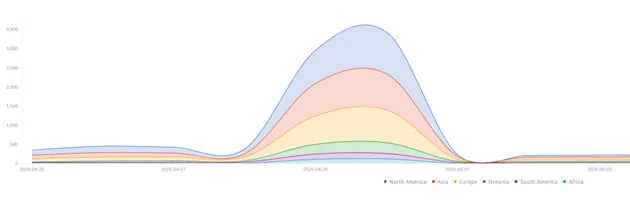
The infamously clandestine marketplace known as Xinbi Guarantee, long serving Chinese-speaking fraudsters and money launderers, has been...
Among the newly announced accessibility features from Apple, one stands out for its groundbreaking potential: a newly...
The attacks targeting SAP NetWeaver servers, initially believed to stem from the exploitation of a single zero-day...
Fortinet has released an urgent security update to address a critical vulnerability affecting its enterprise telephony systems,...
The electronic notification system employed by U.S. federal and local government agencies to inform citizens has been...
The Trump administration has adopted a significantly tougher stance on China’s technological advances, issuing a stark warning...
Microsoft has released its May Patch Tuesday security update, addressing 72 vulnerabilities across its product ecosystem—including five...
Ivanti has issued a warning to its clients regarding two newly discovered vulnerabilities in its Ivanti Endpoint...
According to reports, Perplexity.ai is currently in discussions to secure a new funding round of $500 million,...
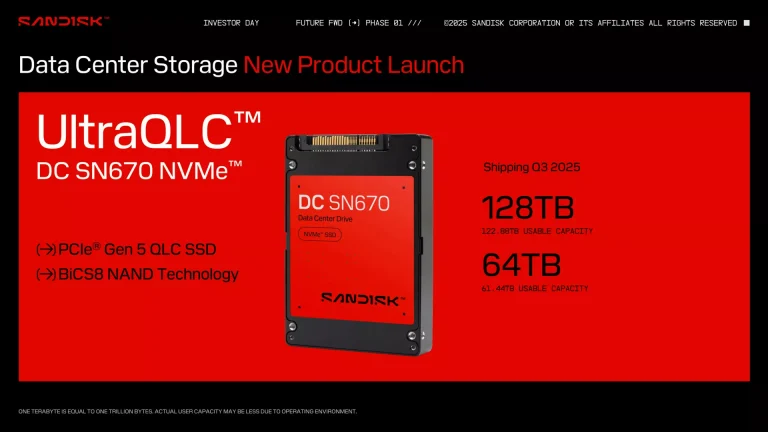
SanDisk, a renowned memory manufacturer, is currently developing a high-capacity solid-state drive (SSD) architecture under the codename...
Kingston has unveiled the new Renegade G5 PCIe 5.0 NVMe M.2 solid-state drive under its Kingston FURY...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has announced that, moving forward, it will publish only...
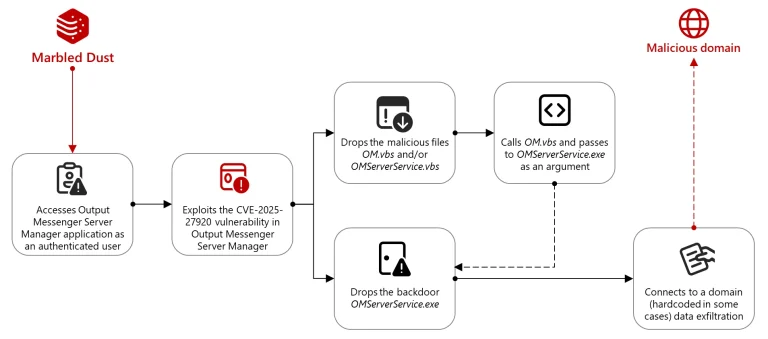
The APT group known as Marbled Dust, believed to be affiliated with the Turkish government, has orchestrated...
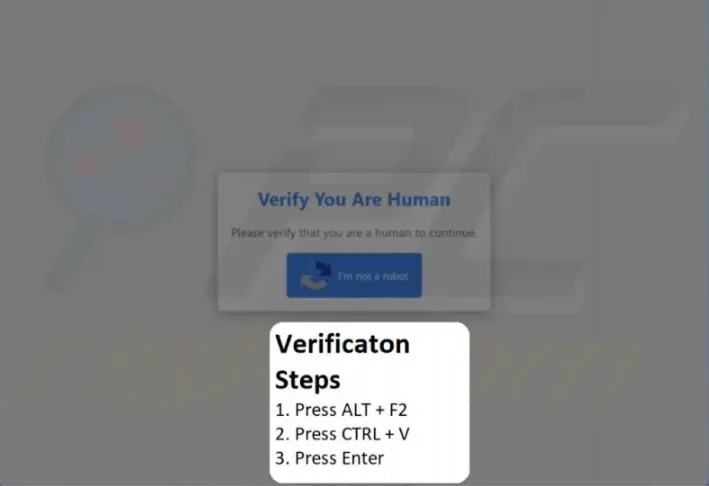
The ClickFix method, rooted in social engineering, has now extended beyond Windows. Researchers at Hunt.io have uncovered...
Google has agreed to pay the state of Texas $1.375 billion in settlement of two lawsuits alleging...