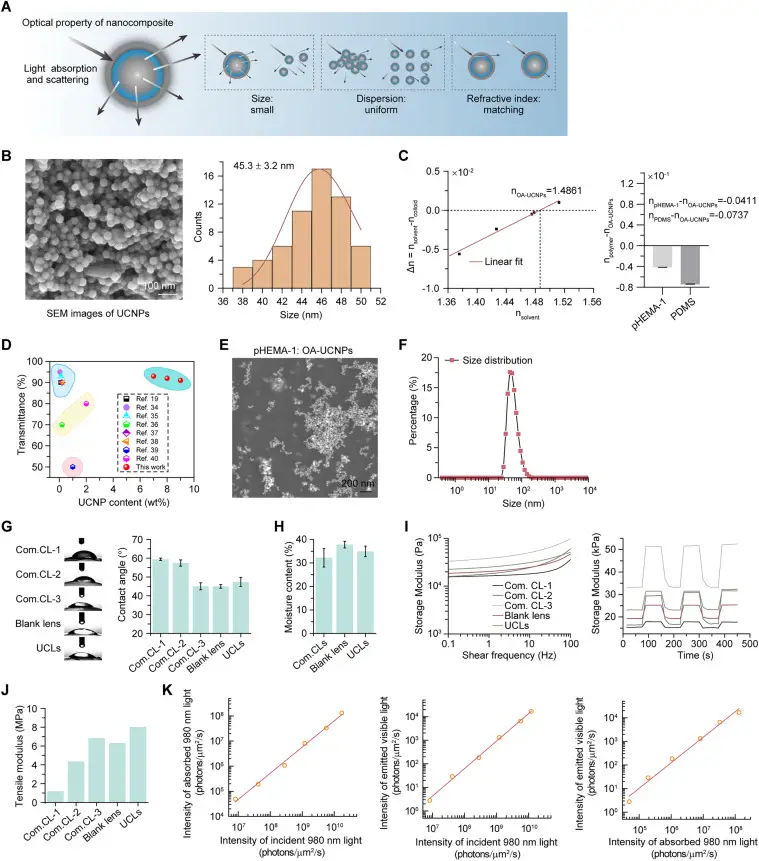
In China, researchers have developed infrared contact lenses that enable vision in complete darkness—even with closed eyes—for...
Google has come under fire from human rights advocates and concerned parents following the launch of a...
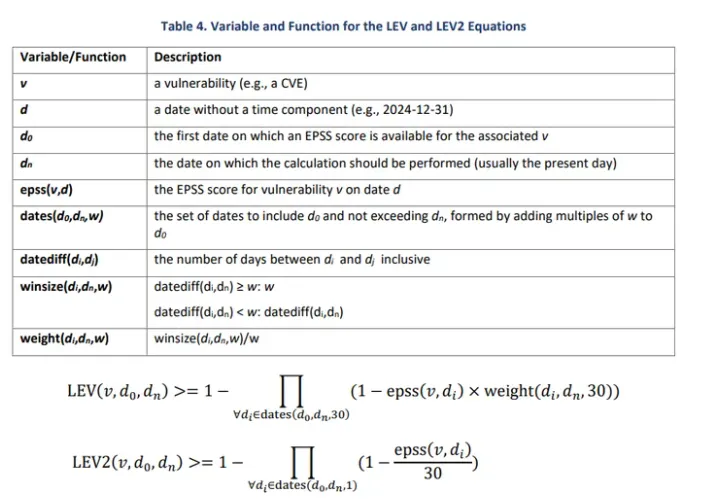
The U.S. National Institute of Standards and Technology (NIST) has introduced a new methodology for assessing the...
The United Kingdom has been shaken by alarming news of a massive data breach affecting millions of...
After the United States Court of Appeals for the Ninth Circuit upheld a previous ruling dismissing the...
