Engineers at ByteDance have introduced an innovative approach to accelerating inter-process communication (IPC) in Linux, dubbed RPAL—Run...
An employee of xAI inadvertently published a private API key on GitHub, which, for two months, granted...
Despite the widespread adoption of multi-factor authentication (MFA), cybercriminals have developed increasingly sophisticated techniques to circumvent it....
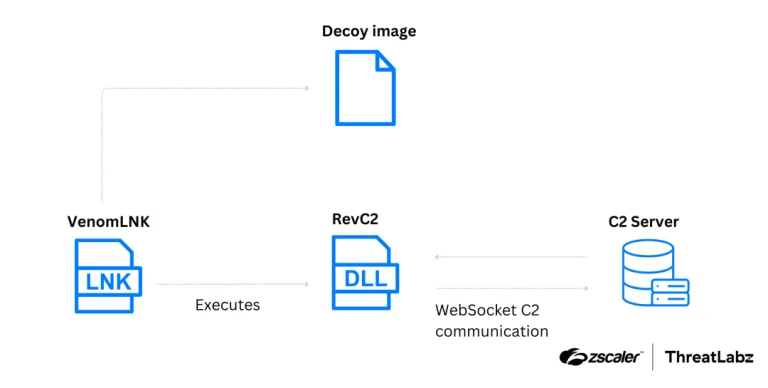
Researchers at Insikt Group have uncovered two new digital tools circulating online, both designed to steal passwords...
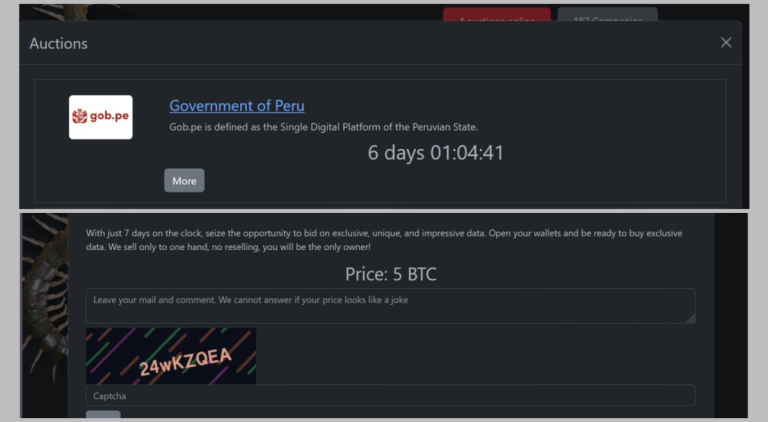
Government systems in Peru have been paralyzed following a large-scale cyberattack claimed by the hacker collective Rhysida,...
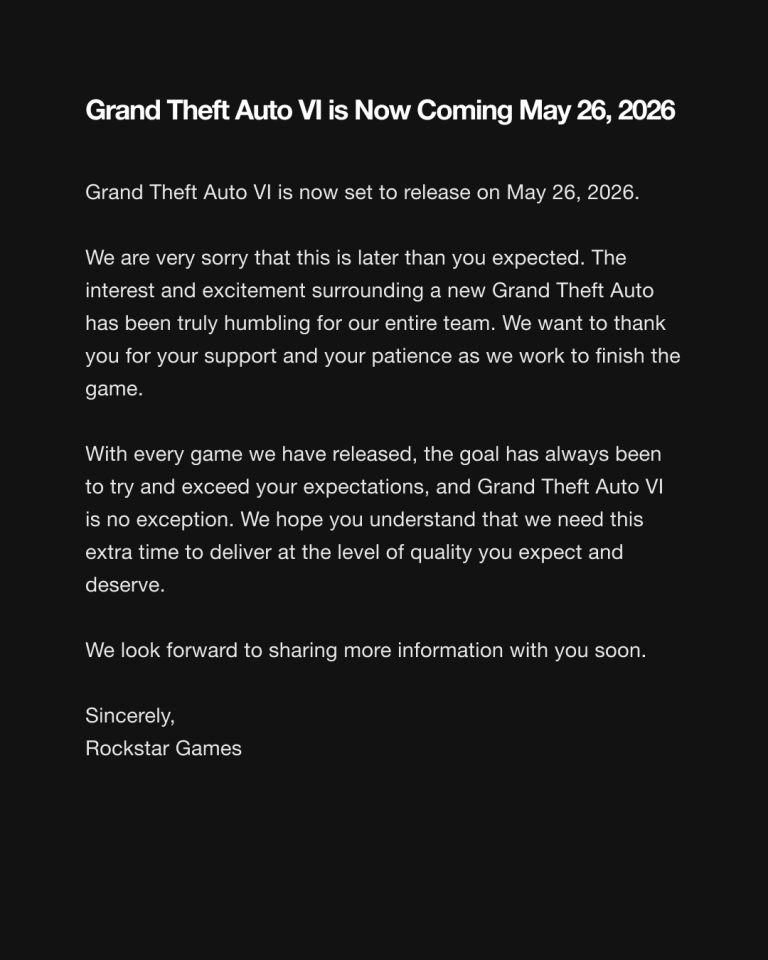
Rockstar Games has officially announced that the highly anticipated Grand Theft Auto VI, originally slated for release...
