Microsoft has announced a revision of its previously stated plans to remove the driver synchronization feature from...
The British government has lost its bid to keep secret the details of a surveillance order issued...
The Signalgate scandal, which implicated Jeffrey Goldberg, editor-in-chief of The Atlantic, as a participant in a private...
In the hospitality industry, incidents are increasingly surfacing in which cybercriminals, masquerading as representatives of Booking.com, gain...
Google has released the April Android security update, addressing a total of 62 vulnerabilities, including two zero-day...
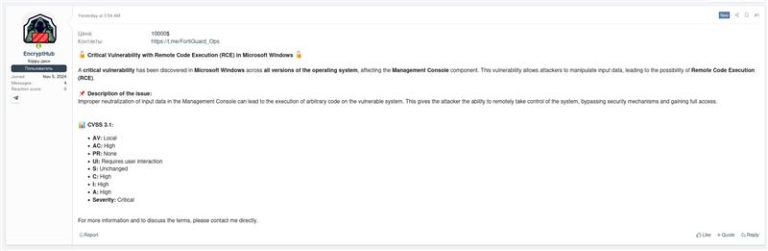
Swedish cybersecurity experts have uncovered an extraordinary tale of a hacker who walks a fine line between...
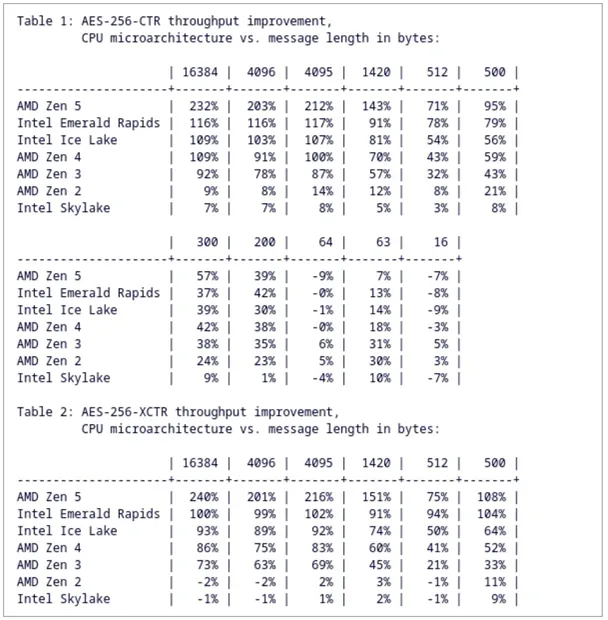
The forthcoming Linux 6.15 kernel is set to introduce significant advancements in the cryptographic subsystem, with particularly...
Previous reports have suggested that Apple’s upgraded Siri digital assistant will be delayed until 2026, which in...
According to Bloomberg journalist Mark Gurman, the upcoming iPhone 17 Pro is expected to retain the design...
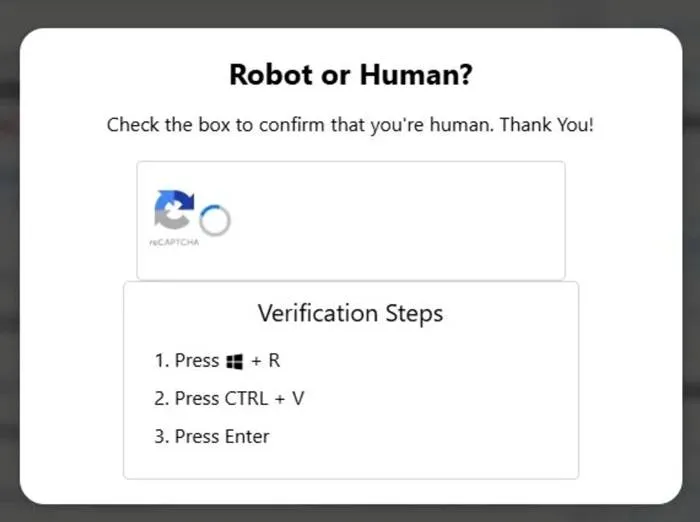
Running Windows on devices for which it was never intended is far from novel—but this time, the...
