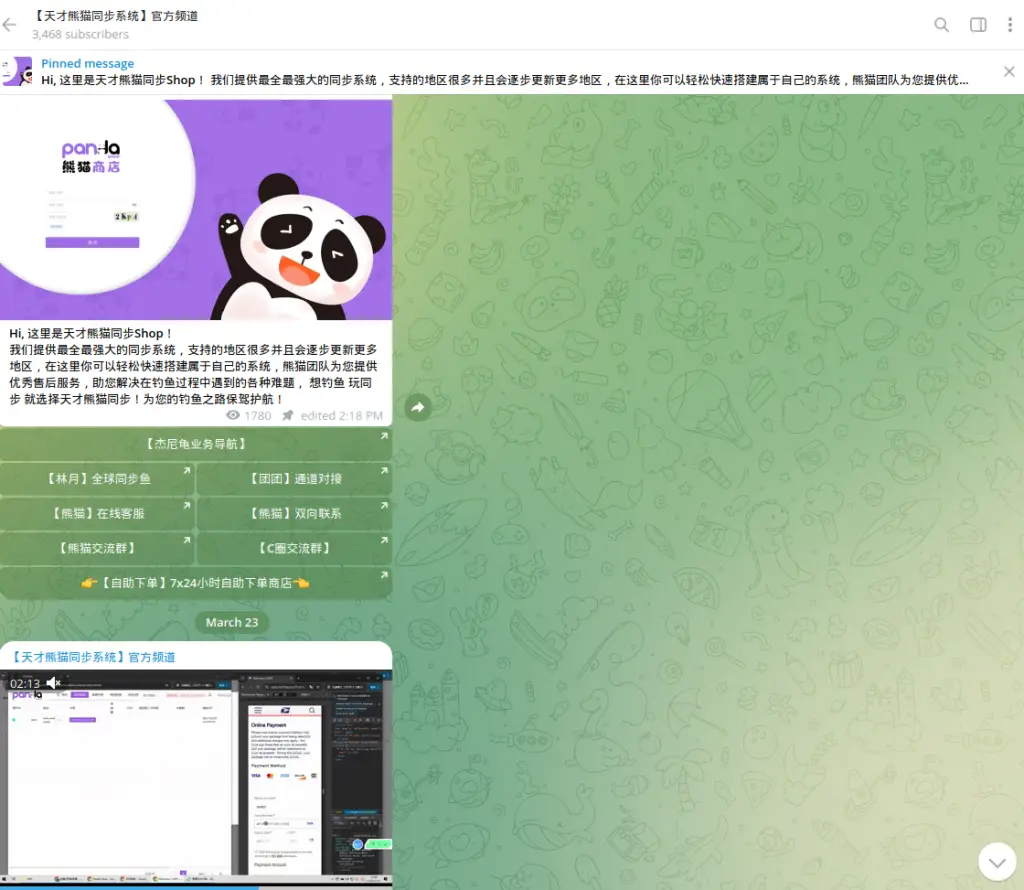
A major Chinese cybercriminal syndicate has launched a sweeping SMS phishing campaign targeting millions of users worldwide. The newly unveiled tool, dubbed Panda Shop, facilitates the distribution of up to 2 million malicious messages per day via SMS, iMessage, and RCS, effectively transforming phishing into a convenient subscription-based service for fellow criminals.
Researchers at Resecurity discovered that Panda Shop is already being actively promoted on Telegram, complete with bots, support channels, and customizable attack options. According to the report, the developers boldly claim they have no fear of the FBI, asserting that their location in China places them beyond the reach of Western law enforcement.
The tool’s defining feature is its full automation of the phishing process. Hundreds of templates mimic the interfaces of delivery services, government portals, banks, and internet providers. The attacks frequently target users of Apple Pay, Google Wallet, and traditional payment cards, harvesting credentials for resale on underground marketplaces.
To amplify the campaign’s reach, the attackers acquire compromised Apple ID and Gmail accounts and employ IP-filtering services to exclude unviable targets and evade security measures. Some phishing pages are virtually indistinguishable from legitimate websites—such as those of postal services or financial institutions—and are meticulously optimized for mobile browsers.
Beyond digital channels, the group utilizes SMS gateways and carrier-grade hardware to directly deliver millions of messages to SIM cards, including those belonging to users outside the United States. The report notes that the financial toll from these operations likely amounts to tens, if not hundreds, of millions of dollars annually.
Evidence suggests ties to former members of the Smishing Triad, a group previously exposed in public investigations. Panda Shop appears to be a reboot—featuring an updated interface, enhanced capabilities, and a refined image within the criminal ecosystem.
According to Resecurity, the campaign is orchestrated from the Shanghai time zone, and one of the domains used is registered through a Chinese company previously implicated in ICANN policy violations. Despite the scale of the operation, arrests have been limited to low-level operatives tasked with withdrawing cash from ATMs, while the true masterminds remain at large.


