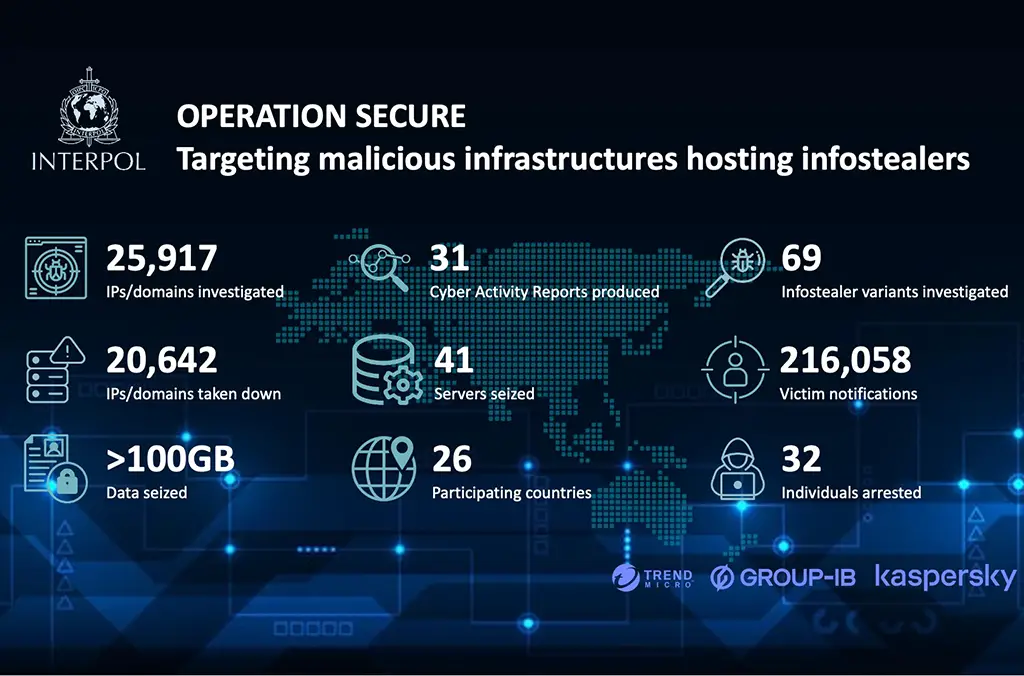
An international law enforcement operation, codenamed Operation Secure, has culminated in the large-scale dismantling of cybercriminal infrastructure used to deploy data-stealing malware. Interpol officially announced that the crackdown targeted over 20,000 malicious IP addresses and domains linked to 69 distinct families of information-stealing malware.
The coordinated effort, which spanned from January to April 2025, involved authorities from 26 countries, including Vietnam, India, Japan, Singapore, South Korea, and other nations within the Asia-Pacific region. Investigators identified command-and-control servers, analyzed physical network infrastructure, and carried out precision takedowns of malicious nodes.
As a result, 79% of the identified suspicious IP addresses were neutralized, 41 servers were seized, over 100 gigabytes of data were confiscated, and 32 individuals suspected of cybercriminal involvement were detained. The most significant impact was delivered by Vietnamese law enforcement, who arrested 18 suspects and seized electronic devices, SIM cards, business registration documents, and approximately $11,500 in cash. Additional raids in Sri Lanka led to the arrest of 12 individuals, while two more were apprehended in Nauru.
Hong Kong police played an especially prominent role, uncovering 117 command-and-control servers hosted across 89 internet service providers. These servers were reportedly used to coordinate phishing campaigns, conduct online fraud, and disseminate malware through social media platforms.
According to Interpol, participating agencies also included those from Brunei, Cambodia, Fiji, Indonesia, Kazakhstan, Kiribati, Laos, Macau, Malaysia, the Maldives, Nepal, Papua New Guinea, the Philippines, Samoa, the Solomon Islands, Thailand, Timor-Leste, Tonga, and Vanuatu.
The dismantled infrastructure had supported malware designed to harvest sensitive data from infected devices. Such malware is often offered as a subscription-based service on the dark web. These tools enable the extraction of login credentials, cookies, credit card details, and cryptocurrency wallet information.
The stolen data is then sold as “logs” on underground cyber forums and serves as the foundation for further attacks, including extortion, business email compromise, and infiltration of corporate networks. This methodology remains one of the most favored among cybercriminals seeking swift access to confidential information.
A key partner in the operation was Singapore-based cybersecurity firm Group-IB, which provided vital intelligence on compromised accounts affected by malware strains such as Lumma, RisePro, and Meta Stealer. According to CEO Dmitry Volkov, this type of data is often the launchpad for further fraudulent activity and ransomware-driven assaults.
The operation follows just weeks after a similar global takedown that saw the seizure of more than 2,300 domains linked to Lumma Stealer. Initiatives like these are becoming increasingly critical tools in the global fight against the escalating threat posed by the digital criminal underworld.


