A critical vulnerability in the Wazuh server, patched as early as February, is now being actively exploited...
In the spring of 2024, an obscure tool known as Skitnet—also appearing under the alias “Bossnet”—surfaced on...
In 2024, Apple introduced audio passthrough functionality to its Mac lineup, enabling the transmission of uncompressed, original...
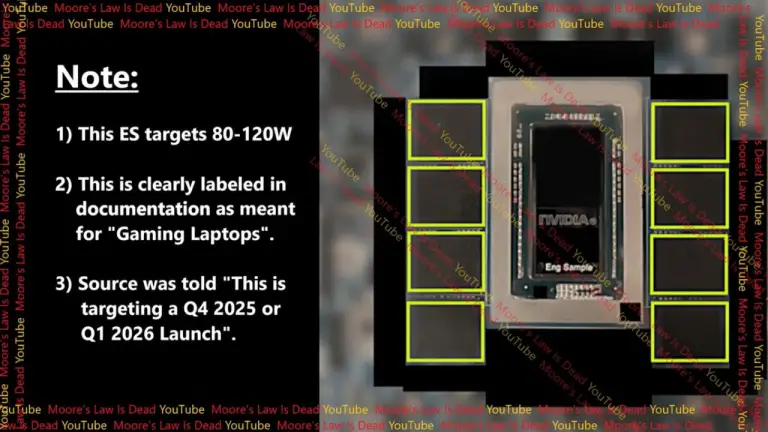
NVIDIA is currently collaborating with MediaTek to develop an ARM-based processor tailored for desktop-class platforms, specifically targeting...
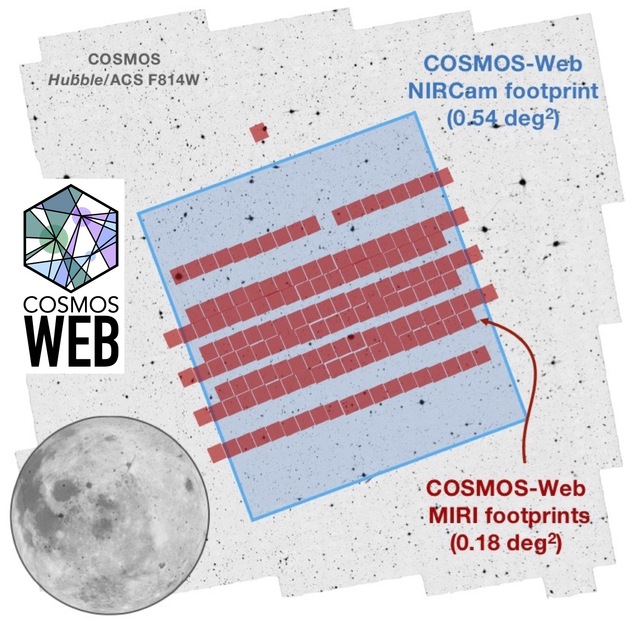
The COSMOS project, supported by the National Aeronautics and Space Administration (NASA), has released 1.5TB of survey...
Android 16 is Here: Early Release Brings Real-Time Notifications, Desktop Mode, & Enhanced Security!


Android 16 is Here: Early Release Brings Real-Time Notifications, Desktop Mode, & Enhanced Security!
Following an extended period of development and testing, Google has now officially released Android 16, initially rolling...
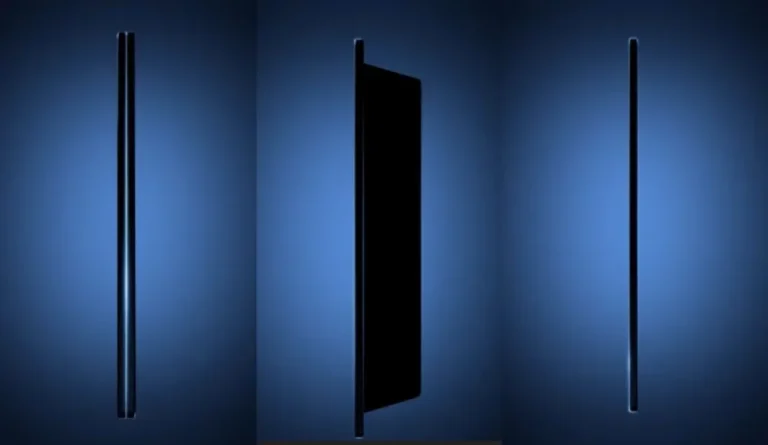
Following the early June release of its initial teaser for a new generation of foldable smartphones—promising a...
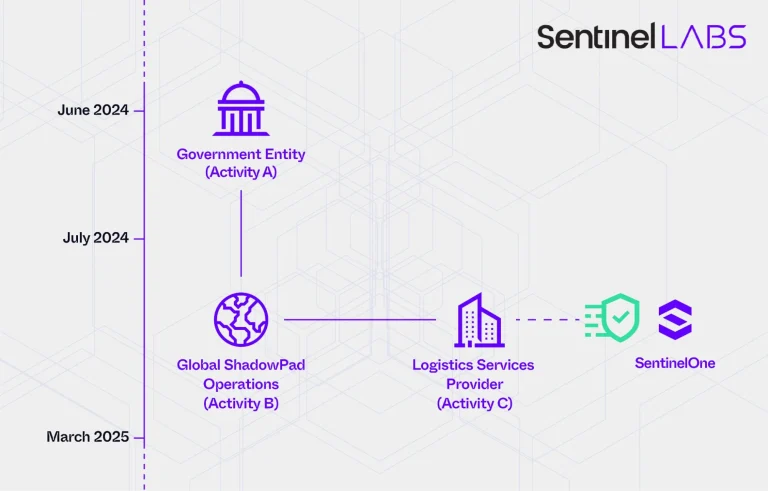
A far-reaching espionage campaign targeting the American cybersecurity firm SentinelOne has been revealed as merely one chapter...
