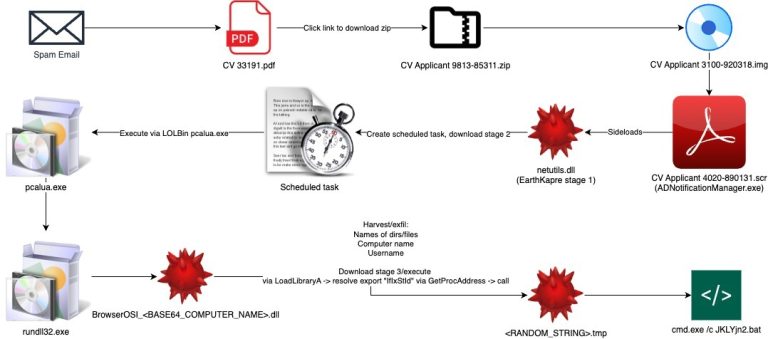
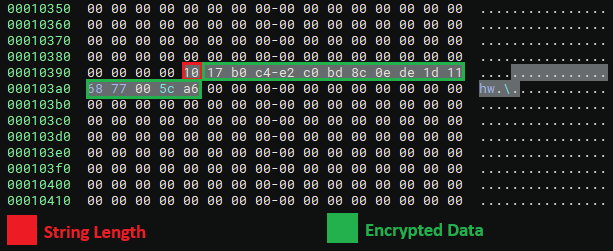
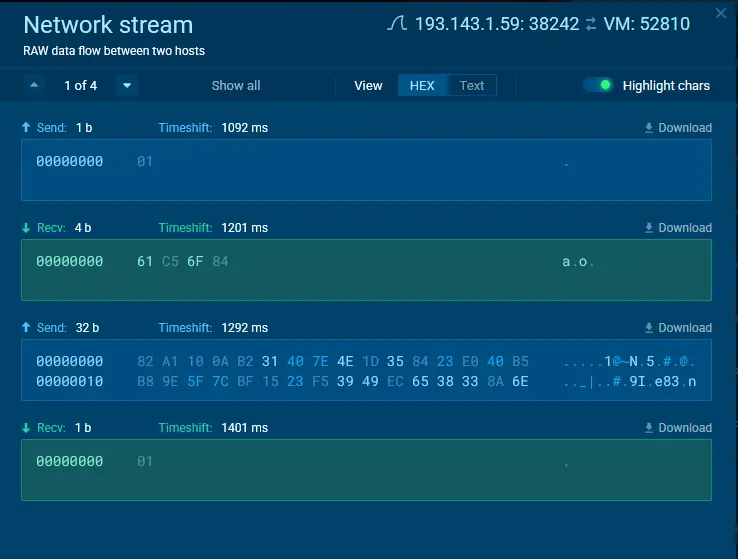
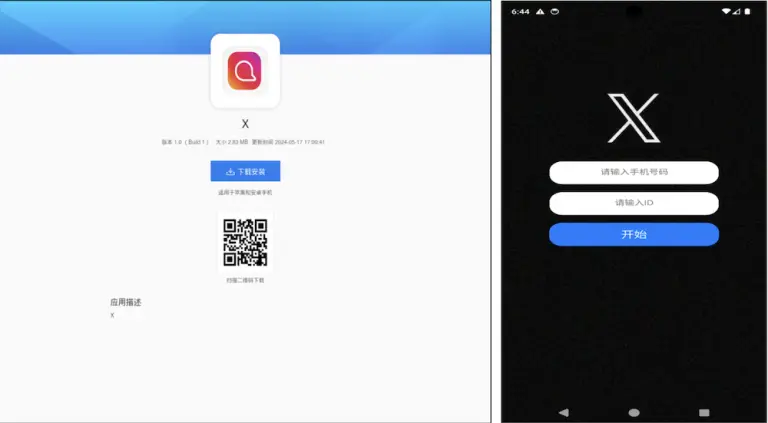
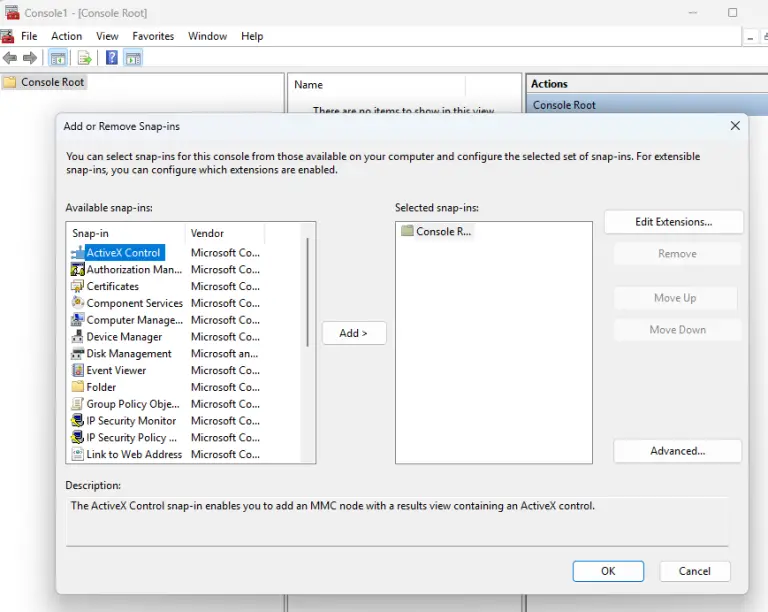
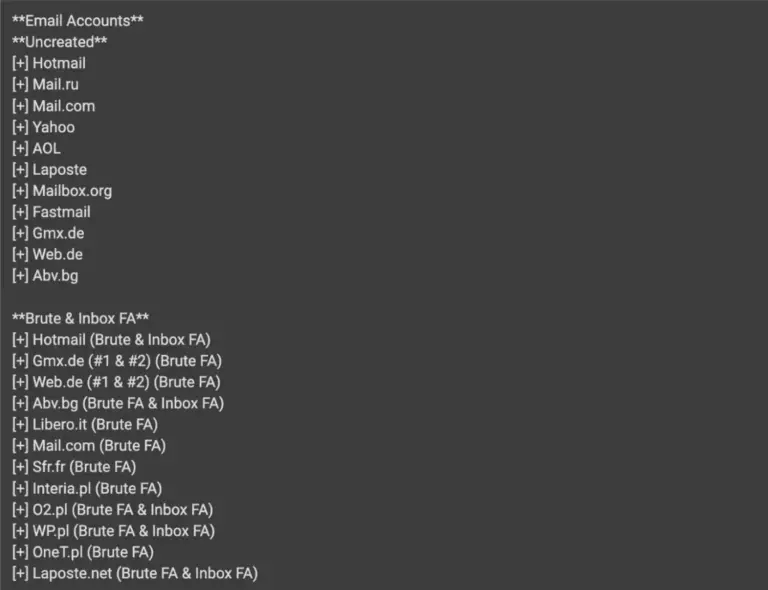
The hacker collective known as RedCurl—previously distinguished by its corporate espionage operations—has now been observed for the...
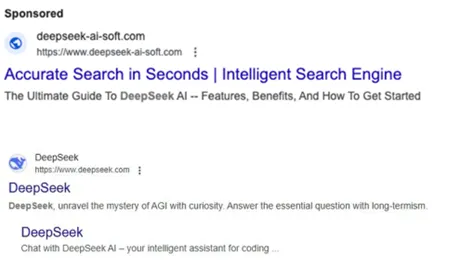
The soaring popularity of DeepSeek, amplified by ongoing debates around privacy, has not only drawn the attention...
OpenAI is strengthening the security of its products and infrastructure by expanding its Bug Bounty program and...
Amid the escalating wave of cyber threats, researchers have identified a novel strain of malware designed to...
In September, cybersecurity experts at NSFOCUS identified the emergence of a new botnet dubbed GorillaBot. Built upon...
Cybercriminals have devised a novel technique to conceal malicious code within Android applications, rendering it nearly impervious...