Amazon has recently unveiled several AI-powered features, including a new function for Kindle e-books called “Recaps,” designed...
The North Korean cyber-espionage group behind the Contagious Interview campaign has once again intensified its activities, extending...
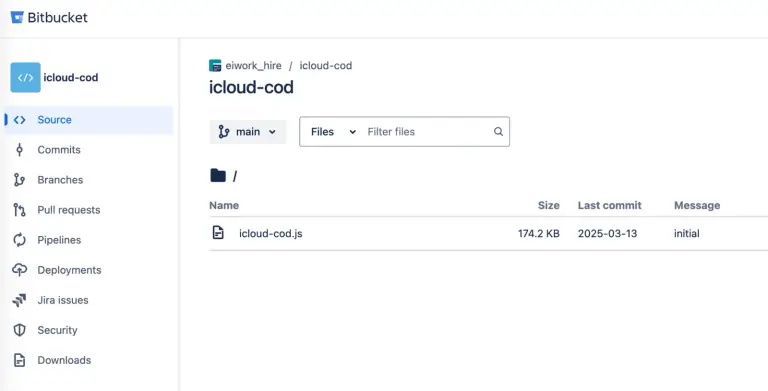
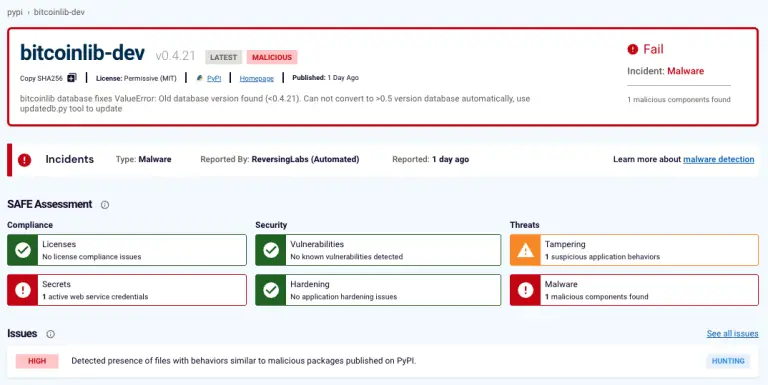
Malicious Python libraries have once again surfaced on the PyPI platform, engineered to steal confidential data and...
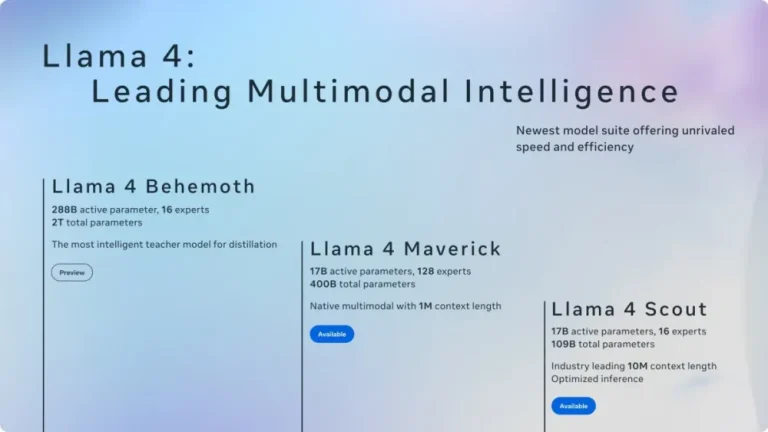
Following the recent announcement that Meta will host its inaugural LlamaCon developer event on April 29 (Pacific...
CUDA is NVIDIA’s proprietary GPU parallel computing architecture—“proprietary” meaning it is not open-source and is solely developed...