Google has released its latest Android security update, addressing 46 vulnerabilities—one of which is already being actively...
Ransomware attacks targeting the agribusiness sector in 2025 have grown markedly in both scale and intensity, according...
Global performance advertising leader Taboola has announced a new strategic partnership with Samsung, aimed at delivering curated...
The Financial Times, citing informed sources, reports that Huawei is constructing three advanced chip fabrication facilities in...
According to sources cited by The Information, Apple is reportedly planning to revise its iPhone product update...
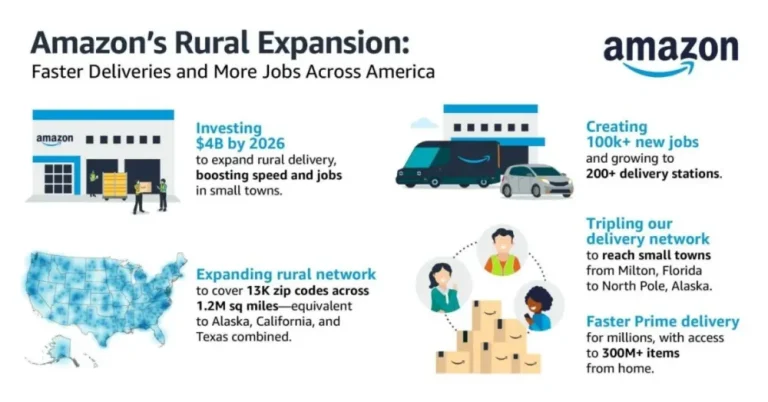
Amazon has announced a $4 billion investment aimed at expanding its delivery infrastructure across rural regions of...
The notion that spam is easily identifiable by clumsy spelling and awkward syntax no longer holds true....
Researcher Zhinyan Peng has released detailed findings and a working proof-of-concept (PoC) exploit for a vulnerability in...
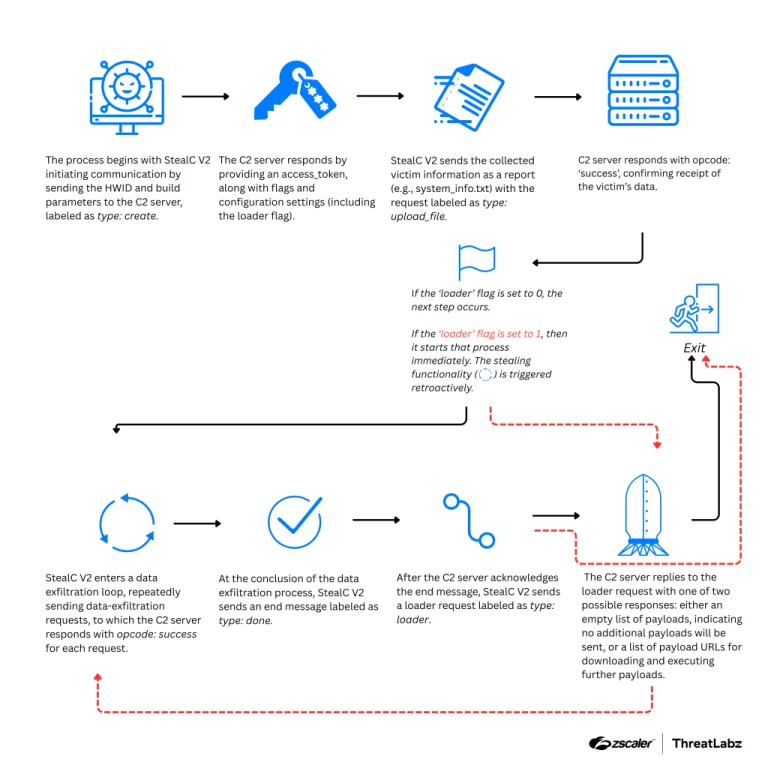
The widely used StealC malware, actively deployed in cyberattacks for data theft and the delivery of secondary...
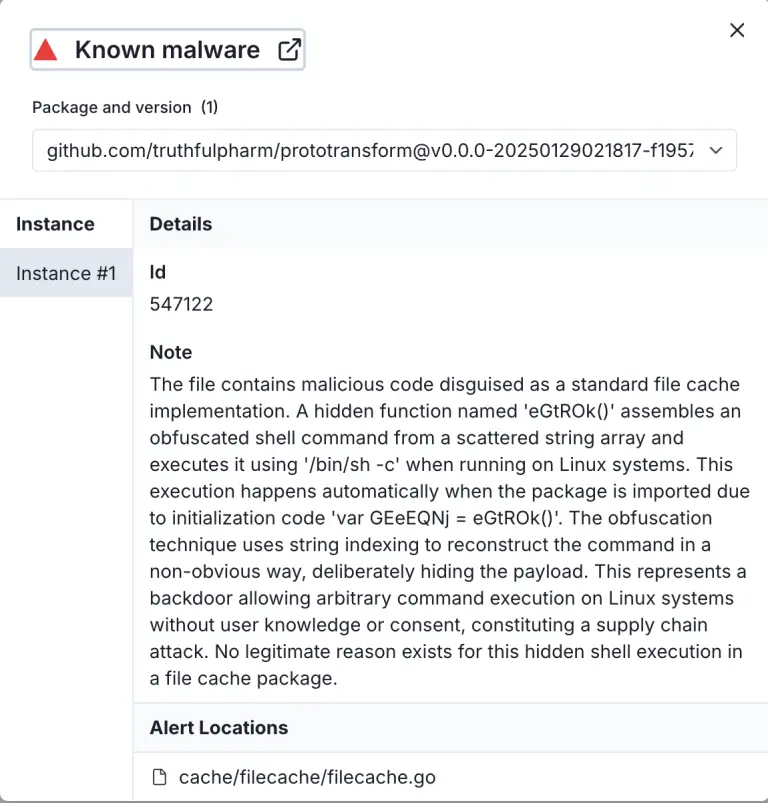
Three malicious components have been discovered within the Go programming module ecosystem, capable of triggering complete data...
The Open Source Lab at Oregon State University (OSU OSL), a vital technical cornerstone for open-source projects...
An AMD engineer continues to advance processor security within Linux by proposing a novel protection management system...
The United States Department of Justice is demanding that Google divest key components of its advertising business...
Apple has begun testing a new programming platform that harnesses artificial intelligence to write, edit, and review...