The developers of the DragonFlyBSD operating system have released version 6.4.2 just one week after the debut...
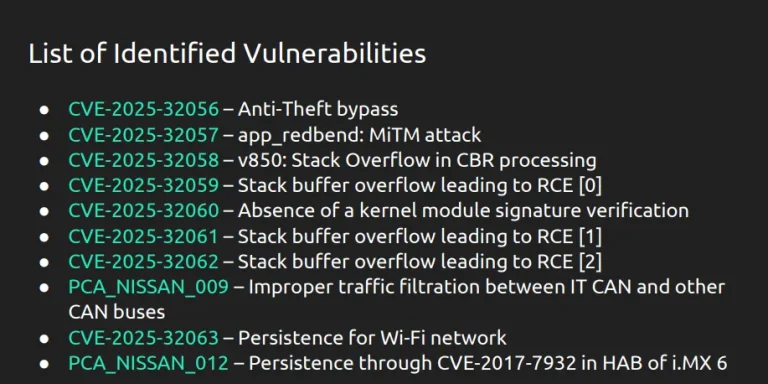
A group of European white-hat hackers from the Budapest-based company PCAutomotive has demonstrated a remote hack of...
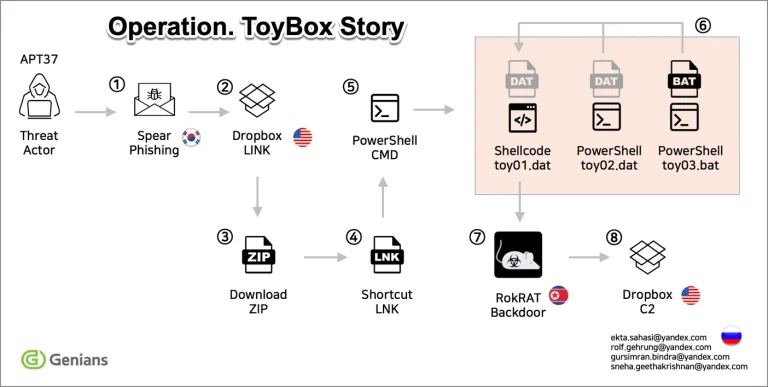
In March 2025, cybersecurity specialists from South Korea’s Genians Security Center uncovered a new operation orchestrated by...
Shelves at the British retail chain Co-op remain partially empty two weeks after a cyberattack disrupted the...
The credentials of an employee affiliated with two prominent U.S. government entities—the Cybersecurity and Infrastructure Security Agency...
Following numerous rumors surrounding the iOS 19 update, Bloomberg journalist Mark Gurman revealed in the latest edition...
According to sources familiar with the matter, Apple is reportedly considering a price adjustment for the upcoming...
Nintendo has recently updated its account usage policy, introducing clauses that grant the company the authority to...
According to a report by Bloomberg News, Meta has appointed former Google DeepMind Research Director Robert Fergus...
When Intel introduced its standalone Xe Max graphics card in 2022, built on the Xe architecture, it...
Researchers at Socket have uncovered a new attack targeting the macOS version of the popular source code...
U.S. Senators Jacky Rosen (D-NV) and Bill Cassidy, M.D. (R-LA) have introduced a bipartisan bill aimed at...
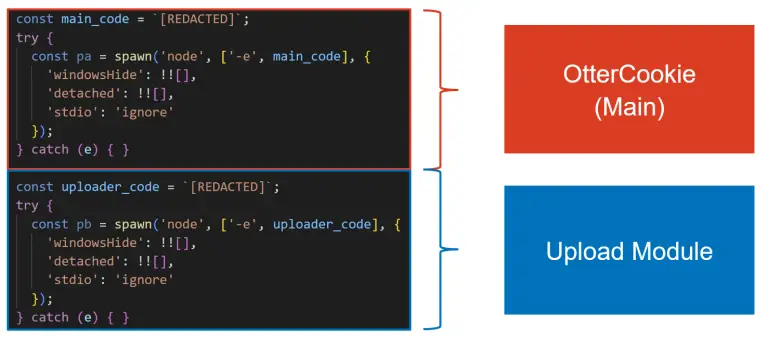
The North Korean cyber-espionage group behind the Contagious Interview campaign continues to evolve its multifunctional malware, OtterCookie—a...
Since the beginning of 2025, Cisco Talos specialists have been tracking a new malicious campaign targeting Portuguese-speaking...
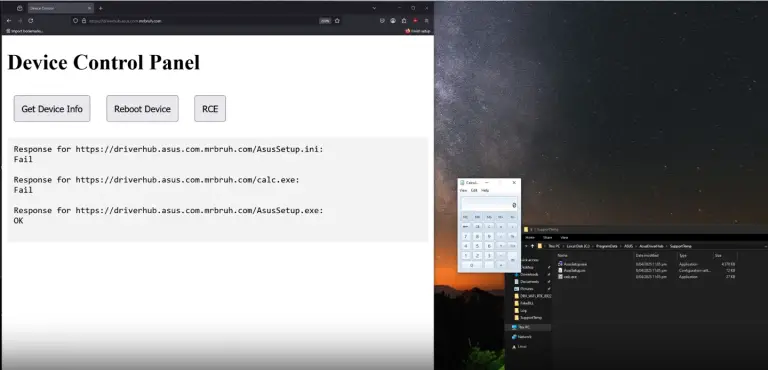
A user who had purchased an ASUS motherboard discovered that the driver installation software—automatically triggered via the...