Oracle has reportedly notified select clients of a data breach involving its public cloud infrastructure, reversing its earlier denial of any such incident. This revelation was brought to light by The Register, citing sources familiar with the matter.
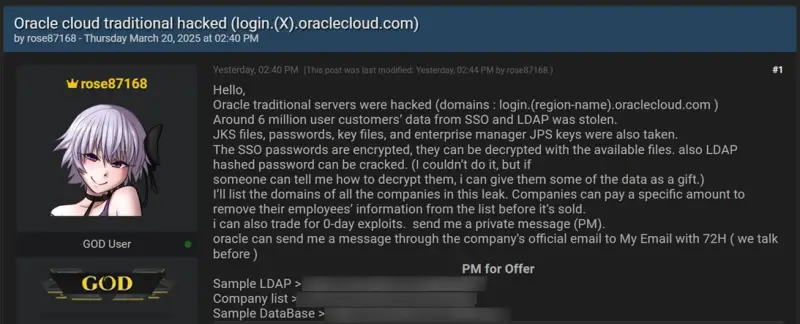
Initial reports of the cyberattack surfaced in late March, when a forum user going by the handle “rose87168” claimed to have breached two Oracle customer authentication servers, gaining access to approximately six million records. The stolen data allegedly included private keys, encrypted credentials, and LDAP entries. According to the threat actor, the information pertained to thousands of organizations and had been offered for sale.
At first, Oracle dismissed these allegations as unfounded. However, subsequent analysis by cybersecurity researchers of the leaked data samples confirmed a compromise of Oracle Cloud Classic. It is believed the attacker exploited CVE-2021-35587 (CVSS score: 9.8), a critical vulnerability in Oracle Access Manager—part of the Oracle Fusion Middleware suite—which had remained unpatched on Oracle’s own servers.
Further corroborating the breach, the attacker reportedly left behind a text file containing their email address on one of the login servers at login.us2.oraclecloud.com as early as March, providing additional evidence of unauthorized access.
To date, at least two Oracle clients have confirmed that the company has reached out to discuss the breach and its implications. While cybersecurity firm CrowdStrike has been enlisted to assist with the investigation, it has declined to comment, referring inquiries back to Oracle. The FBI is also reportedly looking into the matter.
According to Bloomberg, Oracle privately informed customers that the breach involved an outdated server containing data from eight years ago, and that the stolen credentials were no longer valid. However, one affected client contended that the compromised information included records that were still relevant as of 2024.
In light of the incident, a lawsuit has been filed against Oracle in Texas. The legal proceedings are expected to shed further light on the circumstances of the breach. Notably, the attack is said to be unrelated to a separate incident involving Oracle Health, for which the company has yet to issue a public statement.
The breach also raises serious questions regarding Oracle’s compliance with the EU’s General Data Protection Regulation (GDPR), which mandates disclosure of personal data leaks within 72 hours. Failure to meet this requirement could expose the company to fines of up to 4% of its global annual revenue.
Although the United States lacks a federal data breach notification law, several states have enacted regulations requiring prompt disclosure. Additionally, if Oracle Health systems were compromised, the incident could trigger penalties under the Health Insurance Portability and Accountability Act (HIPAA). Legal experts are reportedly exploring the possibility of filing class action lawsuits on behalf of affected parties.