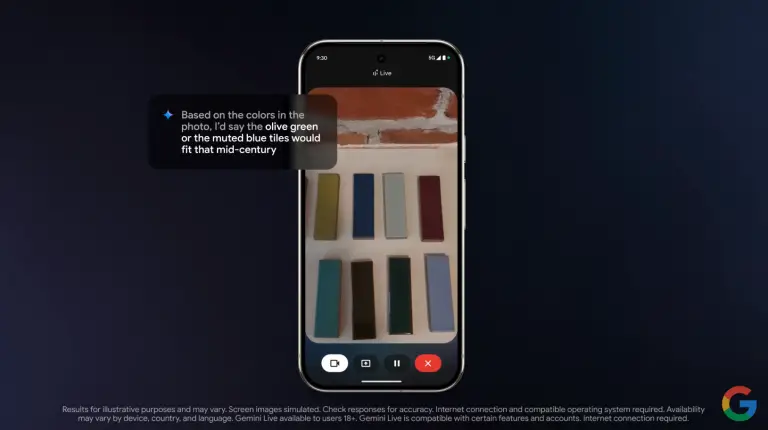
Following Google’s announcement at this year’s Google I/O 2025 that it will launch its “Project Aura” smart...
Following Intel’s recent confirmation of its intention to streamline corporate hierarchy and simplify reporting lines, Reuters has...
Sony recently announced that its PlayStation Stars rewards program, launched in July 2022, will be officially discontinued...
OpenAI has announced the acquisition of the design startup “io,” co-founded by former Apple Chief Design Officer...
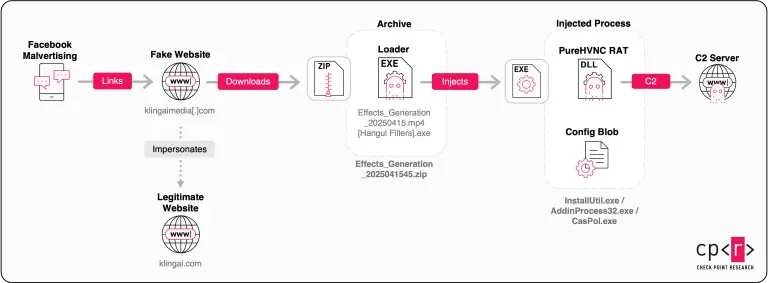
The soaring popularity of Kling AI, a platform capable of generating images and videos from text and...
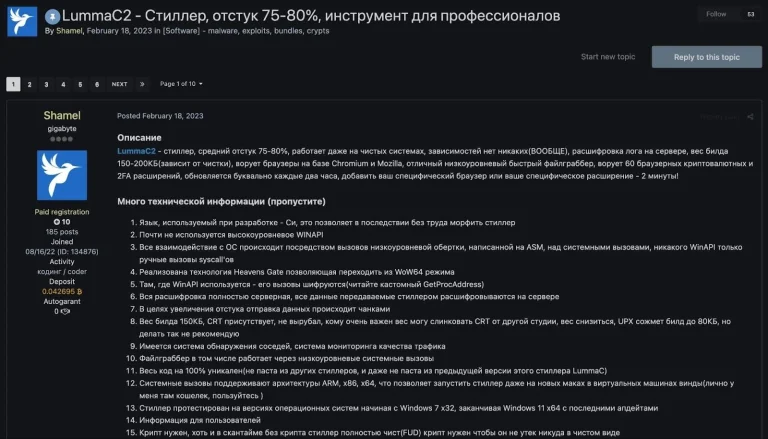
In the first half of May 2025, an international operation aimed at dismantling the infrastructure of Lumma...
Marks & Spencer (M&S), one of the United Kingdom’s largest retail giants, has announced an anticipated decline...
A new malicious campaign targeting containerized infrastructures is spreading rapidly across the globe, transforming compromised containers into...
The legendary Japanese film studio Toho, recently honored with an Academy Award for visual effects in Godzilla...
Subscribers of Cellcom—a telecommunications provider serving users across Wisconsin and Michigan’s Upper Peninsula—were left without service for...