command, replacing it with malicious code designed to exfiltrate sensitive database files.
In an effort to further deceive users, the authors of the counterfeit libraries even engaged in discussions on GitHub, recommending the fake updates as genuine enhancements. However, the ruse was quickly uncovered, and the malicious packages were promptly removed from the repository.
The most concerning of the trio, disgrasya, made no attempt to obscure its nefarious functionality. Version 7.36.9 introduced a malicious script that persisted through subsequent updates. This script was engineered to validate stolen credit card details by mimicking the behavior of an ordinary online shopper.
Through this method, attackers could bypass traditional fraud-detection mechanisms. The script would programmatically locate a product, add it to the cart, proceed to checkout, and populate the payment form with randomized data alongside the stolen card information. All harvested data—including card number, expiration date, and CVV—was exfiltrated to an external server controlled by the attackers.
The domain railgunmisaka[.]com served as the collection point for the pilfered information. Thus, disgrasya functioned as a critical component in broader carding automation schemes, facilitating large-scale testing of stolen credentials. These credit card details are often sourced from underground forums, typically obtained via phishing, skimming, or malware-based attacks.
Once validated, the active cards are used to purchase gift cards or prepaid cards, which are then resold for profit. To evade detection, fraudsters typically begin with low-value transactions, reducing the risk of alerting cardholders or triggering anti-fraud mechanisms.
The name disgrasya, as noted by the Socket team, is unlikely to be coincidental. In Filipino slang, it translates to “misfortune” or “accident,” aptly reflecting the package’s destructive nature—a malicious payload embedded within what appears to be a benign software library, exploiting the ordinary flow of online shopping to execute a full-scale attack.