Trend Micro has uncovered a new campaign orchestrated by the threat group Water Gamayun, in which adversaries...
Linux kernel version 6.15 has received one of the most substantial sets of updates for the x86...
Troy Hunt, the renowned cybersecurity blogger and creator of the popular service “Have I Been Pwned” (HIBP),...
One of South Africa’s largest agro-industrial corporations, Astral Foods, has confirmed that it fell victim to a...
Credential stuffing remains one of the most prevalent and effective methods of unauthorized access. By leveraging databases...
Signal President Meredith Whittaker came to the defense of the messaging platform following a recent incident involving...
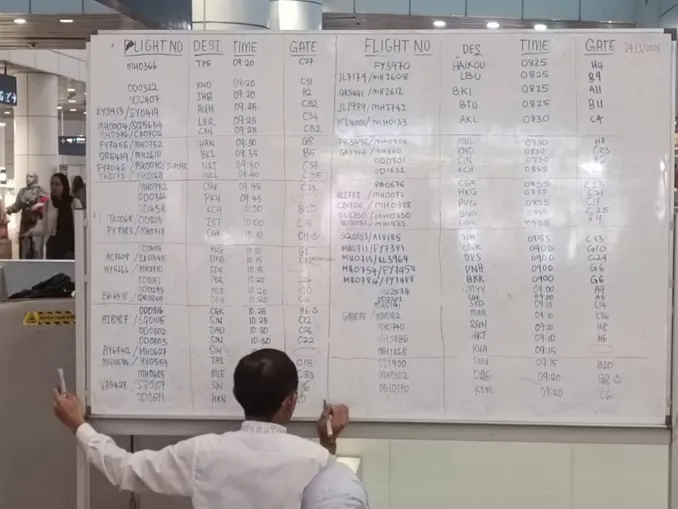
The computer disruptions that afflicted Kuala Lumpur International Airport over the past weekend were the result of...
In early 2025, researchers at Silent Push uncovered a new phishing campaign targeting Counter-Strike 2 players, distinguished...
Cybereason has released a new analytical report examining the operations of the PlayBoy Locker Ransomware-as-a-Service (RaaS) platform....