Qualcomm has released its financial results for the second quarter of fiscal year 2025, reporting revenue of...
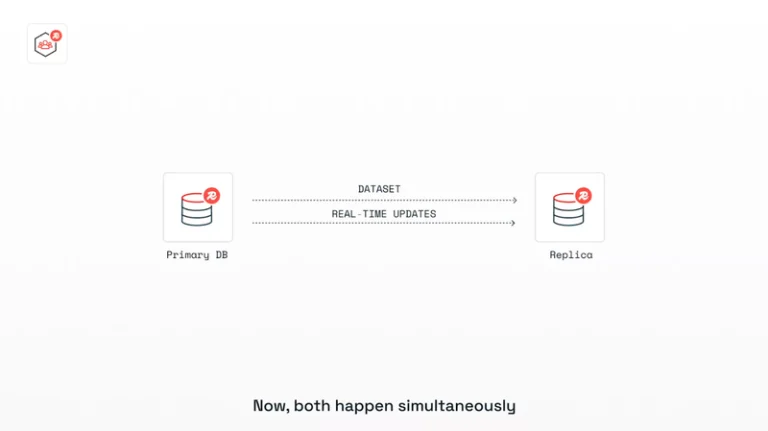
Redis, the company behind the eponymous and widely acclaimed database, has announced its return to an open-source...
Apple has begun issuing alerts regarding targeted attacks involving spyware allegedly procured by state-affiliated entities. According to...
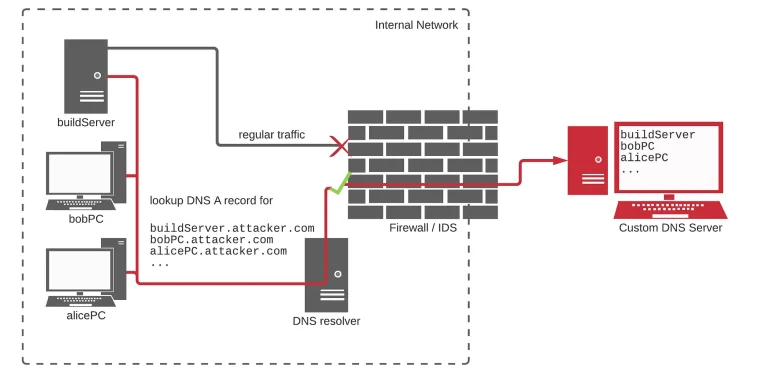
Over the past year, a series of high-profile incidents—including the breaches of Snowflake and the data leak...
AI can generate code—but not always safely. A new study, set to be presented at the 2025...
At the beginning of 2024, a California-based programmer developed a malicious application disguised as an artificial intelligence...
In recent years, account breaches via brute-force attacks have become significantly easier—not solely due to the exponential...
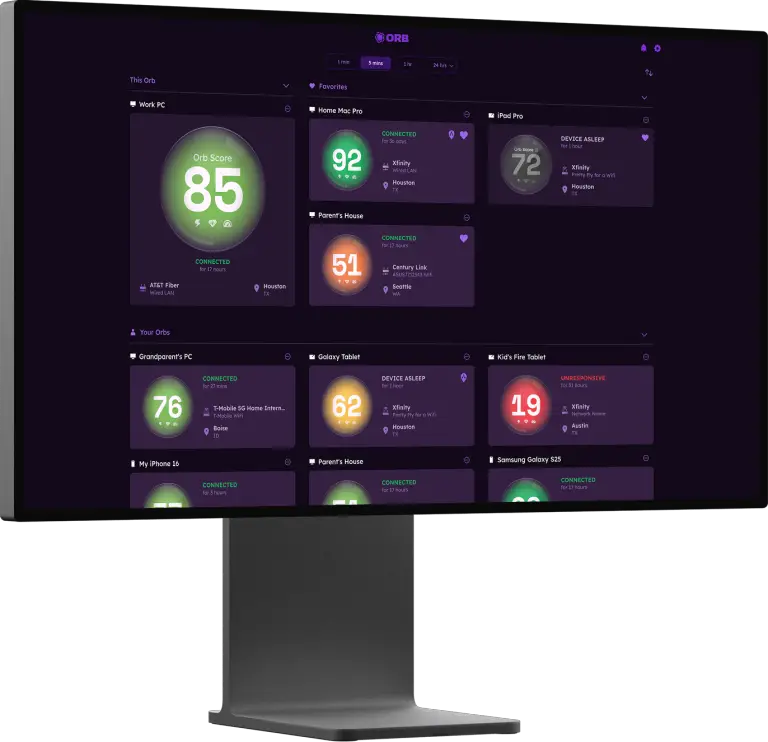
The creator of one of the world’s most widely used internet speed testing services, Speedtest.net, has unveiled...
The enterprise data backup platform Commvault has disclosed a compromise of its Microsoft Azure environment, linked to...