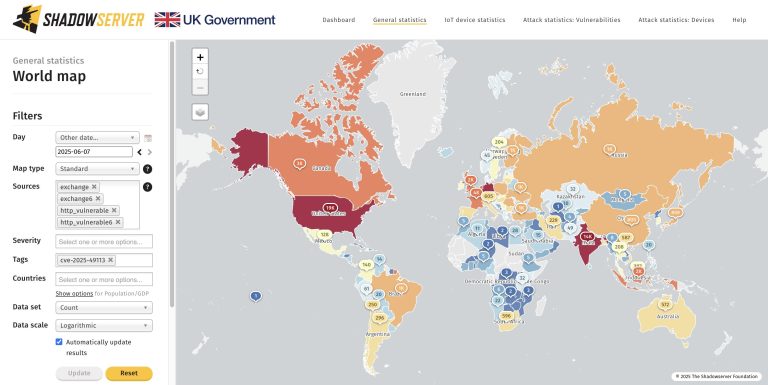
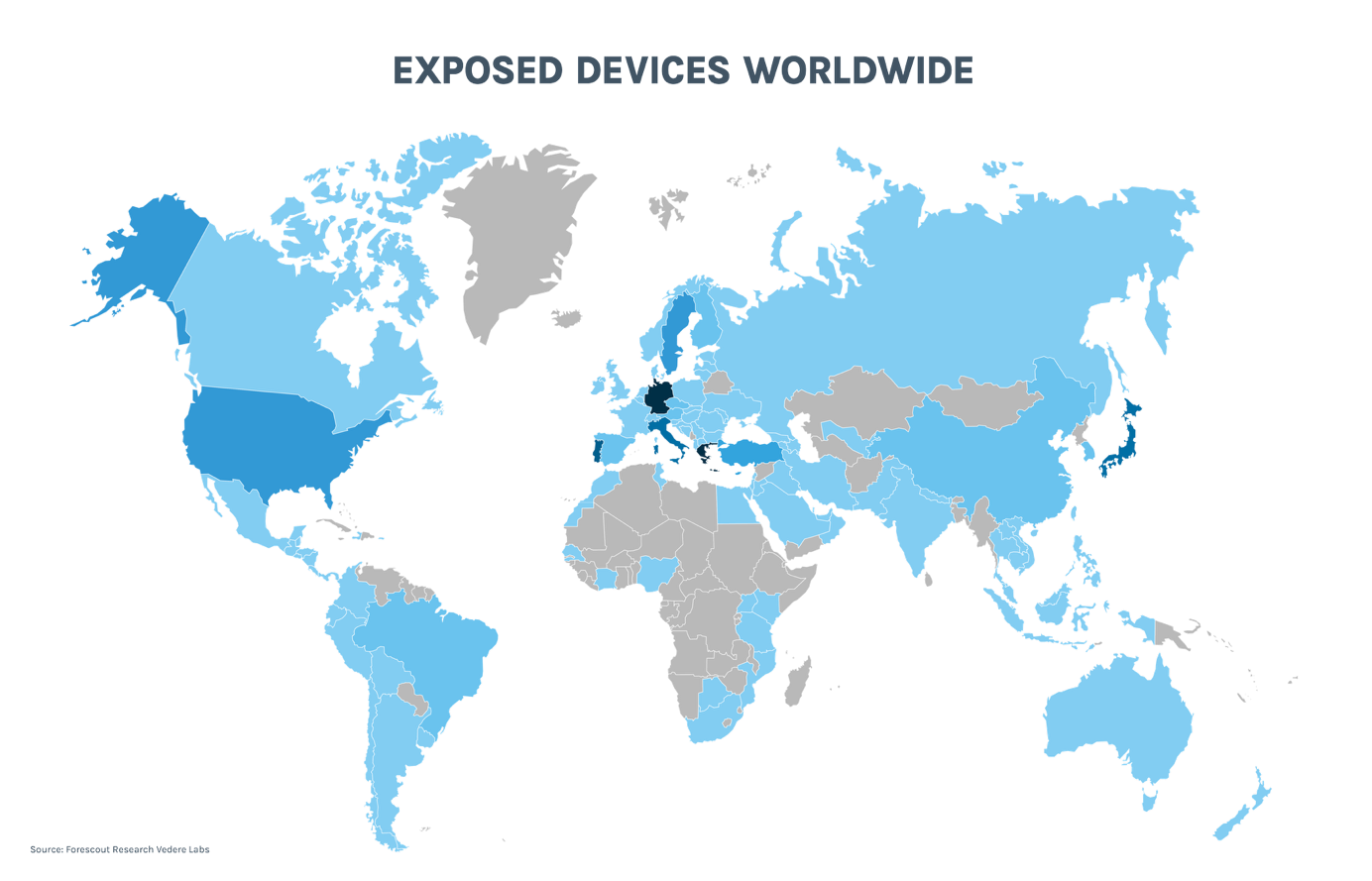
The critical vulnerability CVE-2025-49113 in Roundcube—one of the world’s most widely adopted open-source webmail platforms—has been found...
A vulnerability in an outdated version of Google’s username recovery form allowed malicious actors to deduce a...
Following the April 2025 Windows security updates, users began to notice a curious anomaly — an empty...
Two malicious packages were recently discovered within the widely used JavaScript package registry, npm. Beneath their seemingly...
An increasing number of cybercriminals are shifting toward the use of so-called residential proxy networks, transforming ordinary...
As solar panels steadily become a fixture of daily life—enhancing energy resilience and reducing our carbon footprint—their...