Pwn2Own 2025 has concluded in Berlin, marking one of the most significant showcases of zero-day vulnerabilities in enterprise technologies. Over the course of three days, participants earned a total of $1,078,750 by demonstrating 29 vulnerabilities, with several overlapping exploits reported among competing teams.
As per tradition, all targets in the competition ran fully updated systems with the latest operating systems and security patches. This year’s categories included AI systems, web browsers, virtualization platforms, local privilege escalation techniques, servers, cloud and container technologies, and automotive software. Notably, Tesla provided demonstration booths featuring the 2025 Model Y and the 2024 Model 3—though no attempts were made to exploit these vehicles during the event.
On the first day alone, participants earned $260,000 for successful demonstrations. The second day saw the prize total rise to $435,000 following the discovery of 20 new vulnerabilities. The final day added another $383,750 for eight more exploits, some of which involved sophisticated attack chains. Under contest rules, vendors are granted a 90-day window to patch identified vulnerabilities before full technical details are publicly disclosed.
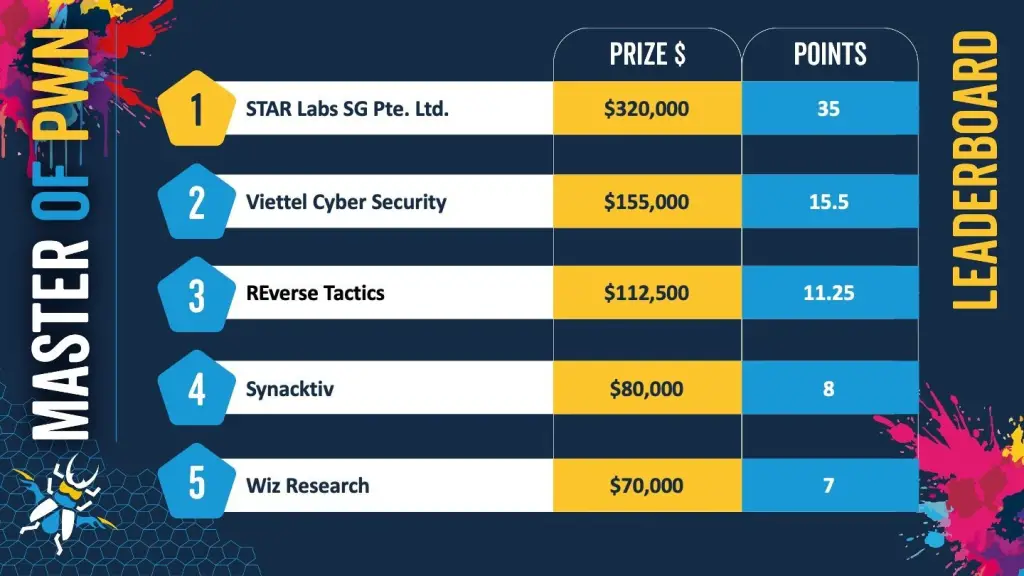
The competition’s top honors went to STAR Labs SG, who scored 35 points and earned $320,000. Over three days, the team demonstrated successful exploits against Red Hat Enterprise Linux, Docker Desktop, Windows 11, VMware ESXi, and Oracle VirtualBox. The single largest reward—$150,000—was awarded to Nguyen Hoang Thach for an integer overflow exploit targeting VMware ESXi.
Second place was claimed by Viettel Cyber Security, whose team executed a virtual machine escape from Oracle VirtualBox to the host system and leveraged a combined attack involving an authentication bypass and insecure deserialization to compromise Microsoft SharePoint.
Reverse Tactics secured third place by demonstrating an exploit chain in VMware ESXi that involved an integer overflow and use of an uninitialized variable—earning the team $112,500 on the final day of the competition.
In the aftermath, Mozilla promptly released emergency patches for Firefox and Firefox ESR, addressing the two zero-day vulnerabilities demonstrated during the event (CVE-2025-4918 and CVE-2025-4919). These fixes were rolled out in Firefox 138.0.4, ESR 128.10.1, ESR 115.23.1, and the latest Android version of the browser.


